To deploy new virtual machines in VMWare, VM templates are typically used. A VMWare VM template is a reference virtual machine copy with the configured settings, installed software and security updates. An administrator needs to regularly update the VM template to keep it up-to-date: install new Windows security updates (at least once a month), update system and application apps, update antivirus definitions, etc.
The update process of a VM template on VMWare consists of the following stages:
- A template from the Content Library is converted to a virtual machine.;
- After starting it, an administrator logs on, installs approved Windows updates using WSUS, updates the required software;
- After the updates have been installed, the VM is restarted, then turned of and converted back to the template.
In this article we will show how to install Windows updates to a VMWare virtual machine template automatically without doing anything manually.
You can use PowerCLI to install updates to a Windows virtual machine. We assume that the VMWare tools, PowerShell version 4 (or newer), and the PSWindowsUpdate module are installed in the virtual machine template. Running PowerShell scripts must be allowed in the guest OS by the script execution policy.
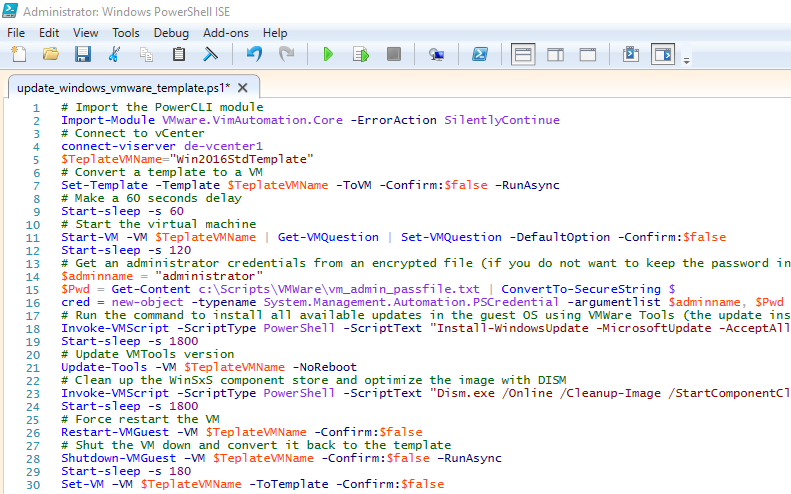
The PowerCLI script below will help you to automatically convert a VMWare template into a VM and install security updates from WSUS:
# Import the PowerCLI module
Import-Module VMware.VimAutomation.Core -ErrorAction SilentlyContinue
# Connect to vCenter
connect-viserver de-vcenter1
$TeplateVMName="Win2016StdTemplate"
# Convert a template to a VM
Set-Template -Template $TeplateVMName -ToVM -Confirm:$false –RunAsync
# Make a 60 seconds delay
Start-sleep -s 60
# Start the virtual machine
Start-VM -VM $TeplateVMName | Get-VMQuestion | Set-VMQuestion -DefaultOption -Confirm:$false
Start-sleep -s 120
# Get an administrator credentials from an encrypted file (if you do not want to keep the password in the PS script in clear text)
$adminname = "administrator"
$Pwd = Get-Content c:\Scripts\VMWare\vm_admin_passfile.txt | ConvertTo-SecureString $
cred = new-object -typename System.Management.Automation.PSCredential -argumentlist $adminname, $Pwd
# Run the command to install all available updates in the guest OS using VMWare Tools (the update installation log is saved to a file: C:\temp\Update.log)
Invoke-VMScript -ScriptType PowerShell -ScriptText "Install-WindowsUpdate -MicrosoftUpdate -AcceptAll -AutoReboot" -VM $TeplateVMName -GuestCredential $Cred | Out-file -Filepath C:\temp\Update.log -Append
Start-sleep -s 1800
# Update VMTools version
Update-Tools -VM $TeplateVMName -NoReboot
# Clean up the WinSxS component store and optimize the image with DISM
Invoke-VMScript -ScriptType PowerShell -ScriptText "Dism.exe /Online /Cleanup-Image /StartComponentCleanup /ResetBase" -VM $TeplateVMName -GuestCredential $Cred
Start-sleep -s 1800
# Force restart the VM
Restart-VMGuest -VM $TeplateVMName -Confirm:$false
# Shut the VM down and convert it back to the template
Shutdown-VMGuest –VM $TeplateVMName -Confirm:$false –RunAsync
Start-sleep -s 180
Set-VM –VM $TeplateVMName -ToTemplate -Confirm:$falseYou can add this PowerShell script to the Task Scheduler to automatically install updates to the template once a month a few days after Microsoft Patch Tuesday. Then if you deploy a new virtual machine from a VMWare template, you may be sure that the latest Microsoft security updates are installed in it.
6 comments
Hello,
Do you add this to the task scheduler of the template VM, or do you add it to the task scheduler of another VM (which then calls upon the template)?
Reason I am asking is because I thought templates are not powered on/cannot run any scheduled tasks.
Thanks in advanced.
Indeed, you cannot power on your VM template. That is why in my script there are commands for converting a template to a VM and vice versa
# Convert a template to a VMSet-Template -Template $TeplateVMName -ToVM -Confirm:$false –RunAsync
…….
Set-VM –VM $TeplateVMName -ToTemplate -Confirm:$false
It is assumed that the update script is executed from an external computer (administrator’s workstation)
Thank you for the guide!
Quick question, when I run:
Invoke-VMScript -ScriptType PowerShell -ScriptText “Install-WindowsUpdate -MicrosoftUpdate -AcceptAll -AutoReboot” -VM $TeplateVMName -GuestCredential $Cred | Out-file -Filepath C:\temp\Update.log -Append
I get a script output of accepted, downloaded, and installed for the updates. But when I log into the VM to verify they still show up as pending install and the update history doesn’t show anything being installed. Is this expected behavior or am I missing something?
You might also need to manually restart your Windows VM after the update.
Regards,
what about ubuntu 20.4 ?
Regards,
does only works with WSUS service running ?
i mean can i use normal/automaticall windows updates feature on windows ?
please confirm
My Best Regards