You can use the PSWindowsUpdate PowerShell module to manage Windows updates from the command line. The PSWindowsUpdate module is not built into Windows and is available for installation from the PowerShell Gallery repository. PSWindowsUpdate allows administrators to remotely check, install, remove, and hide updates on Windows servers and workstations. The PSWindowsUpdate module is especially valuable to manage updates on Windows Server Core or Hyper-V Server (which don’t have a GUI), and when configuring a Windows image in the audit mode.
- Installing the PSWindowsUpdate Module
- PSWindowsUpdate Cmdlets List
- Scan and Download Windows Updates with PowerShell
- Installing Windows Updates with PowerShell (Install-WindowsUpdate)
- Install Windows Update on Remote Computers with PowerShell
- Check Windows Update History with PowerShell (Get-WUHistory)
- Uninstalling Windows Updates with PowerShell (Remove-WindowsUpdate)
- How to Hide Windows Updates with PowerShell?
Installing the PSWindowsUpdate Module
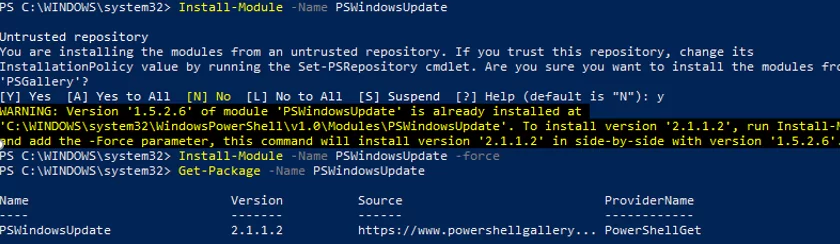
You can install the PSWindowsUpdate module on Windows 10/11 and Windows Server 2022/2019/2016 from the online repository (PSGallery) using the command:
Install-Module -Name PSWindowsUpdate -Force
After the installation is complete, you need to check the package:
Get-Package -Name PSWindowsUpdate
Install-Module: Unable to download from URI.Unable to download the list of available providers. Check your internet connection.
To install the module, you need to use the TLS 1.2 protocol for connection. Enable it for the current PowerShell session with the command:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
https://woshub.com/powershell-install-module-unable-download-uri/
If you have an older Windows version (Windows 7/8.1/Windows Server 2008 R2/2012 R2) or you don’t have direct Internet access, you can install PSWindowsUpdate manually (check the guide “How to install PowerShell modules offline?”).
- Download the PSWindowsUpdate module to any online computer:
Save-Module –Name PSWindowsUpdate –Path C:\ps\; - Copy the module to the following folder on the target computer
%WINDIR%\System32\WindowsPowerShell\v1.0\Modules; - Configure the PowerShell script execution policy:
Set-ExecutionPolicy –ExecutionPolicy RemoteSigned -force - You can now import the module into your PowerShell session:
Import-Module PSWindowsUpdate
| Unblock-File line from the PSWindowsUpdate.psm1 file manually.After installing the PSWindowsUpdate module on your computer, you can remotely install it on other computers or servers using the Update-WUModule cmdlet. For example, to copy the PSWindowsUpdate module from your computer to two remote hosts, run the commands (you need access to the remote servers via the WinRM protocol):
$Targets = "lon-fs02", "lon-db01"
Update-WUModule -ComputerName $Targets –Local
To save (export) the PoSh module to a shared network folder for further importing on other computers, run:
Save-Module -Name PSWindowsUpdate –Path \\lon-fs02\psmodules\
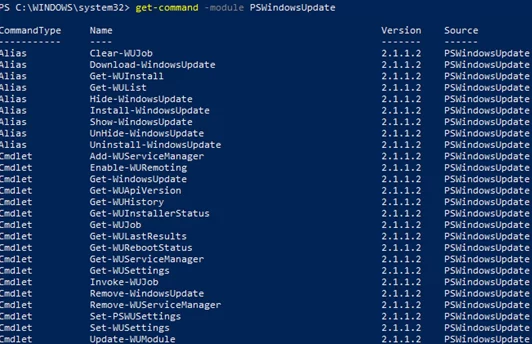
PSWindowsUpdate Cmdlets List
You can display the list of available cmdlets in the PSWindowsUpdate module as follows:
get-command -module PSWindowsUpdate
Let’s describe the usage of the module commands in brief:
