In this article, we’ll describe how to get and audit the RDP connection logs in Windows. The RDP connection logs allow RDS terminal servers administrators to get information about which users logged on to the server when a specific RDP user logged on and ended up the session, and from which device (DNS name or IP address) the user logged on.
RDP Connection Events in Windows Event Viewer
When a user connects to a Remote Desktop-enabled or RDS host, information about these events is stored in the Event Viewer logs (eventvwr.msc). Consider the main stages of RDP connection and related events in the Event Viewer, which may be of interest to the administrator
- Network Connection;
- Authentication;
- Logon;
- Session Disconnect/Reconnect;
- Logoff.
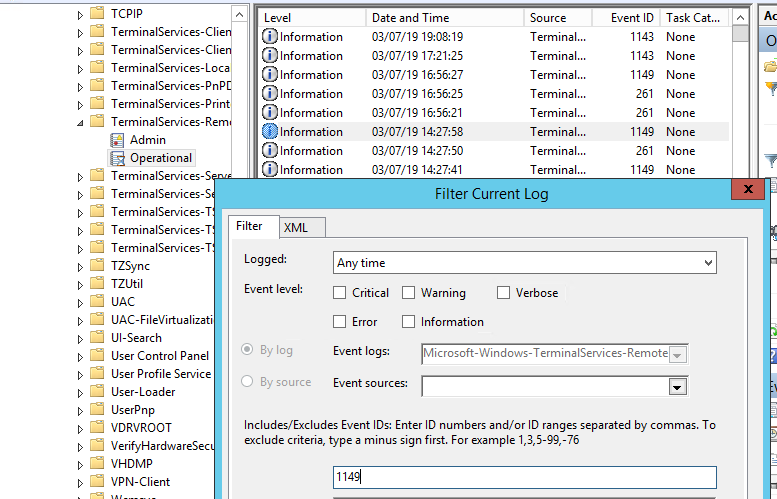
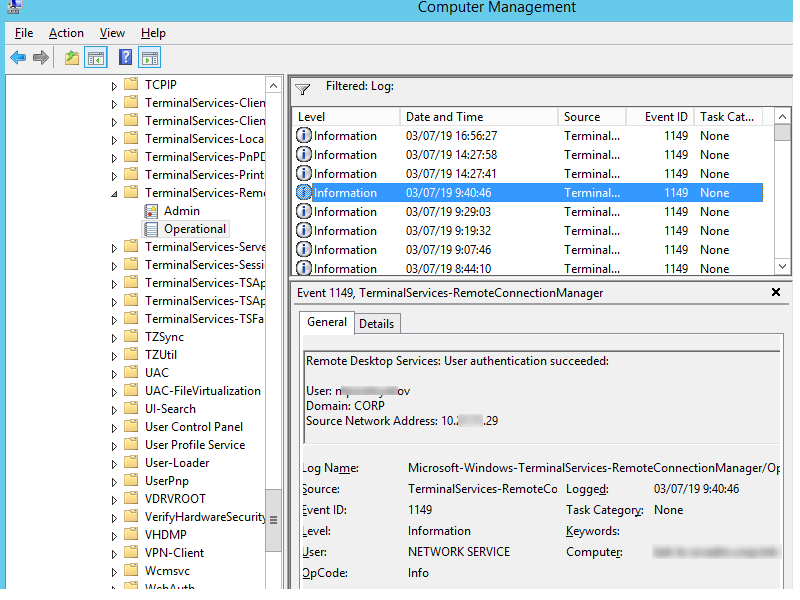
Network Connection – establishing a network connection to a server from the user’s RDP client. It is the event with the EventID 1149 (Remote Desktop Services: User authentication succeeded). If this event is found, it doesn’t mean that user authentication has been successful. This log is located in “Applications and Services Logs -> Microsoft -> Windows -> Terminal-Services-RemoteConnectionManager > Operational”. Enable the log filter for this event (right-click the log -> Filter Current Log -> EventId 1149).
