In one of the previous articles we have described the installation of a WSUS server on Windows Server 2012 R2 / 2016 in details. After you have configured the update server, you need to configure Windows clients (server and workstations) in order to use the WSUS server to receive updates. Thus, all Windows clients on your network should receive updates from the internal update server, and not from Microsoft Update servers via the Internet. In this article, we will take a look on how to configure clients to use a WSUS server using Active Directory domain group policies (GPO).
AD Group Policies allow the administrator to automatically assign computers to different WSUS groups, thus the WSUS administrator won’t have to manually move computers between groups in the WSUS console and keep these groups up-to-date. Assigning clients to different target WSUS groups is based on a label in the registry on the client (labels are set by a GPO or a direct registry modification). This type of client assigning to the WSUS groups is called client side targeting.
It is expected that our network will use two different update policies: separate update policy for Servers and another one for Workstations. These two groups need to be created in the WSUS console in the All Computers section.
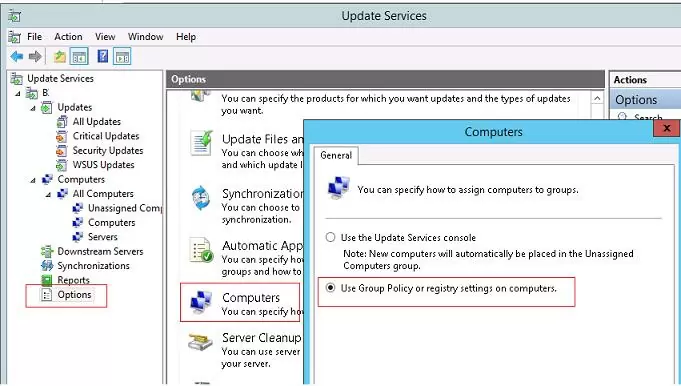
First of all, you have to specify the rule of grouping the computers in the WSUS console (targeting). By default, the computers in the WSUS console are distributed into groups manually by the server administrator (server-side targeting). It does not suit us, so we are going to specify that the computers are to be distributed into groups using the client side targeting (using the group policies or registry parameters). To do this, in the WSUS console click Options and open Computers. Change the value to “Use Group Policy or registry settings on computers”.
Now you can create a GPO to configure WSUS clients. Open the Group Policy Management (GPMC.msc) and create two new group policies: ServerWSUSPolicy and WorkstationWSUSPolicy.
WSUS Group Policy for Windows servers
Let’s start with the description of the server policy – ServerWSUSPolicy.
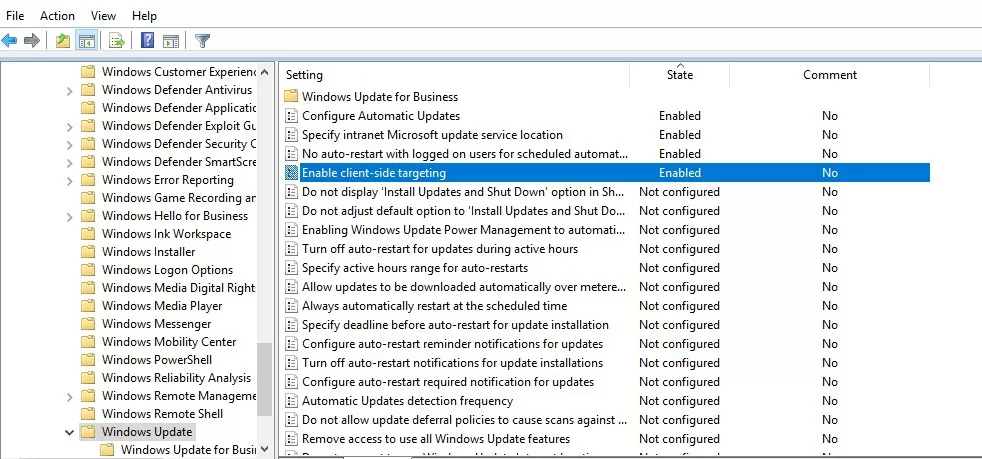
Group Policy settings that are responsible for the operation of the Windows Update service are located in the following GPO section: Computer Configuration -> Policies –> Administrative templates-> Windows Component-> Windows Update.