- Clear-WUJob – use the Get-WUJob to clear the WUJob in Task Scheduler;
- Download-WindowsUpdate (alias for
Get-WindowsUpdate –Download) — get a list of updates and download them; - Get-WUInstall, Install-WindowsUpdate (alias for
Get-WindowsUpdate –Install) – install Windows updates; - Hide-WindowsUpdate (alias for
Get-WindowsUpdate -Hide:$false) – hide update; - Uninstall-WindowsUpdate – remove update using the Remove-WindowsUpdate;
- Add-WUServiceManager – register the update server (Windows Update Service Manager) on the computer;
- Enable-WURemoting — enable Windows Defender firewall rules to allow remote use of the PSWindowsUpdate cmdlets;
- Get-WindowsUpdate (Get-WUList) — displays a list of updates that match the specified criteria, allows you to find and install the updates. This is the main cmdlet of the PSWindowsUpdate module. Allows to download and install updates from a WSUS server or Microsoft Update. Allows you to select update categories, specific updates and set the rules of a computer restart when installing the updates;
- Get-WUApiVersion – get the Windows Update Agent version on the computer;
- Get-WUHistory – display a list of installed updates (update history);
- Get-WUInstallerStatus — check the Windows Installer service status;
- Get-WUJob – check for WUJob update tasks in the Task Scheduler;
- Get-WULastResults — dates of the last search and installation of updates (LastSearchSuccessDate and LastInstallationSuccessDate);
- Get-WURebootStatus — allows you to check whether a reboot is needed to apply a specific update;
- Get-WUServiceManager – list update sources;
- Get-WUSettings – get Windows Update client settings;
- Invoke-WUJob – remotely call WUJobs task in the Task Scheduler to immediately execute PSWindowsUpdate commands;
- Remove-WindowsUpdate – allows to uninstall an update by KB ID;
- Remove-WUServiceManager – disable Windows Update Service Manager;
- Set-PSWUSettings – save PSWindowsUpdate module settings to the XML file;
- Set-WUSettings – configure Windows Update client settings;
- Update-WUModule – update the PSWindowsUpdate module (you can update the module on a remote computer by copying it from the current one, or updating from PSGallery);
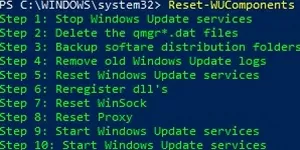
- Reset-WUComponents – allows you to reset the Windows Update agent on the computer to the default state.
To check the current Windows Update client settings, run the command:
Get-WUSettings
ComputerName : WKS5S2N39S2 WUServer : http://MN-WSUS:8530 WUStatusServer : http://MN-WSUS:8530 AcceptTrustedPublisherCerts : 1 ElevateNonAdmins : 1 DoNotConnectToWindowsUpdateInternetLocations : 1 TargetGroupEnabled : 1 TargetGroup : ServersProd NoAutoUpdate : 0 AUOptions : 3 - Notify before installation ScheduledInstallDay : 0 - Every Day ScheduledInstallTime : 3 UseWUServer : 1 AutoInstallMinorUpdates : 0 AlwaysAutoRebootAtScheduledTime : 0 DetectionFrequencyEnabled : 1 DetectionFrequency : 4
In this example, the Windows Update agent on the computer is configured with a GPO to receive updates from the local WSUS server.
The Reset-WUComponents -Verbose cmdlet allows you to reset all Windows Update Agent settings, re-register libraries, and restore the wususerv service to its default state.