You can list all RDP connection attempts with PowerShell:
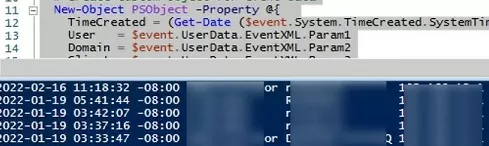
$RDPAuths = Get-WinEvent -LogName 'Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational' -FilterXPath '<QueryList><Query Id="0"><Select>*[System[EventID=1149]]</Select></Query></QueryList>'
[xml[]]$xml=$RDPAuths|Foreach{$_.ToXml()}
$EventData = Foreach ($event in $xml.Event)
{ New-Object PSObject -Property @{
TimeCreated = (Get-Date ($event.System.TimeCreated.SystemTime) -Format 'yyyy-MM-dd hh:mm:ss K')
User = $event.UserData.EventXML.Param1
Domain = $event.UserData.EventXML.Param2
Client = $event.UserData.EventXML.Param3
}
} $EventData | FT
Then you will get an event list with the history of all RDP connections to this server. The logs provide a username, a domain (in this case the Network Level Authentication is used; if NLA is disabled, the event description looks differently), and the IP address of the user’s computer.
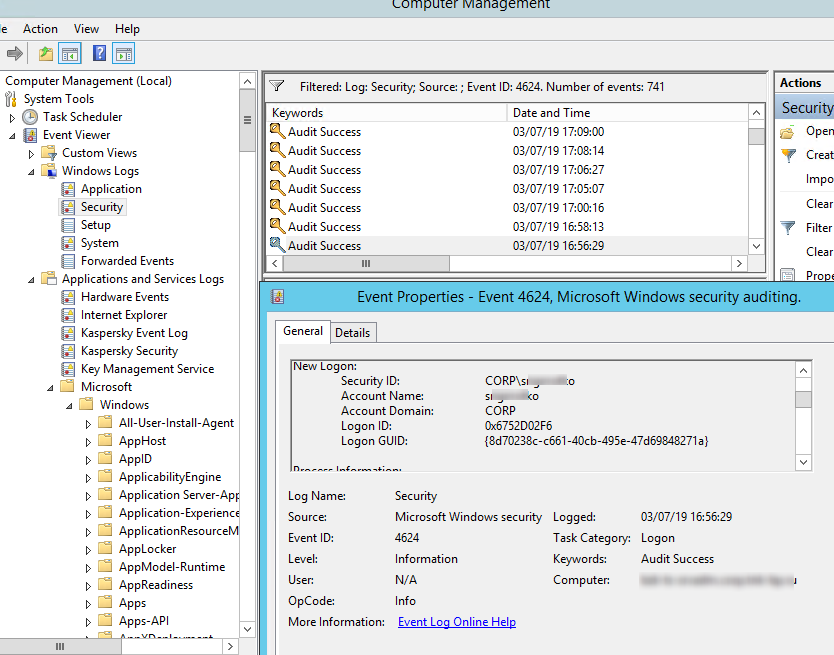
Authentication shows whether an RDP user has been successfully authenticated on the server or not. The log is located under Windows -> Security. So, you may be interested in the events with the EventID 4624 (An account was successfully logged on) or 4625 (An account failed to log on).
Please, pay attention to the LogonType value in the event description.
- LogonType = 10 or 3 — if the Remote Desktop service has been used to create a new session during log on;
- LogonType = 7, means that a user has reconnected to the existing RDP session;
- LogonType = 5 – RDP connection to the server console (in the mstsc.exe /admin mode).
In this case, the user name is contained in the event description in the Account Name field, the computer name in the Workstation Name, and the user IP in the Source Network Address.
