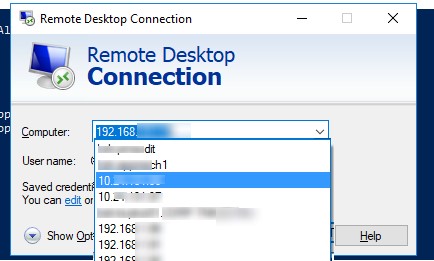
The built-in Windows Remote Desktop Connection (RDP) client (mstsc.exe) saves the remote computer name (or IP address) and the username that is used to login after each successful connection to the remote computer. On the next start, the RDP client offers the user to select one of the connections that was used previously. The user can select the name of the RDS/RDP host from the list, and the client automatically fills the username used earlier for login.
This is convenient from the end-user perspective, but unsafe from the security point of view. Especially when you connect to your RDP server from a public or untrusted computer.
Information about all RDP (terminal) sessions is stored individually in the registry hive of each user, i.e. a non-admin won’t be able to view the RDP connection history of another user.
In this article we will show where Windows stores the history and saved credentials of Remote Desktop connections, how to remove entries from the mstsc window, and clear RDP logs.
How to Remove RDP Connection Cache from the Registry?
Information about all RDP connections is stored in the registry of each user. It’s impossible to remove a computer (or computers) from the list of RDP connection history using built-in Windows tools. You will have to manually clear some registry keys.
- Run the Registry Editor (
regedit.exe) and browse to the registry key HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client; - You need two registry keys in this section: Default (stores the history of the last 10 RDP connections) and Servers (contains the list of all RDP servers and usernames used previously to login);
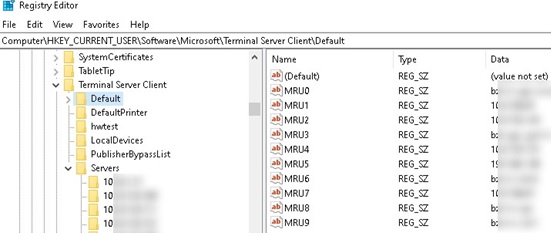
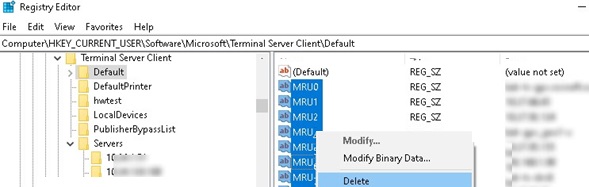
- Expand the registry key HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default which contains the list of 10 IP addresses or DNS names of remote computers that have been used recently (MRU – Most Recently Used). The name (or the IP address) of the remote desktop server is stored in the value of the MRU*. parameter. To clear the history of the most recent RDP connections, select all parameters with the names of MRU0-MRU9, right-click and select Delete;
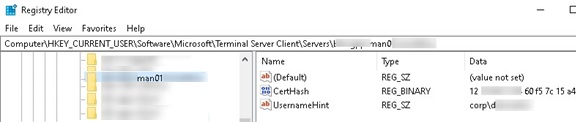
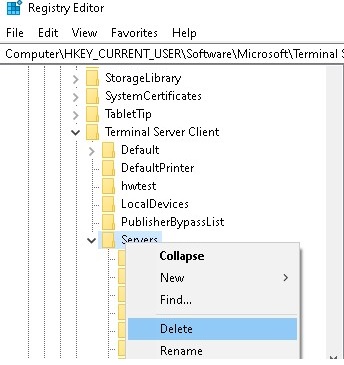
- Now expand the key HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers. It contains the list of all RDP connections that have ever been established by this user. Expand the reg key with the name (or ip address) of any host. Pay attention to the value of the UsernameHint parameter. It shows the username used to connect to the RDP/RDS host. This username will be used to connect to the RDP host automatically. In addition, the CertHash variable contains the RDP server SSL certificate thumbprint (see the article “Configuring trusted TLS/SSL certificates for RDP”);
- In order to clear the history of all RDP connections and saved usernames, you must clean the contents of Servers registry key. Since it’s impossible to select all nested registry keys at once, it’s easier to delete the entire Servers key and then recreate it manually;
- Next you need to delete the default RDP connection file (which contains information about the latest rdp session) – Default.rdp (this file is a hidden file located in Documents directory).
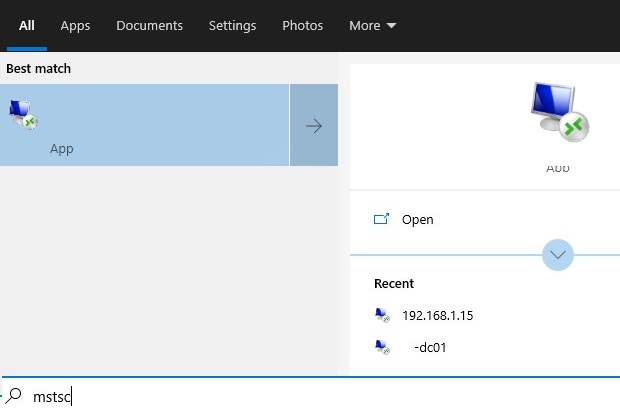
- Windows also saves the recent Remote Desktop connections in Jump Lists. If you type
mstscin the Windows 10 search box, the previously used RDP connections will appear in the list. You can completely disable Windows 10 recent file and location in Jump list with the registry dword parameter Start_TrackDocs in the reg keyHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced(set it to 0), or you can clear the Resent Items lists by deleting files in the directory%AppData%\Microsoft\Windows\Recent\AutomaticDestinations.