Scan and Download Windows Updates with PowerShell
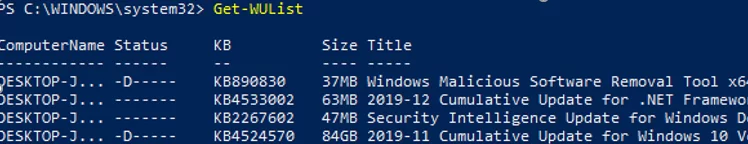
You can list the updates available for the current computer on the update server using the Get-WindowsUpdate or Get-WUList commands.
To check the list of available updates on a remote computer, run this command:
Get-WUList –ComputerName server2
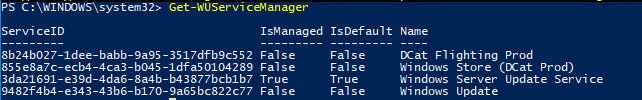
You can check where your Windows should receive updates from. Run the following command:
Get-WUServiceManager
ServiceID IsManaged IsDefault Name --------- --------- --------- ---- 8b24b027-1dee-babb-9a95-3517dfb9c552 False False DCat Flighting Prod 855e8a7c-ecb4-4ca3-b045-1dfa50104289 False False Windows Store (DCat Prod) 3da21691-e39d-4da6-8a4b-b43877bcb1b7 True True Windows Server Update Service 9482f4b4-e343-43b6-b170-9a65bc822c77 False False Windows Update
As you can see, the computer is configured to receive updates from the local WSUS server (Windows Server Update Service = True). In this case, you should see a list of updates approved for your computer.
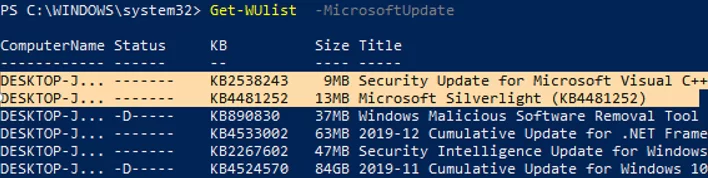
If you want to scan your computer against Microsoft Update servers on the Internet (in addition to Windows updates, these servers contain Office and other Microsoft product updates), run this command:
Get-WUlist -MicrosoftUpdate
You will get this warning:
Get-WUlist : Service Windows Update was not found on computer. Use Get-WUServiceManager to get registered service.
To allow scanning on Microsoft Update, run this command:
Add-WUServiceManager -ServiceID "7971f918-a847-4430-9279-4a52d1efe18d" -AddServiceFlag 7
You can now scan against Microsoft Update. In this case, additional updates were found for Microsoft Visual C ++ 2008 and Microsoft Silverlight.
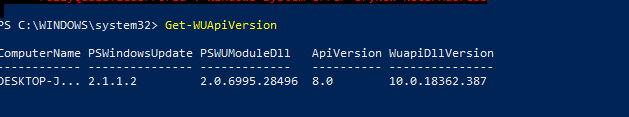
To check the version of the Windows Update Agent on the computer, run the command:
Get-WUApiVersion
ComputerName PSWindowsUpdate PSWUModuleDll ApiVersion WuapiDllVersion ------------ --------------- ------------- ---------- --------------- DESKTOP-J... 2.1.1.2 2.2.0.2 8.0 10.0.19041.1320
To remove specific products or KBs from the list of updates received by your computer, you can exclude them by:
- Category (
-NotCategory); - Title (
-NotCategory); - Update number (
-NotKBArticleID).
For example, let’s exclude OneDrive, driver updates, and the specific KB from the list:
Get-WUlist -NotCategory "Drivers" -NotTitle "OneDrive" -NotKBArticleID KB4489873
Installing Windows Updates with PowerShell (Install-WindowsUpdate)
To automatically download and install all available updates for your Windows device from Windows Update servers (instead of local WSUS), run the command:
Install-WindowsUpdate -MicrosoftUpdate -AcceptAll -AutoReboot
The AcceptAll parameter accepts the installation of all update packages, and AutoReboot allows Windows to automatically restart after the updates are installed.
You can also use the following options:
- IgnoreReboot – disable automatic reboot;
- ScheduleReboot – set the exact time to restart the computer.