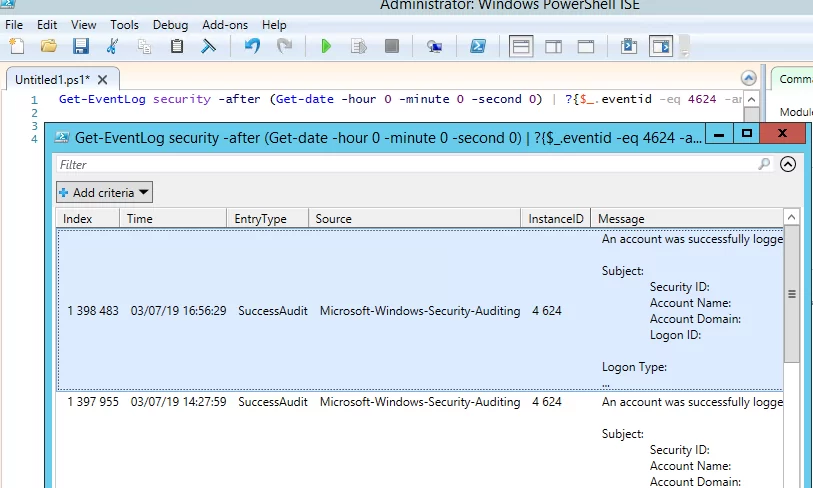
You can get a list of successful RDP authentication events (EventID 4624) using this PowerShell command:
Get-EventLog security -after (Get-date -hour 0 -minute 0 -second 0) | ?{$_.eventid -eq 4624 -and $_.Message -match 'logon type:\s+(10)\s'} | Out-GridView
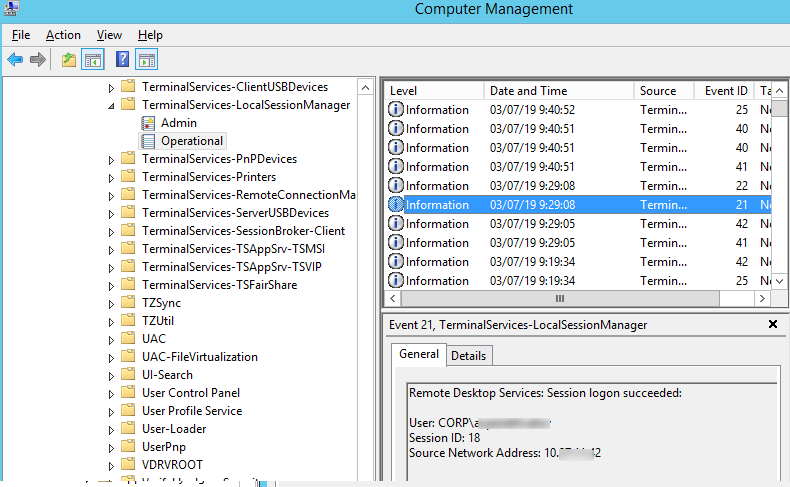
Logon refers to an RDP login to Windows. EventID 21 – this event appears after a user has been successfully authenticated (Remote Desktop Services: Session logon succeeded). This events are located in the “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”. As you can see, here you can find the ID of a user RDP session — Session ID.
EventID – 21 (Remote Desktop Services: Shell start notification received) indicates that the Explorer shell has been successfully started (the Windows desktop appears in the user’s RDP session).
Session Disconnect/Reconnect – session disconnection and reconnection events have different IDs depending on what caused the user disconnection (disconnection due to inactivity set in timeouts for RDP sessions, Disconnect option has been selected by the user in the session, RDP session ended by another user or an administrator, etc.). You can find these events in the Event Viewer under “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”. Let’s consider the RDP Event IDs that might be useful:
- EventID – 24 (
Remote Desktop Services: Session has been disconnected) –a user has disconnected from the RDP session; - EventID – 25 (
Remote Desktop Services: Session reconnection succeeded) – a user has reconnected to the existing RDP session on the server; - EventID – 39 (
Session <A> has been disconnected by session <B>) – a user has disconnected from the RDP session by selecting the corresponding menu option (instead of just closing the RDP client window). If the session IDs are different, a user has been disconnected by another user (or administrator); - EventID – 40 (
Session <A> has been disconnected, reason code <B>). Here you must check the disconnection reason code in the event description. For example:- reason code 0 (
No additional information is available) means that a user has just closed the RDP client window; - reason code 5 (
The client’s connection was replaced by another connection) means that a user has reconnected to the previous RDP session; - reason code 11 (
User activity has initiated the disconnect) a user has clicked the Disconnect button in the start menu.
