The read-only domain controller (RODC) feature was first introduced in Windows Server 2008. The main purpose of the RODC is the secure installation of the own domain controller in remote branches and offices where it is difficult to physically secure an ADDS role server. The RODC contains a read-only copy of the Active Directory database. This means that nobody can change data in AD (including reset of the domain admin password) even having physical access to the domain controller host.
In this article, we’ll look at how to install a new Read-Only domain controller based on Windows Server 2022/2019 and how to manage it.
What is a Read-Only Domain Controller (RODC) in Active Directory?
Here are the main differences of the RODC from common read-writable domain controllers (RWDC)
- The RODC maintains a read-only copy of the AD database. So the clients of this domain controller cannot make changes to it;
- The RODC doesn’t replicate AD data and SYSVOL folder to other domain controllers (RWDC), one-way replication is used;
- The RODC maintains a full copy of the AD database except for password hashes of the AD objects and some other attributes containing sensitive information. This set of attributes is called Filtered Attribute Set (FAS). Attributes like ms-PKI-AccountCredentials, ms-FVE-RecoveryPassword, ms-PKI-DPAPIMasterKeys, etc. are included in it. You can add other attributes to this set, such as computer passwords stored in cleartext in the ms-MCS-AdmPwd attribute when using LAPS;
- If the RODC receives an authentication request from a user, it forwards the request to the RWDC;
- The RODC can cache the credentials of some users (it speeds up the authentication and allows the users to authenticate on the domain controller, even if there is no connection to the RWDC);
- You can provide administrative and RDP access to the RODC to the non-admin users (for example, for the branch SysOps);
- The DNS service on the RODC is in read-only mode.
Requirements to deploy the Read-Only Domain Controller.
- A static IP has to be assigned on the server;
- The Windows Firewall has to be disabled or configured correctly to pass traffic between DCs and clients;
- The nearest RWDC must be specified as the DNS server;
- You can install RODC on both Windows Server Full GUI and Windows Server Core edition;
- You shouldn’t place the RODC on the same AD site as the RWDC.
Installing RODC Using Server Manager GUI
Open the Server Manager console and add the Active Directory Domain Services role (agree to install all additional components and management tools).
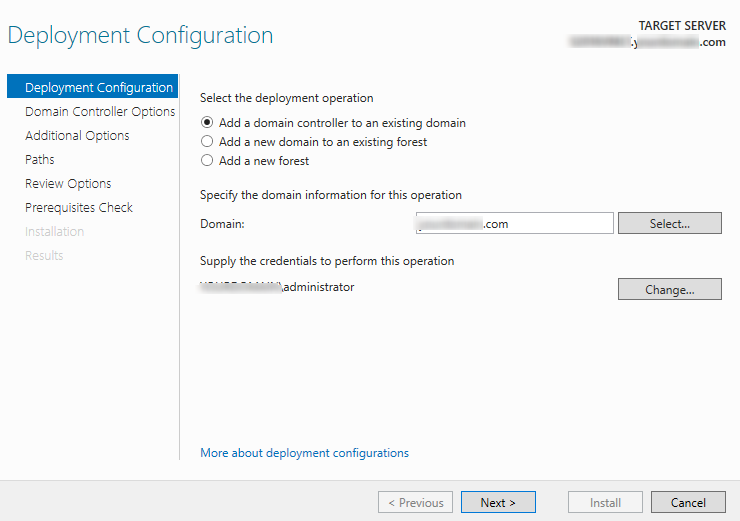
When you specify the settings for the new DC, check the Add a domain controller to an existing domain option, specify the domain name and the credentials of the user account with the domain administrator privileges if necessary.