You can save the update installation history to a log file (you can use it instead of WindowsUpdate.log file).
Install-WindowsUpdate -AcceptAll -Install -AutoReboot | Out-File "c:\logs\$(get-date -f yyyy-MM-dd)-WindowsUpdate.log" -force
You can install only the specific update packages by KB numbers:
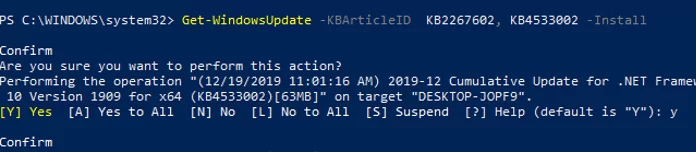
Get-WindowsUpdate -KBArticleID KB2267602, KB4533002 -Install
In this case, you need to confirm the installation of each update manually.
If you want to exclude certain updates from the installation list, run this command:
Install-WindowsUpdate -NotCategory "Drivers" -NotTitle OneDrive -NotKBArticleID KB4011670 -AcceptAll -IgnoreReboot
Install Windows Update on Remote Computers with PowerShell
The PSWindowsUpdate module allows you to install updates remotely on multiple workstations or servers at once (the PSWindowsUpdate must be installed/imported on these computers). This is very convenient because the administrator doesn’t have to manually log on to remote Windows hosts to install updates. WinRM must be enabled and configured on remote computers (manually or via GPO).
Almost all PSWindowsUpdate module cmdlets allow you to manage and install Windows updates on remote computers with the –Computername attribute.
Install the PSWindowsUpdate module on remote computers and allow access via dynamic RPC ports to the dllhost.exe process in the Windows Defender Firewall. You can use the Invoke-Command cmdlet to configure the PSWindowsUpdate module on remote computers:
$Targets = "lon-fs02", "lon-db01"
Invoke-Command -ComputerName $Target -ScriptBlock {Set-ExecutionPolicy RemoteSigned -force }
Invoke-Command -ComputerName $Target -ScriptBlock {Import-Module PSWindowsUpdate; Enable-WURemoting}
The PSWindowsUpdate module can be used to remotely manage Windows updates both on computers in an AD domain and in a workgroup (requires PowerShell Remoting configuration for workgroup environment).
In order to manage updates on remote computers, you need to add hostnames to your winrm trusted host list or configure PowerShell Remoting (WinRM) via HTTPS:
winrm set winrm/config/client '@{TrustedHosts="server1,server2,…"}'
Or with PowerShell :
Set-Item wsman:\localhost\client\TrustedHosts -Value server1 -Force
The following command will install all available updates on three remote Windows hosts:
$ServerNames = "server1, server2, server3"
Invoke-WUJob -ComputerName $ServerNames -Script {ipmo PSWindowsUpdate; Install-WindowsUpdate -AcceptAll | Out-File C:\Windows\PSWindowsUpdate.log } -RunNow -Confirm:$false -Verbose -ErrorAction Ignore
The Invoke-WUJob cmdlet (previously called Invoke-WUInstall) will create a scheduler task on the remote computer that runs under a local SYSTEM account.
You can specify the exact time to install Windows updates:
Invoke-WUJob -ComputerName $ServerNames -Script {ipmo PSWindowsUpdate; Install-WindowsUpdate –AcceptAll -AutoReboot | Out-File C:\Windows\PSWindowsUpdate.log } -Confirm:$false -TriggerDate (Get-Date -Hour 22 -Minute 0 -Second 0)
You can check the status of the update installation task using the Get-WUJob:
Get-WUJob -ComputerName $ServerNames
If the command returns an empty list, then the update installation task on all computers has been completed.
