The GPResult.exe command-line tool is used to get a Resultant Set of Policy (RSoP) that is applied to a user and/or computer in an Active Directory domain. GPResult allows you to display a list of domain policies (GPOs) that are applied to the computer and user, policy settings, GPO processing time and errors. It is the most commonly used administrator tool for analyzing settings and troubleshooting Group Policy issues in Windows.
In this article, we’ll take a look at how to use the GPResult command to diagnose, debug, and analyze Group Policy settings applied to Windows in an Active Directory domain.
- How to Use the Group Policy Results (GPResult.exe) Command?
- Exporting RSoP Report to HTML with GPResult
- GPResult: Getting RSOP Data from a Remote Computer
- GPResult: The User Does Not Have RSoP Data
- The following GPOs Were Not Applied Because They Were Filtered Out
- Resultant Set of Policies (RSOP.msc) Snap-in in Windows
How to Use the Group Policy Results (GPResult.exe) Command?
You must run the GPResult command on the computer on which you want to check the application of Group Policy. The syntax for GPResult is:
GPRESULT [/S system [/U username [/P [password]]]] [/SCOPE scope] [/USER targetusername] [/R | /V | /Z] [(/X | /H) <filename> [/F]]
To get detailed information about the Group Policies applied to a specific user or computer, as well as other settings related to the GPO infrastructure (the resulting GPO policy settings, RsoP), open the command prompt and run this command:
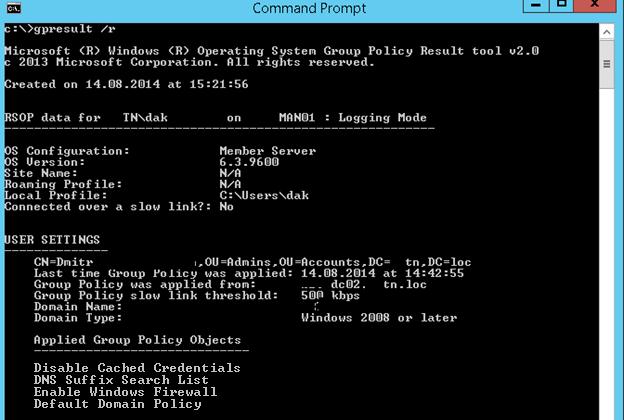
Gpresult /r
The results of this command are divided into two sections:
- COMPUTER SETTINGS – the section contains the information on the GP objects applied to the computer (as an Active Directory object);
- USER SETTINGS – this is a user policy section (the policies applied to the account of the AD user).
Let’s briefly cover the basic settings/sections in the GPResult output that can be of interest for administrators:
- Site Name – is the name of the AD site where the computer is located;
- CN – full canonical user/computer name for which RSoP data was generated;
- Last time Group Policy was applied – is the time when the Group Policy settings were last applied (updated);
- Group Policy was applied from – is the domain controller name from which last GPO versions has been downloaded;
- Domain Name and Domain Type – is the name and the version number of the Active Directory domain schema;
- Applied Group Policy Objects – are the lists of applied GPOs;
- The following GPOs were not applied because they were filtered out
- The user is a part of the following security groups – a list of domain security groups the user is a member of.
In this example, you can see that 4 Group Policies are applied to the user object.
- Disable Cached Credentials
- DNS Suffix Search List;
- Enable Windows Firewall;
- Default Domain Policy.
The report will also contain information about local policy settings configured through the Local Group Policy Editor (gpedit.msc).
You can use the /scope option to display only user or computer policies:
gpresult /r /scope:user
or only applied computer policies:
gpresult /r /scope:computer
gpresult /r /scope:computerERROR: Access Denied.
For the convenience of parsing and analyzing RSOP data, you can redirect the Gpresult results to the clipboard:
Gpresult /r |clip
or a text file:
Gpresult /r > c:\ps\gpresult.txt
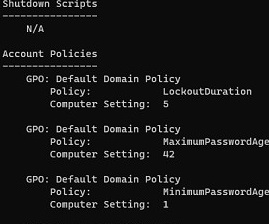
To display more detailed RSoP information, you need to add the /z key:
Gpresult /r /z
For example, the screenshot shows the domain password policy settings that are applied to the computer.