- reason code 0 (
EventID 4778 in Windows -> Security log (A session was reconnected to a Window Station). A user has reconnected to an RDP session (a user is assigned a new LogonID).
EventID 4779 in “Windows -> Security” log (A session was disconnected from a Window Station). A user has been disconnected from an RDP session.
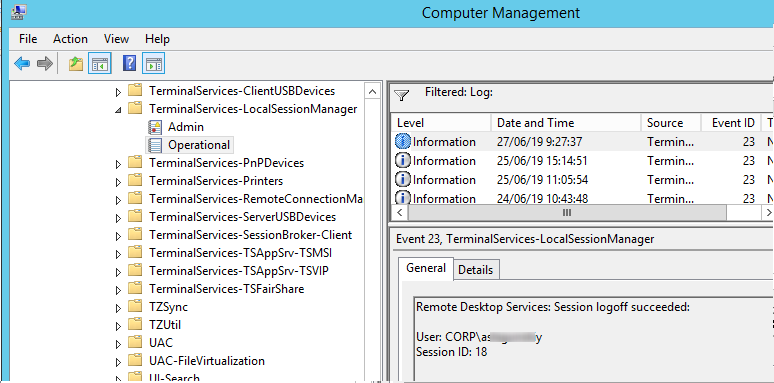
Logoff refers to the end of a user session. It is logged as the event with the EventID 23 (Remote Desktop Services: Session logoff succeeded) under “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”.
At the same time the EventID 4634 (An account was logged off) appears in the Security log.
The EventID 9009 (The Desktop Window Manager has exited with code <X>) in the System log means that a user has initiated logoff from the RDP session with both the window and the graphic shell of the user have been terminated.
EventID 4647 — User-initiated logoff
Getting Remote Desktop Login History with PowerShell
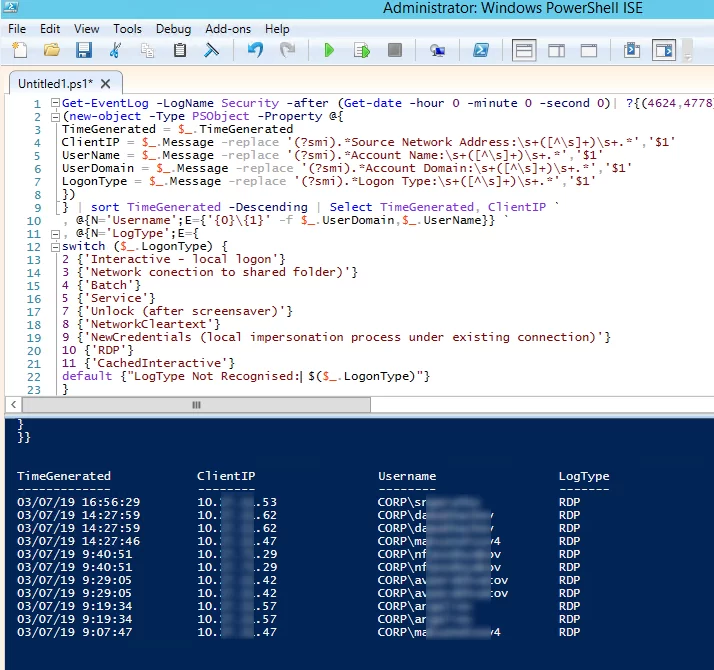
Here is a short PowerShell script that lists the history of all RDP connections for the current day from the terminal RDS server event logs. The resulting table shows the connection time, the client’s IP address (DNS computername), and the remote user name (if necessary, you can include other LogonTypes in the report).