You can install updates on a remote computer and send an email report to the administrator:
Install-WindowsUpdate -ComputerName nysrv1 -MicrosoftUpdate -AcceptAll - IgnoreReboot -SendReport –PSWUSettings @{SmtpServer="smtp.woshub.com";From="updat[email protected]";To="[email protected]";Port=25} -Verbose
Check Windows Update History with PowerShell (Get-WUHistory)
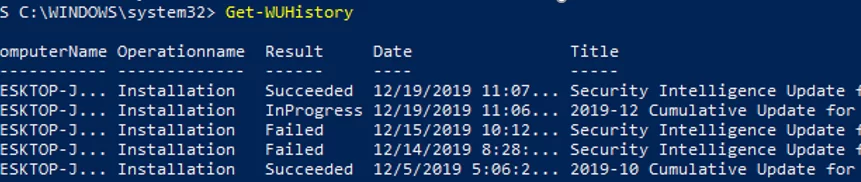
Using the Get-WUHistory cmdlet, you can get the list of updates installed on a computer earlier automatically or manually.
You can get the information about the installation date of a specific update:
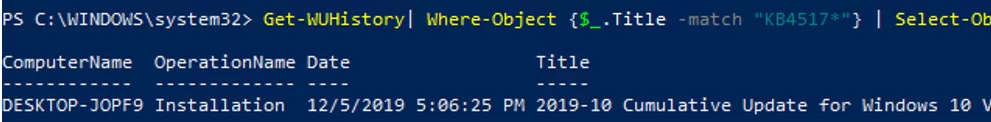
Get-WUHistory| Where-Object {$_.Title -match "KB4517389"} | Select-Object *|ft
To find out if the specific update has been installed on multiple remote computers, you can use this PowerShell code:
"server1","server2" | Get-WUHistory| Where-Object {$_.Title -match "KB4011634"} | Select-Object *|ft
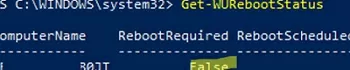
Check if the computer needs to be restarted after installing the update (pending reboot):
Get-WURebootStatus –ComputerName WKS21TJS
Check the value of the RebootRequired and RebootScheduled attributes.
You can generate a report with the dates when updates were last installed on all computers in the domain using the Get-ADComputer cmdlet (from the Active Directory for PowerShell module):
$Computers=Get-ADComputer -Filter {enabled -eq "true" -and OperatingSystem -Like '*Windows*' }
Foreach ($Computer in $Computers)
{
Get-WULastResults -ComputerName $Computer.Name|select ComputerName, LastSearchSuccessDate, LastInstallationSuccessDate
}
By analogy, you can find computers that have not installed updates for more than 60 days and display the result in the Out-GridView interactive table:
$result=@()
Foreach ($Computer in $Computers) {
$result+= Get-WULastResults -ComputerName $Computer.Name
}
$result| Where-Object { $_.LastInstallationSuccessDate -lt ((Get-Date).AddDays(-60)) }| Out-GridView
Uninstalling Windows Updates with PowerShell (Remove-WindowsUpdate)
You can use the Remove-WindowsUpdate cmdlet to correctly uninstall the updates with PowerShell. Just specify the KB number as an argument of the KBArticleID parameter. To delay automatic computer restart, add the –NoRestart option:
Remove-WindowsUpdate -KBArticleID KB4489873 -NoRestart
How to Hide Windows Updates with PowerShell?
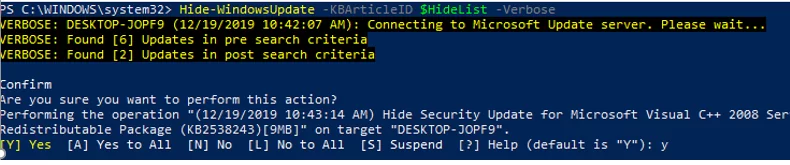
You can hide the specific updates so they will be never installed by the Windows Update service on your computer (most often you need to hide the driver updates). For example, to hide the KB4489873 and KB4489243 updates, run these commands:
$HideList = "KB4489873", "KB4489243"
Get-WindowsUpdate -KBArticleID $HideList –Hide
Now the next time you scan for updates using the Get-WUlist command, the hidden updates won’t be displayed in the list of updates available for installation.