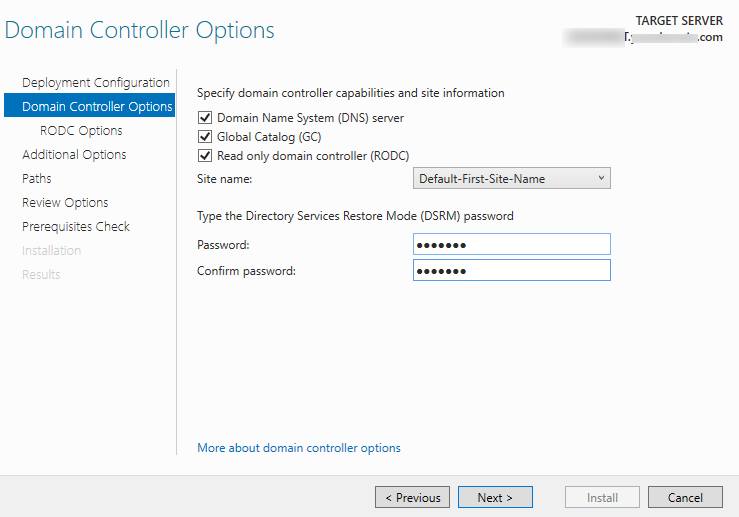
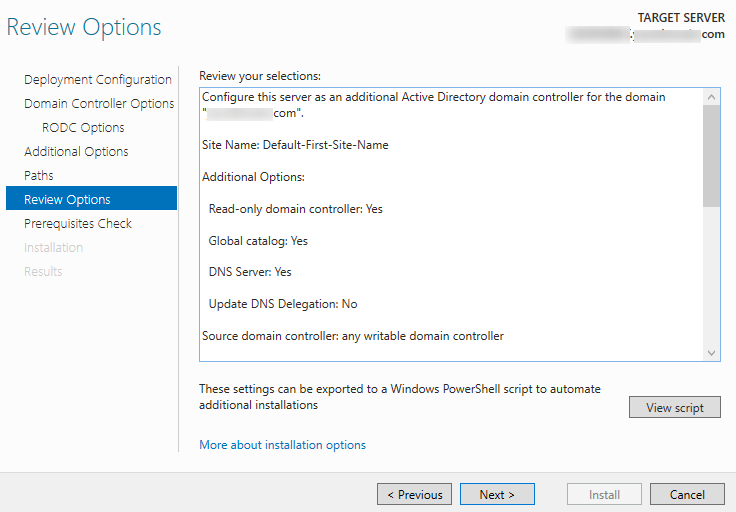
Specify that the DNS server, global catalog (GC), and RODC capabilities must be installed. Then select a site, where the new controller will be located, and the password to access it in DSRM mode.
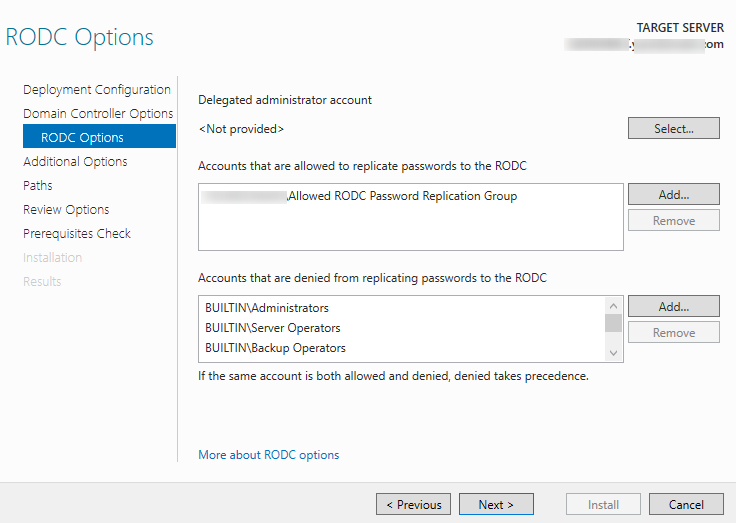
Next, you need to specify the user to whom you want to delegate administrative access to the domain controller, and the list of accounts/groups, whose passwords are allowed or denied from replicating to the RODC (you can do this later).
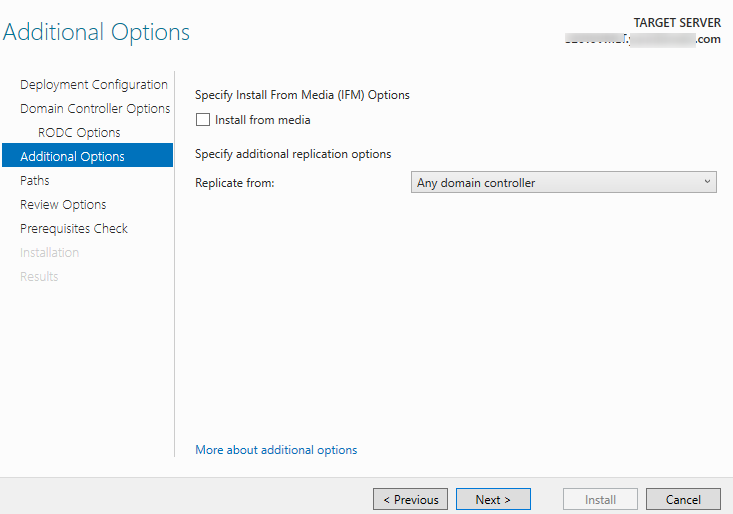
Specify that AD database data can be replicated from any DC.