In our environment, we suggest to use this policy to install updates from WSUS on Windows servers. All the computers that fall under this policy are assigned to the Servers group in the WSUS console. In addition, we want to disable the automatic updates installation on the servers when they are received. During update client should just download the available updates to local drive, display the corresponding notification in the system tray and wait for administrator to manually start the installation (locally or remotely using the PSWindowsUpdate module). This means that productive servers won’t automatically install updates and restart without administrator confirmation (usually these tasks are performed by the system administrator as part of the monthly scheduled maintenance). To implement such a scheme, let’s set the following policies:
- Configure Automatic Updates: Enable. 3 – Auto download and notify for install – client automatically downloads new updates and notifies you about them;
- Specify Intranet Microsoft update service location: Enable. Set the intranet update service for detecting updates: http://hq-wsus.woshub.com:8530, Set the intranet statistics server: http://hq-wsus.woshub.com:8530 – set the address of the local WSUS server and the statistics server (usually they are the same);
- No auto-restart with logged on users for scheduled automatic updates installations: Enable – disable automatic restart if the user session is open;
- Enable client-side targeting: Enable. Target group name for this computer: Servers – in the WSUS console, assign clients to the Servers group.
WSUS Group Policy for Windows Workstations
We assume that in contrast to the server policy, updates to the client workstations are installed automatically at night immediately after receiving the updates. Computers should restart automatically after the installation of updates (notifying the user in 5 minutes).
In this GPO (WorkstationWSUSPolicy) we specify:
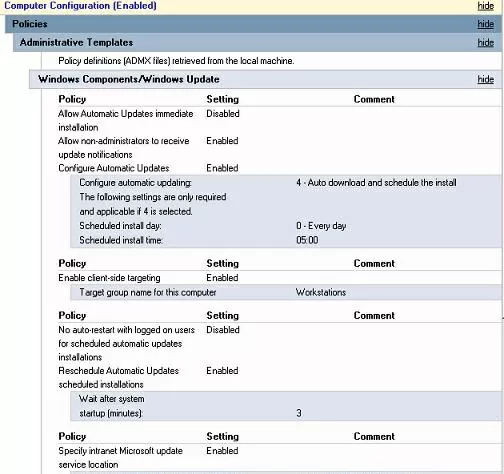
- Allow Automatic Updates immediate installation: Disabled – the immediate installation of updates after they are received is disabled;
- Allow non-administrators to receive update notifications: Enabled – display notifications of the new updates to non-administrators and allows to install them manually;
- Configure Automatic Updates: Enabled. Configure automatic updating: 4 – Auto download and schedule the install. Scheduled install day: 0 – Every day. Scheduled install time: 05:00 – a client downloads new updates and plans to install them automatically at 5:00 am;
- Target group name for this computer: Workstations – in the WSUS console, assign the client to the Workstations group;
- No auto-restart with logged on users for scheduled automatic updates installations: Disabled;
- Specify Intranet Microsoft update service location: Enable. Set the intranet update service for detecting updates: http://hq-wsus.woshub.com:8530, Set the intranet statistics server: http://hq-wsus.woshub.com:8530 – is the address of the corporate WSUS server.
In Windows 10 1607 and higher, despite the fact that you have specified to receive updates from the internal WSUS, Windows 10 may still try to access the Windows Update servers on the Internet. This “feature” is called Dual Scan. To disable receiving updates from the Internet, you need to additionally enable the policy Do not allow update deferral policies to cause scans against Windows Update.
Assigning the WSUS Group Policies to the AD OUs
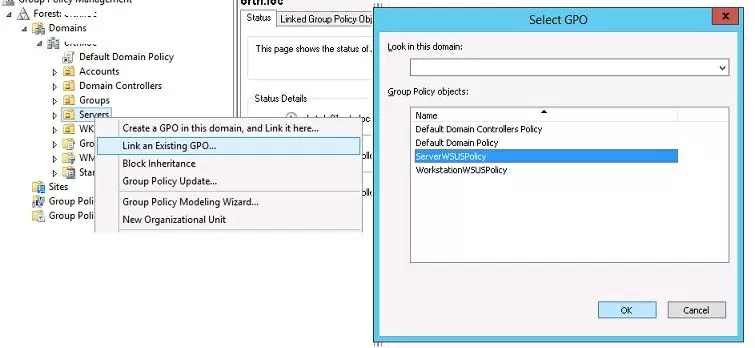
The next step is to assign the created policies to the corresponding Active Directory containers (OU). In our example OU structure is extremely simple: there are two containers – Servers (it contains all servers of the company, with the exception of the domain controllers) and WKS (Workstations – users’ computers).
To assign the policy to the OU, click the correct OU in the Group Policy Management Console, select Link an Existing GPO, and then check the appropriate policy.
You have to assign WorkstationWSUSPolicy to the AD container with the name WKS (where the Windows workstations are located) in the same way.