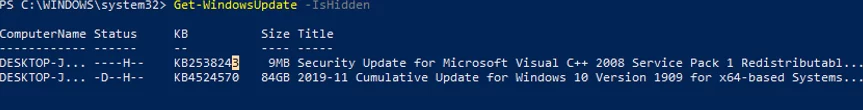
This is how you can display the list of updates hidden on this computer:
Get-WindowsUpdate –IsHidden
Notice that the H (Hidden) attribute has appeared in the Status column of hidden updates.
To unhide some updates, run this command:
Get-WindowsUpdate -KBArticleID $HideList -WithHidden -Hide:$false
or:
Show-WindowsUpdate -KBArticleID $HideList
For those who feel uncomfortable in the PowerShell console, I would recommend a graphic Windows Update MiniTool to manage updates in Windows 10/11 and Windows Server 2022/2019.
34 comments
Excellent piece. One surprise though was it was published in Mar of 2019 and I notice it uses Invoke-WUInstall which seems to have been removed from the current version of PSWindowsUpdate so wondering what version you based the article on
Excellent Article. Thanks
I get “Update-WUModule : A parameter cannot be found that matches parameter name ‘LocalPSWUSource’.”
did anyone try to run remotely, massively on several computers, install downloaded updates (from WSUS) and restart?
It looks like Invoke-WUInstall is now Invoke-WUJob
can you also let a client check for update to a nother computer in your VPN network and what ports and ^protocols needs to be open on a firewall? the client whit the updates is only reachable by ip so can we search whit client x on client y for updates by IP?
awesome post , thanks for the same.
I get a following error message, when I tried to run this command: Get-WUInstall -MicrosoftUpdate -IgnoreUserInput -AcceptAll -IgnoreReboot -Verbose
Error message: WARNING: Can’t find registered service Microsoft Update. Use Get-WUServiceManager to get registered service.
Do you have idea why cannot run this command?
Awesome script, thanks! I found one issue though, after I disabled Windows Update access using the command “set-wusettings DisableWindowsUpdateAccess”, I can’t re-enable it. I tried adding “False” at the end of the command, but it throws an error. Is there a different way to re-enable Windows Update Access?
Thanks
Please show me the Set-ClientWSUSSetting command that you are using and the full PowerShell error test.
What happens with with install Windows Updates on remote computers sections;
…Invoke-WUInstall : A parameter cannot be found that matches parameter name ‘RunNow’.
…Invoke-WUInstall : A parameter cannot be found that matches parameter name ‘SkipModuleTest’.
Total PS noob here. I’ve got PSWindowsUpdate (v2.2.0.2) installed on various Windows Server 2016 VMs and a Windows 10 VM I am executing their commands remotely from. I was able to update all of my server VMs successfully using PSWU commands. But, after restarting, a few of the VMs no longer respond to remote commands though the same commands work from the VMs’ consoles.
The problems some servers experience are one of two issues:
1) The command seemingly executes but nothing is returned.
For instance, on my Win10 VM I enter “get-wuhistory -computername SERVER -verbose” and get “Connecting to default for SERVER. Please wait…” No data is returned. I just come back to the PS prompt within a couple of seconds. Executing the command in PS at the server’s console results in the full history of applied Windows updates.
2) I enter the command “get-wuhistory -computername SERVER -verbose” and get the following results
—————————————————–
VERBOSE: Performing the operation “(5/19/2020 8:58:35 AM) Get Windows Update History” on target “SERVER”.
get-wuhistory : CORP-SYS-DC-01: Unknown failure.
At line:1 char:1
+ get-wuhistory -computername SERVER -verbose
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (:) [Get-WUHistory], Exception
+ FullyQualifiedErrorId : Unknown,PSWindowsUpdate.GetWUHistory
—————————————————–
Again, these commands worked fine until I restarted some of the servers. Oddly, the problem affects only a few of my servers.
Try if you can connect to these computers through PowerShell remoting. For example,
Enter-PSSession -ComputerName serveror try to get WU history with the Invoke-Command:
Invoke-Command -ComputerName Server1, Server2 -ScriptBlock {get-wuhistory -verbose}I have been successful in getting some updates to run, but i have two that are sitting in pending install state, and they never install. is there a parameter that needs to be input to get these pending install updates to go?