Replicate from -> Any domain controller
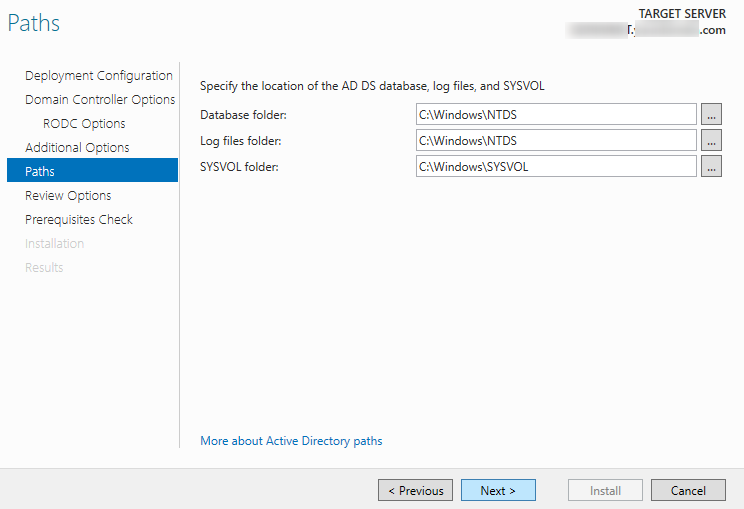
Then specify the paths to the NTDS database, logs, and SYSVOL folder (you can move them to another drive later if necessary).
After you have checked all options, you can install the ADDS role.
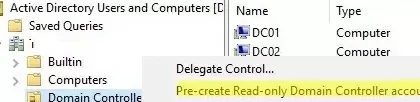
Alternatively, you can deploy RODC using the Staged feature. It consists of pre-creating the RODC computer account in the ADUC console and basic setup. To do this, right-click the Domain Controllers container and select Pre-create a read-only domain controller account.
When installing the ADDS role on a server with the same name, the following message will appear:
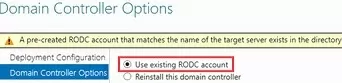
A Pre-created RODC account that matches the name of the target server exists in the directory. Choose whether to use this existing RODC account or reinstall this domain controller.
Select the Use existing RODC account option to use the pre-created RODC object.
After completing the role installation and restarting the server, you will receive an RODC controller. You can check the health of the domain controller.
When the ADUC snap-in (dsa.msc) connects to the RODC, all new AD object create buttons are greyed out. Also, you cannot change the attributes of AD objects on a read-only domain controller. All other actions in the Active Directory console, including search, work as usual.
Deploying a Windows Server Read-Only DC with PowerShell
To deploy a new RODC using PowerShell, you need to install the ADDS role and the PowerShell ADDS module:
Add-WindowsFeature AD-Domain-Services,RSAT-AD-AdminCenter,RSAT-ADDS-Tools
Now you can install the RODC:
Install-ADDSDomainController -ReadOnlyReplica -DomainName woshub.com -SiteName MUN_Branch1_RO_Site -InstallDns:$true -NoGlobalCatalog:$false
After the installation is over, the cmdlet will prompt you to restart your server.
List the DCs in your domain using the Get-ADDomainController cmdlet from the Active Directory PowerShell module:
Get-ADDomainController -Filter * | Select-Object Name,IsReadOnly
The IsReadOnly attribute value for a read-only domain controller must be True.