Exporting RSoP Report to HTML with GPResult
GPResult allows you to generate an HTML report on the applied resultant policies (available in Windows 7 and newer). This report contains detailed information on all system settings that are set by the Group Policies and the names of the GPOs that have set them. The gpresult HTML report is structurally similar to the Settings tab in the Group Policy Management Console (gpmc.msc). You can generate the RSoP HTML report using the following gpresult command:
GPResult /h c:\PS\gpo-report.html /f
%WINDIR%\system32 folder.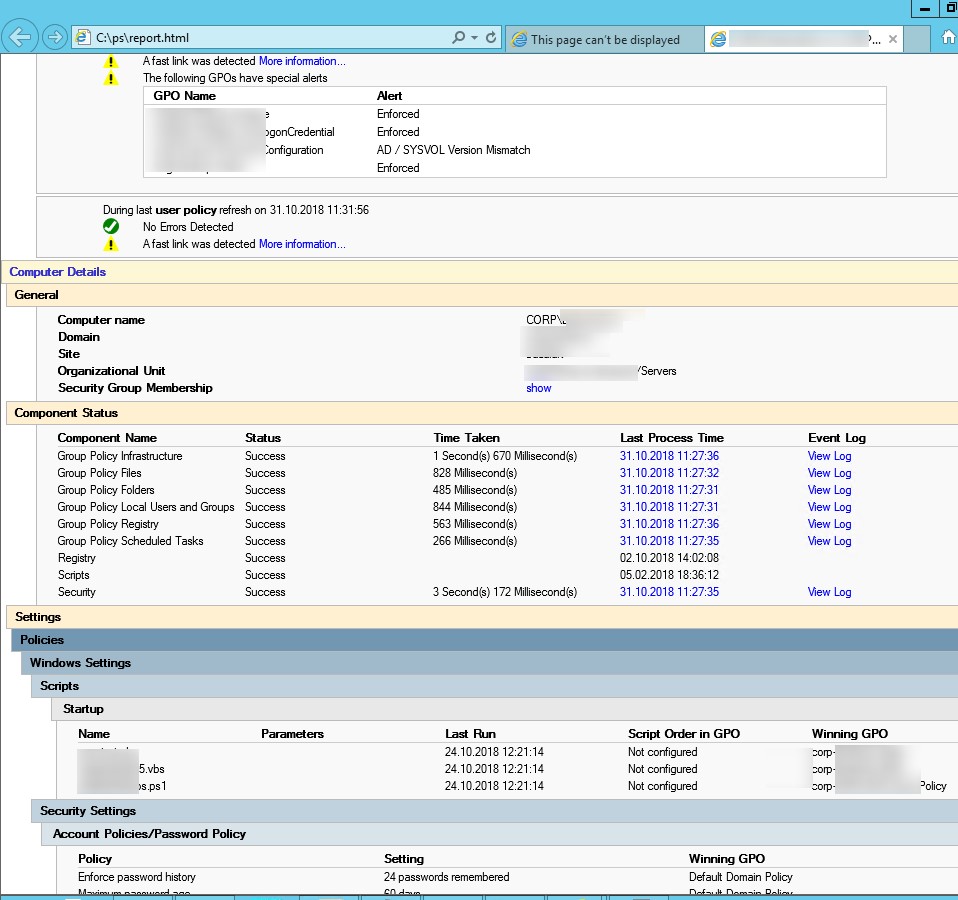
To generate the report and automatically open it in a browser, run the following command:
GPResult /h GPResult.html & GPResult.html
The gpresult HTML report contains quite a lot of useful information: you can see GPOs applying errors, processing time (in ms) for a specific policy and CSEs (in the Computer Details -> Component Status section). This is useful when you need to understand why GPO processing takes a long time.