It remains to update the group policies on clients to bind the client to the WSUS server:
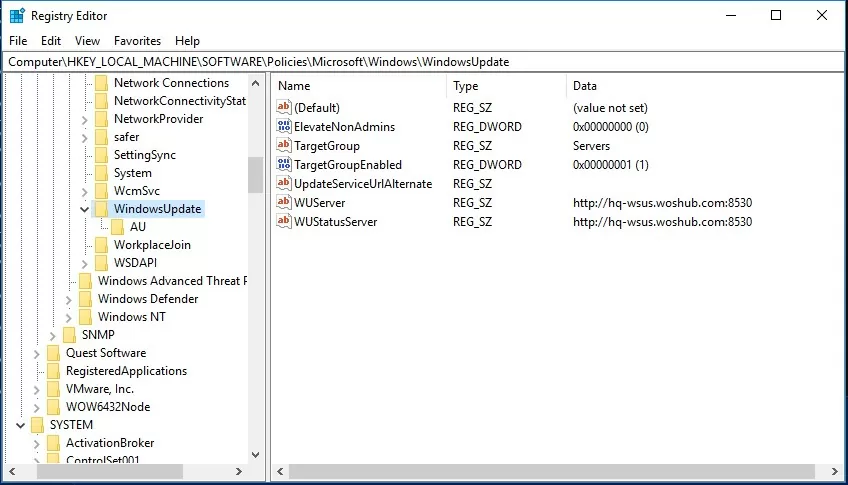
gpupdate /forceAll Windows update settings that we have set via the group policies should appear on the client’s in registry key HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate.
The following reg file can be used to transfer WSUS settings to other computers on which you cannot configure update settings using GPO (computers in a workgroup, isolated segments, DMZ, etc.)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
"WUServer"="http://hq-wsus.woshub.com:8530"
"WUStatusServer"="http://hq-wsus.woshub.com:8530"
"UpdateServiceUrlAlternate"=""
"TargetGroupEnabled"=dword:00000001
"TargetGroup"="Servers"
"ElevateNonAdmins"=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU]
"NoAutoUpdate"=dword:00000000 –
"AUOptions"=dword:00000003
"ScheduledInstallDay"=dword:00000000
"ScheduledInstallTime"=dword:00000003
"ScheduledInstallEveryWeek"=dword:00000001
"UseWUServer"=dword:00000001
"NoAutoRebootWithLoggedOnUsers"=dword:00000001
It is also convenient to control the applied WSUS settings on clients using the rsop.msc snap-in.
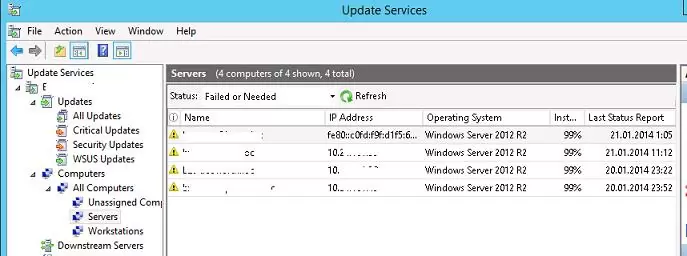
In some time (it depends on the number of updates and bandwidth to the WSUS server) check if there is a pop-up notification of the new updates in the tray. Clients (the client’s name, an IP, an OS, patch percentage and the date of the last status update) should appear in the corresponding groups in the WSUS console. Since we assigned the computers and servers to the different WSUS groups using GPO, they will receive only the updates that are approved for installation on the corresponding WSUS groups.
The client downloads updates to the local folder C:\Windows\SoftwareDistribution\Download.
To start the search for new updates on the WSUS server immediately, you need to run the command:
wuauclt /detectnowAlso, sometimes you have to force the client to re-register on the WSUS server:
wuauclt /detectnow /resetAuthorizationIn particularly difficult cases, you can try to fix the wuauserv service as follows. If an error 0x80244010 occurs when receiving updates on clients, try changing the frequency of checking for updates on the WSUS server using the Automatic Update detection frequency policy to 3-4 hours.
In the next articles we’ll describe the peculiarities of the update approval on the WSUS server, and how to transfer approved updates between groups to a WSUS server using PowerShell.
3 comments
What are the configuration need to be done on WSUS server, like Pre-approved / Auto Approve updates.
If we don’t approve update on WSUS will it get downloaded on clientt machine?
hello.
i am trying your solution, but when i run the powershell command: get-windowsupdatelog.
the clients are getting the correct target group. but the servers goes to the unassigned computers group.
how come?
Check the following:
1) The option “Use Group Policy or registry settings on computers” should be enabled in the WSUS settings,
2) Check the resulting Group Policy settings on the client using
rsop.msc. Make sure that the GPO sets the value for the “Target group name for this computer” parameter on the client. If not, check why your GPO is not applied (https://woshub.com/group-policy-not-applied-troubleshooting/)