Get-EventLog -LogName Security -after (Get-date -hour 0 -minute 0 -second 0)| ?{(4624,4778) -contains $_.EventID -and $_.Message -match 'logon type:\s+(10)\s'}| %{
(new-object -Type PSObject -Property @{
TimeGenerated = $_.TimeGenerated
ClientIP = $_.Message -replace '(?smi).*Source Network Address:\s+([^\s]+)\s+.*','$1'
UserName = $_.Message -replace '(?smi).*\s\sAccount Name:\s+([^\s]+)\s+.*','$1'
UserDomain = $_.Message -replace '(?smi).*\s\sAccount Domain:\s+([^\s]+)\s+.*','$1'
LogonType = $_.Message -replace '(?smi).*Logon Type:\s+([^\s]+)\s+.*','$1'
})
} | sort TimeGenerated -Descending | Select TimeGenerated, ClientIP `
, @{N='Username';E={'{0}\{1}' -f $_.UserDomain,$_.UserName}} `
, @{N='LogType';E={
switch ($_.LogonType) {
2 {'Interactive - local logon'}
3 {'Network connection to shared folder)'}
4 {'Batch'}
5 {'Service'}
7 {'Unlock (after screensaver)'}
8 {'NetworkCleartext'}
9 {'NewCredentials (local impersonation process under existing connection)'}
10 {'RDP'}
11 {'CachedInteractive'}
default {"LogType Not Recognised: $($_.LogonType)"}
}
}}
You can export RDP connection logs from the Event Viewer to a CSV file (for further analysis in an Excel spreadsheet). You can export the log from the Event Viewer GUI (assuming Event Viewer logs are not cleared) or via the command prompt:
WEVTUtil query-events Security > c:\ps\rdp_security_log.txt
Or with PowerShell:
get-winevent -logname "Microsoft-Windows-TerminalServices-LocalSessionManager/Operational" | Export-Csv c:\ps\rdp_connection_log.txt -Encoding UTF8
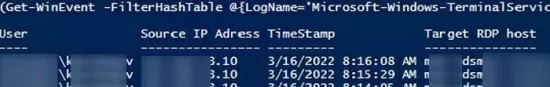
If your users connect to corporate RDS hosts through the Remote Desktop Gateway, you can check the user connection logs in the Microsoft-Windows-TerminalServices-Gateway log by the EventID 302. For example, the following PowerShell script will display the specified user’s connection history through RD Gateway:
$rdpusername="b.smith"
$properties = @(
@{n='User';e={$_.Properties[0].Value}},
@{n='Source IP Adress';e={$_.Properties[1].Value}},
@{n='TimeStamp';e={$_.TimeCreated}}
@{n='Target RDP host';e={$_.Properties[3].Value}}
)
(Get-WinEvent -FilterHashTable @{LogName='Microsoft-Windows-TerminalServices-Gateway/Operational';ID='302'} | Select-Object $properties) -match $rdpusername
- 300 — The user NAME, on client computer DEVICE, met resource authorization policy requirements and was therefore authorized to connect to resource RDPHOST;
- 302 — The user NAME, on client computer DEVICE, connected to resource RDPHOST;
- 303 — The user NAME, on client computer DEVICE, disconnected from the following network resource: RDPHOST. Before the user disconnected, the client transferred X bytes and received X bytes. The client session duration was X seconds.