To list all RODCs in your domain, run:
Get-ADDomainController –filter {IsReadOnly –eq $true}
If you want to pre-create a domain RODC account first (staged deployment), use this command:
Add-ADDSReadOnlyDomainControllerAccount -DomainControllerAccountName MUN-RODC01 -DomainName woshub.com -DelegatedAdministratorAccountName "woshub\mbak" -SiteName MUN_Branch1_RO_Site
When promoting a Windows Server host to a DC, use the command:
Install-ADDSDomainController -DomainName woshub.com -Credential (Get-Credential) -LogPath "C:\Windows\NTDS" -SYSVOLPath "C:\Windows\SYSVOL" -ReplicationSourceDC "MUN-DC01.woshub.com" – UseExistingAccount
RODC Password Replication Policy and Credential Caching
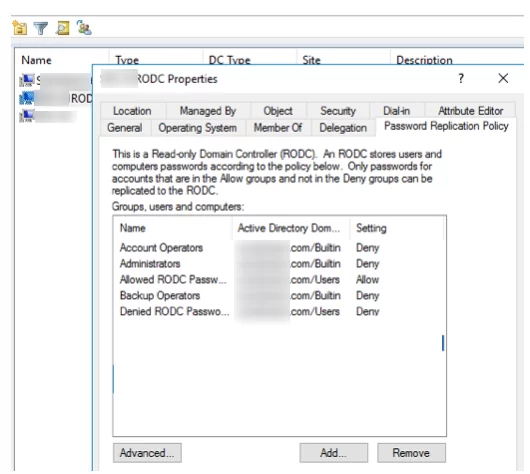
On each RODC you can specify a list of users, computers, and servers, whose password hashes are allowed to or denied from replicating to this domain controller.
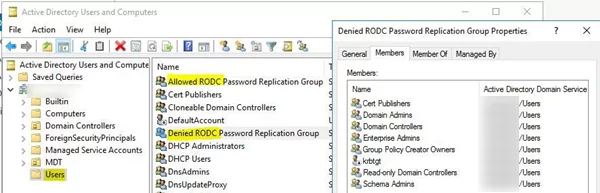
By default, two new global groups are created in the domain:
- Allowed RODC Password Replication Group
- Denied RODC Password Replication Group
By default, the first group is empty, and the second one contains privileged security groups, whose passwords cannot be replicated or cached on the RODC to prevent them from being compromised. By default, the following groups are included here:
- Group Policy Creator Owners
- Domain Admins
- Cert Publishers
- Enterprise Admins
- Schema Admins
- Account krbtgt
- Account Operators
- Server Operators
- Backup Operators
The RODC Password Replication Allowed group typically includes users at the branch office where the RODC is located.
If you are deploying multiple RODCs in a domain, it is best to create such groups for each RODC. You can bind the groups to the RODC in the PasswordReplication Policy tab of the server properties section in the ADUC console.
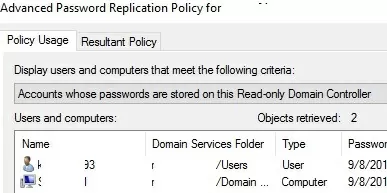
On the Advanced Password Replication Policy for RODC_name, you can view:
- Accounts whose passwords are stored on this Read-Only Domain Controller – a list of users and computers whose passwords are cached on this RODC
- Accounts that have been authenticated to this Read-Only DC– a list of users and computers currently authenticated with this read-only domain controller
On the Resultant Policy tab, you can select a user account and check if its password will be cached on the RODC.
You can manage RODC groups using PowerShell. List users in an AD group:
Get-ADGroupMember -Identity "Denied RODC Password Replication Group" | ft Name, ObjectClass
Add all enabled users from a specific Active Directory Organizational Unit (OU) to the RODC group:
Get-ADUser -SearchBase 'OU=MUN_Branch1,DC=woshub,DC=com' -Filter {Enabled -eq "True"} | ForEach-Object {Add-ADGroupMember -Identity 'Allowed RODC Password Replication Group' -Members $_ -Confirm:$false }
To pre-populate the user password cache from the OU to the RODC, use the following PowerShell script:
$usrs = Get-ADUser -SearchBase 'OU= MUN_Branch1,DC=woshub,DC=com' -Filter {Enabled -eq "True"}
foreach ($usr in $usrs) {
Get-ADObject -identity $usr | Sync-ADObject -Source MUN-DC01 ‑Destination MUN-RODC1 -PasswordOnly
}
You can list the users and computers whose passwords are in the RODC cache:
Get-ADDomainControllerPasswordReplicationPolicyUsage -Identity MUN-RODC1 ‑RevealedAccounts
You cannot remove the password for a specific user from the RODC cache. However, you can invalidate this cache by resetting the user’s password via the ADUC snap-in or with the Set-ADAccountPassword PowerShell cmdlet.