For example, in the screenshot above you can see that the Enforce password history policy with the settings “24 passwords remembered” is applied by the Default Domain Policy (Winning GPO column).
An HTML report allows you to present the resulting set of computer GPOs in a convenient graphical form.
GPResult: Getting RSOP Data from a Remote Computer
GPResult can get a resultant set of policies from a remote computer as well with no need to log locally or via the RDP on to the remote device.
GPResult /s remote-pc-name1 /r
You can specify a username and password to connect to a remote computer using the gpresult options:
gpresult /R /S wks2b21c /scope user /U corp\jsmith /P myPaSSw0rd1!
If you don’t want your password to be saved in the PowerShell command history, you can prompt for the password interactively:
gpresult /R /S wks2b21c /scope user /U corp\jsmith /P
Similarly, you can remotely collect data on both user and computer policies.
If you don’t know the name of a user who is logged on to a remote computer, you can get a username like this:
qwinsta /SERVER:wks2b21c
Get-GPResultantSetOfPolicy -user jsmith -computer corp\wks2b21c -reporttype html -path c:\ps\gpo_rsop_report.html
GPResult: The User Does Not Have RSoP Data
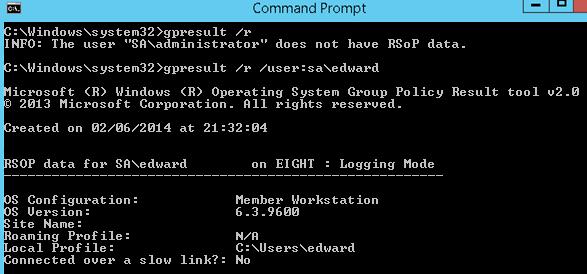
When the UAC is enabled and GPResult is used in non-elevated mode, only the user settings section of the Group Policies is shown. If you need both sections (USER SETTINGS and COMPUTER SETTINGS) to be displayed, the command must be running in the command prompt with the administrator privileges.
If an elevated command prompt is run on behalf of an account that is different from the current user, the tool will show the warning: INFO: The user “domain\user” does not have RSOP data. This happens since GPResult tries to collect the data of the user that has started it, but because this user has not logged in, there is no RSOP information for him. To collect RSOP information for a user with an active session, you need to specify his account:
gpresult /r /user:corp\edward
Also, check the time (and timezone) on the client. The time must match the time on the domain controller running the FSMO PDC role (Primary Domain Controller).
The following GPOs Were Not Applied Because They Were Filtered Out
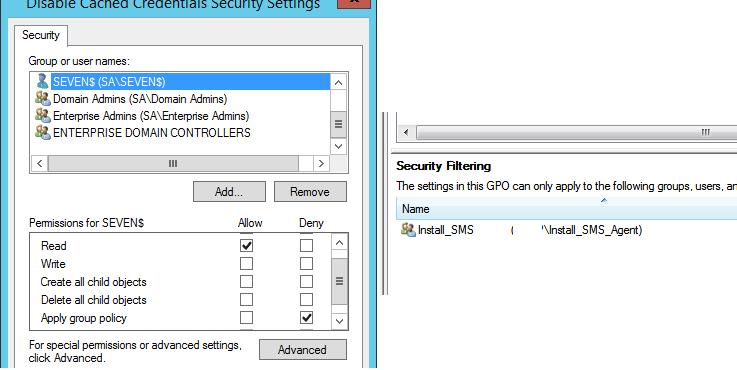
When troubleshooting the applied Group Policies, it’s worth paying attention to the section: The following GPOs were not applied because they were filtered out. It contains the list of the GPOs that are not applied to this object for any reason. Here are some reasons why the GPOsare not applied to a specific Active Directory object:
- Filtering: Not Applied (Empty) – the policy is empty (there is nothing to apply);
- Filtering: Denied (Unknown Reason) – a user/computer is likely to have no permission to read/apply this policy. The permissions can be configured in the Security tab of the Group Policy Management Console (
gpmc.msc); - Filtering: Denied (Security) — an explicit denial is specified in the section Apply Group Policy, or an AD object is not in the list of groups in the Security Filtering section of the GPO.
