When a domain user logs on to Windows, their credentials are saved on a local computer by default (Cached Credentials: a user name and a password hash). This allows the user to logon to the computer even if the AD domain controllers are unavailable, powered off, or the network cable is unplugged from the computer. Domain account credentials caching is convenient for laptop users who can access their local data on a device when the corporate network is not available.
Caching Domain User Credentials on Windows
Cached credentials may be used to logon to Windows if a user has authenticated on this computer at least once and their domain password has not been changed since then. User password in cashed credentials never expires. If the domain password policy forces a user change the password, the saved password in the local cache won’t change until the user logs on with a new password. If the user password in AD has been changed after the last logon to the computer and the computer has been offline (without access to the domain network), the user will be able to login computer with the old password.
If the Active Directory domain is not available, Windows checks if the entered username and password match the local cache and allows local logon to the computer.
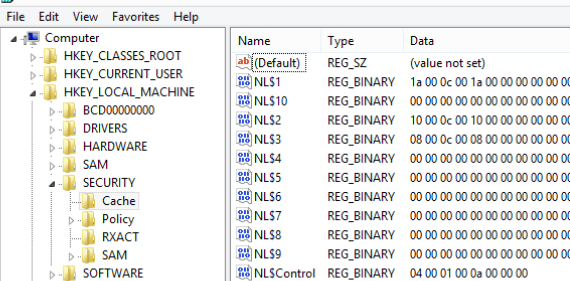
Cached credentials are stored in the registry under the reg key HKEY_LOCAL_MACHINE\Security\Cache (%systemroot%\System32\config\SECURITY). Each saved hash is stored in the NL$x parameter (where x is a cached data index). By default, even an administrator cannot view the contents of this registry key, but you can get access if needed.
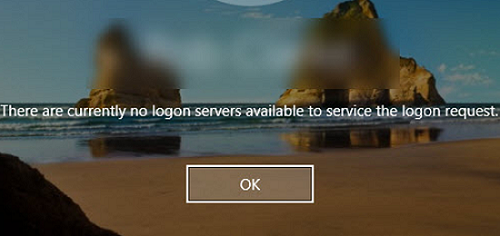
If there are no cached credentials in the local cache, you will see the following message when you try to log on to an offline computer:
There are currently no logon servers available to service the logon request.
Configuring Cached Credentials with Group Policy
You can set the number of unique users, whose credentials may be saved in the local cache on the domain computers with the Group Policy option. For user credentials to be stored in the local cache, the user must log on to the computer at least once.
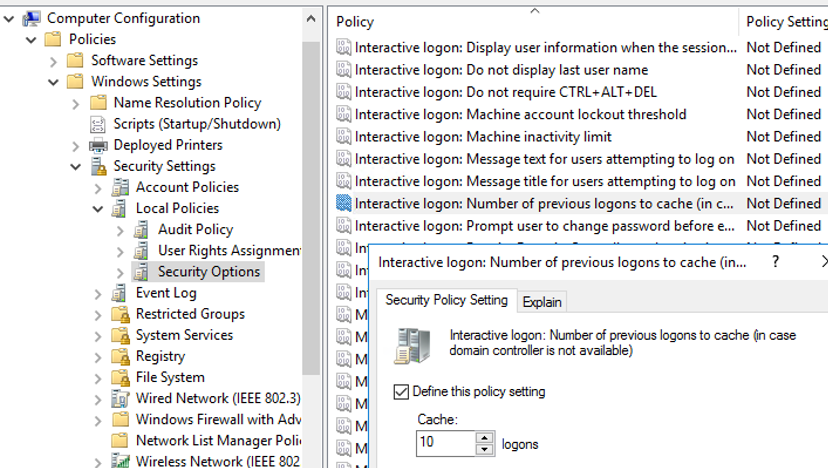
By default, Windows 10 and Windows Server 2016 stores credentials of 10 recently logged users. You can change this value with the following GPO option – Interactive logon: Number of previous logons to cache (in case domain controller is not available). You can find it in Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options. You can set any value from 0 to 50.
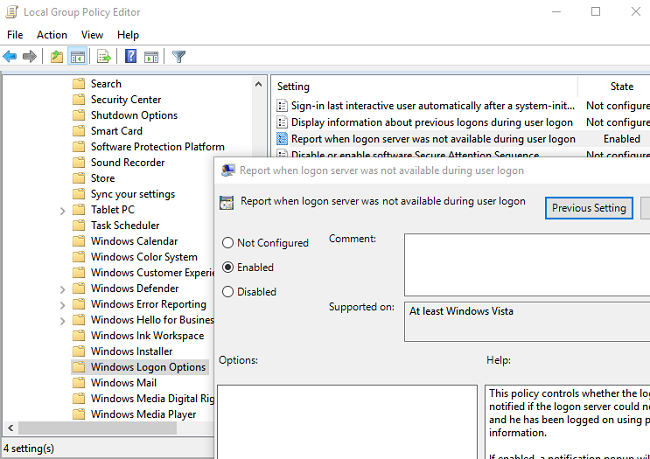
There are currently no logon servers available to service the logon request.HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon.If a user logs on with the saved credentials, they don’t see that the domain controller is not available. Using GPO, you can display a notification of using cached credentials to log on. To do it, enable the GPO option Report when logon server was not available during user logon policy under the Computer configuration -> Policies -> Administrative templates -> Windows Components -> Windows Logon Options.
Then the following notification will appear in the tray after a user logon:
A domain controller for your domain could not be contacted. You have been logged on using cached account information. Changes to your profile since you last logged on might not be available.
HKEY_LOCAL_MACHINE/SOFTWARE/Microsoft/Windows NT/Current Version/Winlogon
- ValueName:
ReportControllerMissing - Data Type:
REG_SZ - Value:
1
Security Risks of Cached Windows Credentials
Local credential caching has some security risks. After getting a physical access to a computer/laptop with the cached data, an attacker can decrypt your password hash using a brute-force attack. It depends on the length and complexity of the password. If a password is complicated, it takes a huge amount of time to brute the password. So it is not recommended to use caching for users with local administrator permissions (or, moreover, domain admin account).
To mitigate security risks, you can disable credential caching on office and administrator computers. It is recommended to reduce the number of cached accounts on mobile devices to 1. It means that even if an administrator has logged on to a computer and their data have been cached, the password hash of the administrator will be overwritten after the device owner logs on.
For AD domains with functional level Windows Server 2012 R2 or newer, you can add domain administrator accounts to the Protected Users group. Local credential caching is prohibited for this security group.
You can create separate GPOs in your domain to control the use of cached credentials for different devices and user categories (for example, using GPO Security filters, WMI filters, or deploying the CashedLogonsCount registry parameter using GPP Item level targeting).
- For mobile (laptop) users:
CashedLogonsCount = 1 - For office desktops:
CashedLogonsCount = 0
Such policies will reduce the chance of getting privileged user hashes from the domain joined devices.
4 comments
Does this also affect RDP?
What are the differences client/server-side?
Thx!
Lovely guide like always!!
many thanks
Thanks for the guide. Great post
Additionally:
1.) to read the NLS$ entries you need SYSTEM rights, so you are already in god mode, Hacking Admins as Admin is not a hack, you alerady own the system
2.) thinking about utilman.exe/sethc.exe and all other attacks against the offline system: get back to 1.) you do not need cached credentials, you alerady own the system
3.) You own the system, you can disable AV/EDR and run keyloggers waiting for someone logging on as member of the protectect user group
Kudos to Paula: Cached Credentials: Important Facts That You Cannot Miss
https://cqureacademy.com/blog/windows-internals/cached-credentials-important-facts