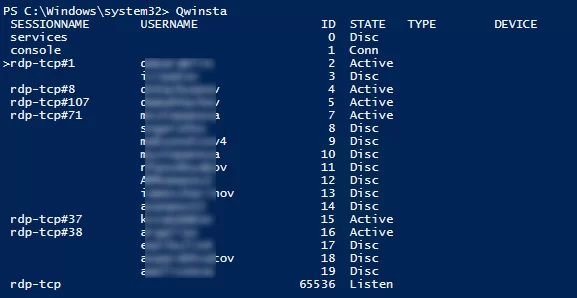
You can display the list of current remote sessions on your RDS host with the command:
qwinsta
The command returns the session ID, the USERNAME, and the session state (Active/Disconnect). This command is useful when you need to get the user’s RDP session ID when using shadow Remote Desktop connections.
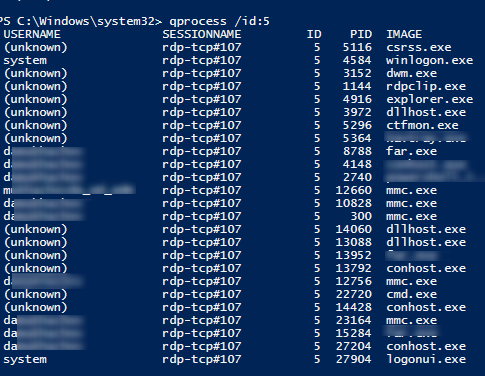
You can display the list of the running processes in the specific RDP session (the session ID is specified):
qprocess /id:5
Outgoing RDP Connection Logs in Windows
You can also view outgoing RDP connection logs on the client side. They are available in the following event log: Application and Services Logs -> Microsoft -> Windows -> TerminalServices-ClientActiveXCore -> Microsoft-Windows-TerminalServices-RDPClient -> Operational.
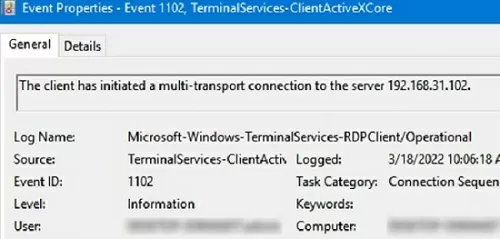
For example, EventID 1102 occurs when a user connects to a remote Windows Server RDS host or a Windows 10/11 computer with RDP enabled (desktop Windows editions also support multiple simultaneous RDP connections).
The client has initiated a multi-transport connection to the server 192.168.13.201.
The following RDP script will display the history of RDP client connections on the current computer:
$properties = @(
@{n='TimeStamp';e={$_.TimeCreated}}
@{n='LocalUser';e={$_.UserID}}
@{n='Target RDP host';e={$_.Properties[1].Value}}
)
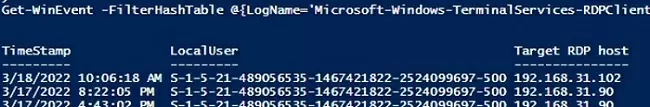
Get-WinEvent -FilterHashTable @{LogName='Microsoft-Windows-TerminalServices-RDPClient/Operational';ID='1102'} | Select-Object $properties
The script returns the SIDs of the users who initiated RDP connections on this computer, as well as the DNS names/IP addresses of the Remote Desktop hosts that the users connected to. You can convert SIDs to usernames as follows.
25 comments
First at all great article, it helped me already with some analysis.
But i would have a short question about an reason code i receive in the TerminalServices-LocalSessionManager Log, maybe you can help me with it:
“Session 90 has been disconnected, reason code 3489660929”
What is the reason code: 3489660929?
Currently my users are experiencing random disconnects on my RDS 2019 Farm where always this reason code pops up.
I am trying to run this on a Windows 10 machine and nothing occurs. I am running from the ISE under admin privileges. Still get no response, just returns to prompt.
And are there some connections to this machine via RDP ? If not, then the log is empty.
top info 🙂 thanks a lot!
great article and very detailed information.
my question, though, can you do this (powershell scripts) of another computer? like remotely?