You can also see if a GPO should be applied to an organizational unit (OU) in AD or to a specific object on the effective permissions tab (Advanced -> Effective Access) in the GPMC.
Resultant Set of Policies (RSOP.msc) Snap-in in Windows
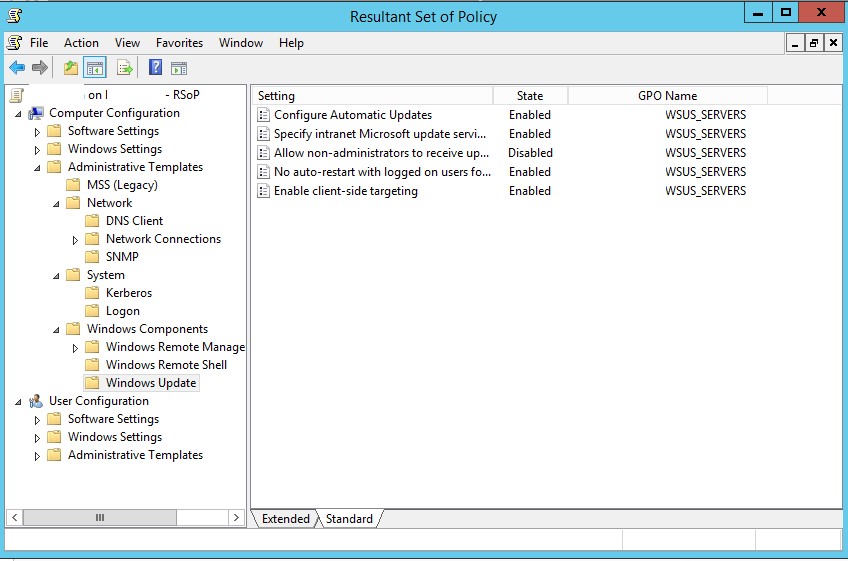
Initially, the graphical console RSOP.msc was used to diagnose applied Group Policies in Windows. This mmc snap-in allows you to get the settings of the resulting policies (domain + local) applied to the computer and the user in a graphical form that is similar to the GPO editor console. The RSOP.msc console on the screenshot below shows that the Windows update settings are configured by the WSUS_SERVERS policy.
You cannot use the RSOP.msc to fully analyze the applied GPOs in modern Windows versions. It doesn’t show settings applied through Client Side Extensions (CSE), such as GPP (Group Policy Preferences), doesn’t allow searches, and provides little diagnostic information. When running rsop.msc on Windows 10 and 11, there was a warning that you should use gpresult to get a full GPO report.
Starting with Vista, the Resultant Set of Policies (RSoP) report does not show all Microsoft Group Policy settings. To see the full set of Microsoft Group Policy settings applied for a computer or user, use the command-line tool gpresult.
In this article, we looked at how to use the GPResult command to analyze the resultant Group Policies that are applied in Windows. In addition, the following guide may be helpful for troubleshooting GPOs in a domain: “Common issues that prevent Group Policy from being applied to clients”.
3 comments
Hi,
Lately i encountered a strange issue pertaining GPO. Out of sudden the GPO use to read from group member stop working. GPresult shows unknown reason. In fact in the same days, a few of my client setup were encountered the same issue (all same symptoms). However, if added with authenticated user account, the gpo will work.
Hi,
Your problems are related with the bulletin MS16-072 ( update KB3159398).
It appears to be an issue with where a group policy has used an Active Directory Security group in the Security Filtering section.
Read the following thread : https://social.technet.microsoft.com/Forums/en-US/e2ebead9-b30d-4789-a151-5c7783dbbe34/patch-tuesday-kb3159398?forum=winserverGP
Do you know if GPRESULT /r /scope computer tries to contact a domain controller at all or if it stays 100% local?