Script to Clear RDP Connection History
Above we have showed how to clear the history of RDP connection in Windows manually. However, doing it manually (especially on multiple computers) is time consuming. Therefore, we offer a small script (BAT file) that allows to automatically clearing the RDP history.
To automate the RDP history cleanup, you can place this script to Windows Startup or run it on user computers via a GPO logoff script.
@echo off
reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default" /va /f
reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" /f
reg add "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers"
attrib -s -h %userprofile%\documents\Default.rdp
del %userprofile%\documents\Default.rdp
del /f /s /q /a %AppData%\Microsoft\Windows\Recent\AutomaticDestinations
Let’s consider all the actions of the script:
- Disable the output of the information to the console;
- Delete all the parameters in the registry key HKCU\Software\Microsoft\Terminal Server Client\Default (clear the list of recent RDP connections);
- Delete the entire reg key HKCU\Software\Microsoft\Terminal Server Client\Servers (clears the list of all RDP connection and saved user names);
- Recreate the previously deleted registry key;
- Change the Default.rdp file attributes in the profile directory of the current user (by default it is Hidden and System);
- Delete the Default.rdp file;
- Clear Remote Desktop Connection entries from jump list recent items.
In addition, you can clear the history of RDP connections using the following PowerShell script:
Get-ChildItem "HKCU:\Software\Microsoft\Terminal Server Client" -Recurse | Remove-ItemProperty -Name UsernameHint -Ea 0
Remove-Item -Path 'HKCU:\Software\Microsoft\Terminal Server Client\servers' -Recurse 2>&1 | Out-Null
Remove-ItemProperty -Path 'HKCU:\Software\Microsoft\Terminal Server Client\Default' 'MR*' 2>&1 | Out-Null
$docs = [environment]::getfolderpath("mydocuments") + '\Default.rdp'
remove-item $docs -Force 2>&1 | Out-Null
How to Prevent Windows from Saving RDP Connection History?
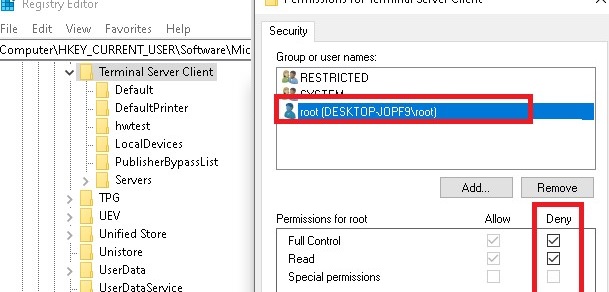
If you do NOT want Windows to save the RDP connection history, you must deny writing to the registry key HKCU\Software\Microsoft\Terminal Server Client for all user accounts. First, disable permission inheritance on the specified reg key (Permissions -> Advanced -> Disable inheritance). Then change the registry key ACL by ticking the Deny option for users (but you should understand that this is an unsupported configuration).
As a result, mstsc.exe simply cannot write RDP connection info to the registry.
How to Clear Remote Desktop Bitmap Cache?
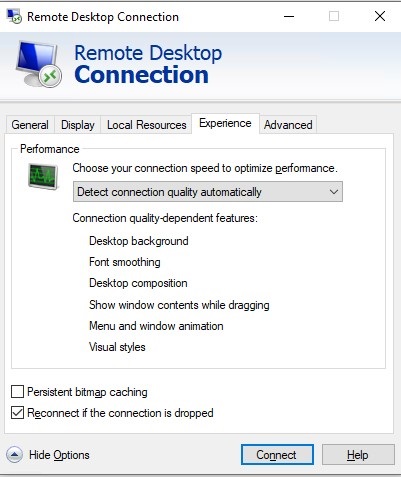
The Remote Desktop Connection client has image persistent bitmap caching feature. The RDP client saves rarely changing fragments of the remote screen as a raster image cache. Thanks to this, the mstsc.exe client loads parts of the screen that have not changed since the last rendering from the local drive cache. This RDP caching feature reduces the amount of data transmitted over the network.