Can someone please explain me what update statuses are? I know that H means hidden, also I saw D. If I get it right there are 7 of them.
agreed – whats the “D” mean and others?
D = DOWNLOADED
Statuses (Get-Help Get-WindowsUpdate -detailed): [A|R]DIMHUB
A – IsAccetped
R – IsRejected
D – IsDownloaded
I – IsInstalled
M – IsMandatory
H – IsHidden
U – IsUninstallable
B – IsBeta
F – DownloadFailed
? – IsInvoked
F – InstallFailed
? – IsInvoked
R – RebootRequired
Sadly, the Remove-WindowsUpdate command has no -force parameter, making it useless for managed environment. I was looking for an alternative to wusa.exe, as it’s /quiet parameter is no longer supported in Windows 10. Sadly, it seems there is currently no way to silently remove certain updates, as the only alternative to wusa, dism, doesn’t list all updates :-/
Nice Article!. But the last patched details is not shown in “View Update History” in system
I have the same issue: last patched details is not shown in “View Update History” in system.
On some of my servers I get this error message when running this command:
invoke-command -ComputerName $c -ScriptBlock { Invoke-WUjob -ComputerName localhost -Script “ipmo PSWindowsUpdate; Install-WindowsUpdate -AcceptAll | Out-File C:\PSWindowsUpdate.log” -Confirm:$false -RunNow}
Any tips?
(10,44):StartBoundary:2021-05-19T15.35.38
+ CategoryInfo : NotSpecified: (:) [Invoke-WUJob], COMException
+ FullyQualifiedErrorId : System.Runtime.InteropServices.COMException,PSWindowsUpdate.InvokeWUJob
Invoke-command required elevated rights make sure you’re running Invoke-command as admin.
I’ve got the error:
Invoke-WUJob : The network path was not found. (Exception from HRESULT: 0x80070035)
when trying to install on remote machine. Cannot figure out why.
you have to set the executionpolicy to unrestricted and enable the WURemoting
Invoke-Command -ComputerName $computer -ScriptBlock {Set-ExecutionPolicy Unrestricted}
Invoke-Command -ComputerName $computer -ScriptBlock {Import-Module PSWindowsUpdate; Enable-WURemoting}
Is it possible to have multiple -NotTitle value’s?
For example: -NotTitle “Intel – Extension”, “ELAN – Mouse”
with -KBArticleID it should be possible to have multiple value’s but the updates I want to block don’t have KBArticleID’s
I use this syntax for the NotCategory parameter:
$UpdateCats = “‘Drivers’,’Feature Packs'”
-NotCategory $UpdateCats
Try to specify several values for the -NotTitle parameter in the same way.
Sadly this seems to not work for -nottitle parameter.
why below code with select-object dont work? pls try, i’m have results without select-obect, but when im try to choise one valu results is empty, pls try:
get-windowsupdate | select-object KB
why it dont work?
Nice script, thank you
A question:
I want to use the script in a Windows rollout (automated installation)
To do this, I am looking for a variable so that my script knows that the update is complete.
I thought of a process, but can’t find anything relevant.
Any idea ?
Greeting
A. Obert
Install-Module -Name PSWindowsUpdate -Force
this is not working
+ CategoryInfo : InvalidArgument: (:) [Install-Module], ArgumentException
This is what i’m going with for now:
invoke-wujob -computername -script “set-executionpolicy bypass -scope process -force; import-module pswindowsupdate; enable-wuremoting; start-sleep -seconds 60; get-windowsupdate -acceptall -install -autoreboot | out-file “C:\wulogs.log” -confirm:$false -verbose -runnow
Unable to install optional quality updates.
🙁
What ports are require to push the module from a local machine to remote machines, and also to run the commands against remote machines?
We have a highly locked down firewall infrastructure, and need to approach the firewall team with a set of ports to allow for the use of this module.