Useful, Thank you.
Great article and very helpful, thank you
I am running it in windows 2016 and return all value fine but for user name is showing like -\-
any idea?
Hi. Very good job, it worked awesomely to me.
How can I set the Event Log properties for the Applications and Services Logs.
For windows logs I use “Limit-EventLog -logname …..”, but I can’t figure out how to point to that session.
Thanks for sharing. Very detailed. However, I’m having same issue as Arman. When running PowerShell script on Windows Server 2019, Username results display: “\-” (without quotes).
If you are getting the “-\-” problem with Domain and username
replace
UserName = $_.Message -replace ‘(?smi).*Account Name:\s+([^\s]+)\s+.*’,’$1′
UserDomain = $_.Message -replace ‘(?smi).*Account Domain:\s+([^\s]+)\s+.*’,’$1′
with
UserName = $_.Message -replace ‘(?smi).*\s\sAccount Name:\s+([^\s]+)\s+.*’,’$1′
UserDomain = $_.Message -replace ‘(?smi).*\s\sAccount Domain:\s+([^\s]+)\s+.*’,’$1′
The regex was picking up the “Network Account name” and “Network Account Domain” entries in error
The article is great. Thanks for sharing.
But sometimes there are no 4624 event logs because of the rotation of the logs, in fact most of the times if we think from a DFIR consulting perspective.
What do you propose on this cases?
This worked like a charm, thank you
Guys, how do I limit the export for just 1 user I am looking for? Thank you for the script, it works great.
Not working on windows server 2019 🙁
Any idea?
Brilliant article, very helpful, I refer to it regularly.
Just one last line you could add, though, about the next step down where a connection doesn’t even get to the Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational log…
thanks for valuable article. it enlightened me about rdp logs location.
Very informative…however…I have a unique issue: I am looking for an attempt to do a RDP from the server (X) to an unknown IP address (Computer Y).
I am not able to view any event/logs/activity indicating a RDP task was initiated. I do see it in the Firewall log that RDP is blocked – whereas Server (x) was the source and Computer (Y) is the designation. I am not able to find rhyme or reason for RDP is being initiated.
Check RDP client events. Look under ‘Application and Services Logs’ -> ‘Microsoft’ -> ‘Windows’ -> ‘TerminalServices-ClientActiveXCore’ -> ‘Microsoft-Windows-TerminalServices-RDPClient/Operation’
I’ve got a very simple question:
Been bashing my head against this for hours now, but how do you modify the timeframe of the PS script from only the current day to say, the current month or so?
Last 30 days:
(get-date).AddMonths(-1)Current month:
$LastMonth = (Get-Date).AddMonths(-1)$FirstDayOfMonth = $LastMonth | Get-Date -Format "yyyy/MM/01"
Get-EventLog security -after $FirstDayOfMonth .....
Can you send me your contact?
What can we do if we do not have an RDS server and we want to log all domain users through AD? I hope I could explain myself, I used translate. thanks
Thank you for the great article!
One note: this – “LogonType = 10 or 3 — if the Remote Desktop service has been used to create a new session during log on;” is not correct: only LogonType=10 designates RDP logon, LogonType=3 means any network logon (accessing a shared folder, for example) so filtering the Security log on logontype=3 will be useless in terms of RDP.
Hi mate,
Firstly, thanks for this article… very helpful.
I’m trying to find a way to send notifications to a Microsoft Teams channel every time someone logs on/logs off into/from a server.
I know how to do the Power Automate flow to get triggered by an API request that could be done using Powershell using Invoke-WebRequest.
But doing the trigger on the server side is hard. I’m thinking of something like a Task Schedule job that is triggered by those specific Event IDs, but hasn’t worked for me so far.
Any other ideas? Have you done any article on that?
Thanks a lot!
You can send a notification to your Teams channel from PowerShell as follow
Then attach this PowerShell script to the required event IDs (see an example here)