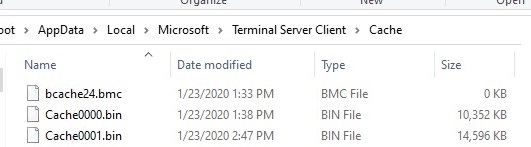
RDP cache is two types of files in a directory %LOCALAPPDATA%\Microsoft\Terminal Server Client\Cache:
- *.bmc
- bin
These files store raw RDP screen bitmaps in the form of 64×64 pixel tiles. Using simple PowerShell or Python scripts (easily searched for by the RDP Cached Bitmap Extractor query), you can get PNG files with pieces of the remote desktop screen and use them to get sensitive information. The size of the tiles is small, but sufficient to provide useful information to a person studying the RDP cache.
You can prevent the RDP client from storing the remote desktop screen image cache by disabling the Persistent bitmap caching option on the Advanced tab.
Bitmap Disk Cache Failure. Your disk is full or the cache directory is missing or corrupted. Some bitmaps may not appear.
In this case, you need to clear the RDP cache directory or disable the Bitmap Caching option.
Clearing Saved RDP Credentials
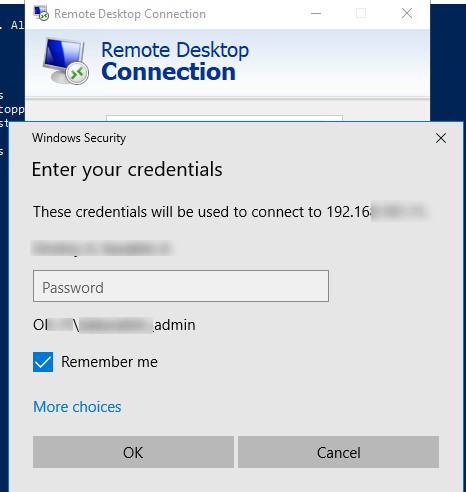
If when establishing a new remote RDP connection, before entering the password, the user checks an option Remember Me, then the username and password will be saved in the Windows Credential Manager. The next time you connect to the same computer, the RDP client automatically uses the previously saved password for authentication on the remote host.
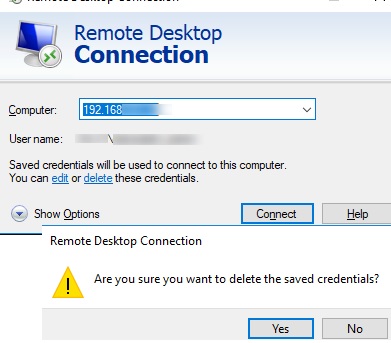
You can remove the saved RDP password directly from the client’s mstsc.exe window. Select the same connection from the list of connections, and click on the Delete button. Then confirm deletion of the saved credentials.
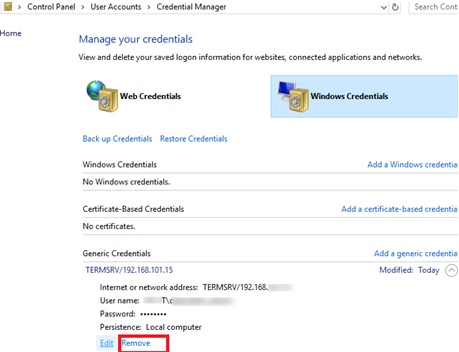
Alternatively, you can delete the RDP saved password directly from the Windows Credential Manager. Go to the Control Panel\User Accounts\Credential Manager section. Select Manage Windows Credentials and in the list of saved passwords find the computer name (in the following format TERMSRV/192.168.1.100). Expand the found item and click the Remove button.
In an Active Directory domain environment, you can disable saving passwords for RDP connections by using the special GPO – Network access: Do not allow storage of passwords and credentials for network authentication (see an article).
Removing RDP-Related Event Logs on a Remote Host
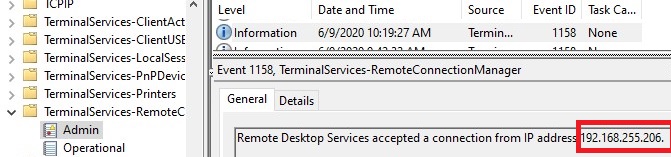
Connection logs are also saved on the RDP/RDS host side. You can find information about RDP connection history in Event Viewer logs:
- Security;
- Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-RemoteConnectionManager -> Operational;
- TerminalServices-LocalSessionManager -> Admin.
You can clear the Event Logs on an RDP server using wevtutil or PowerShell.
10 comments
Thanks for your post. I was looking to clear the last connection, and deleting the default.rdp file helped in that regard. Thanks again!
I am still getting the username once I login to the RDP
go to “Documents” folder and delete “Default.rdp”
In windows 10 there is still a recent connection list when you search RDP in bottom search bar and it brings the RDP client app in the result. How to clear that too?
Thanks, it worked.
still leaves sum info on the resents on windows 10
Is there a way to prevent RDP from caching remote computer name
I do not want RDP to cache remote computer name at all
Thanks for publishing this forum. It was very helpful to me.
Thanks, the script worked and saved a lot of time
Hello,
This batch file does not work on Windows 11. Is there a way to make it work on Windows 11? Please help me out. Please