You can use the Get-ADDomainController PowerShell cmdlet to get information about the domain controllers in Active Directory. This cmdlet is a part of PowerShell Active Directory module and requires RSAT installation (onWindows 10 1809 and newer RSAT is installed in a different way).
Get-ADDomainController Cmdlet
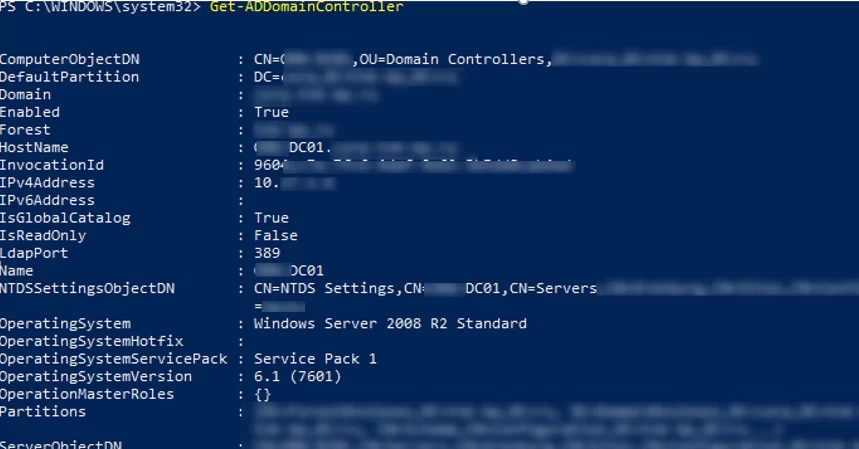
When running Get-ADDomainController without any parameters, the cmdlet displays the information about the current domain controller (LogonServer) used by this computer to get authenticated (the DC is selected according to the AD site an IP subnets topology).
The cmdlet returned all fields with the information about the domain controller available in Active Directory database.
ComputerObjectDN : CN=MunDC01,OU=Domain Controllers,DC=corp,DC=woshub,DC=com
DefaultPartition : DC=corp,DC= woshub,DC=com
Domain : corp.woshub.com
Enabled : True
Forest : woshub.com
HostName : MunDC01.corp.woshub.com
InvocationId : 921234a-2a32-4312-9e12-3b32343ab4ad
IPv4Address : 192.168.1.6
IPv6Address :
IsGlobalCatalog : True
IsReadOnly : False
LdapPort : 389
Name : MunDC01
NTDSSettingsObjectDN : CN=NTDS Settings,CN=MunDC01,CN=Servers,CN=DE,CN=Sites,CN=Configuration,DC=woshub,DC=com
OperatingSystem : Windows Server 2012 R2 Standard
OperatingSystemHotfix :
OperatingSystemServicePack :
OperatingSystemVersion : 6.3 (9600)
OperationMasterRoles : {}
Partitions : {DC=ForestDnsZones,DC=woshub,DC=com, DC=DomainDnsZones,DC=corp,DC=woshub,DC=com, CN=Schema,CN=Configuration,DC=woshub,DC=com...}
ServerObjectDN : CN=MunDC01,CN=Servers,CN=DE,CN=Sites,CN=Configuration,DC=woshub,DC=com
ServerObjectGuid : 8123453-e294-1234-a987-1234535432d6
Site : DE
SslPort : 636
Also, you can find the domain controller, to which your computer should belong via the DCLocator service:
Get-ADDomainController –Discover
You can find the closest available DC with the active AD Web Services role:
Get-ADDomainController –ForceDiscover -Discover -Service ADWS
You can use the Service parameter to find the PDC (or other FSMO role) in your domain:
Get-ADDomainController -Discover -Service PrimaryDC
If your domain controller is not found or not responding, you can find the domain controller on the closest AD site (determined by the weight of intersite links):
Get-ADDomainController –Discover –ForceDiscover -NextClosestSite
To display the list of all domain controllers in the current domain, run this command:
Get-ADDomainController -Filter * | ft
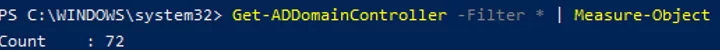
Using this command, you can count the number of domain controllers in AD:
Get-ADDomainController -Filter * | Measure-Object
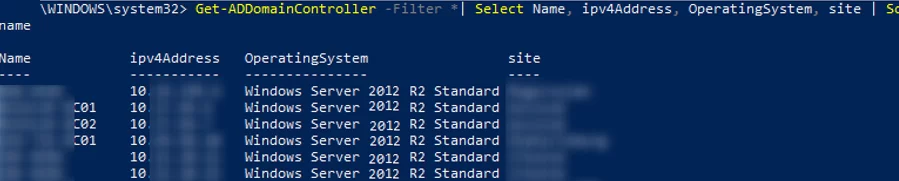
You can display a more convenient table showing all domain controllers, their host names, IP addresses, OS versions and AD site names:
Get-ADDomainController -Filter *| Select Name, ipv4Address, OperatingSystem, site | Sort-Object name
If you want to get some information about a DC from another domain, specify the name of any available DC in another domain using the –Server parameter (it is possible in case of enabling trust relationships between the domains).
Get-ADDomainController -Filter * -server dc01.test.com | Select Name, ipv4Address, IsGlobalCatalog, Site
Using Get-ADDomainController to Find Domain Controllers By Certain Criteria
Let’s consider some useful commands you can use to get the list of domain controllers in AD according to certain criteria.
To find a domain controller by its IP address:
Get-ADDomainController -Identity "192.168.100.6"
To find all DCs that have DC02 in their names:
Get-ADDomainController -Filter {name -like "*dc02*"} | Select Name, ipv4Address, OperatingSystem, site
To find all available DCs on the specific site:
Get-ADDomainController -Discover -ForceDiscover -Site "Site-Name"
To display the list of DCs on the sites, which names begin from Mun*:
Get-ADDomainController -Filter {site -like "Mun*"} | Select Name, ipv4Address, OperatingSystem, site
To display the list of all Read Only domain controllers (RODCs):
Get-ADDomainController -Filter {IsReadOnly -eq $true} | Select Name, ipv4Address, OperatingSystem, site
To find DCs on the “Rome” site with the Global Catalog role enabled:
Get-ADDomainController -Filter {site -eq "Rome" -and IsGlobalCatalog -eq $true} | Select Name, ipv4Address, OperatingSystem, site
PowerShell Script to Check Availability of All Domain Controllers
The next PowerShell script allows to check your domain controllers one-by-one and perform the specific action for each of them:
$DCs = Get-ADDomainController -Filter *
ForEach($DC in $DCs)
{
do something
}
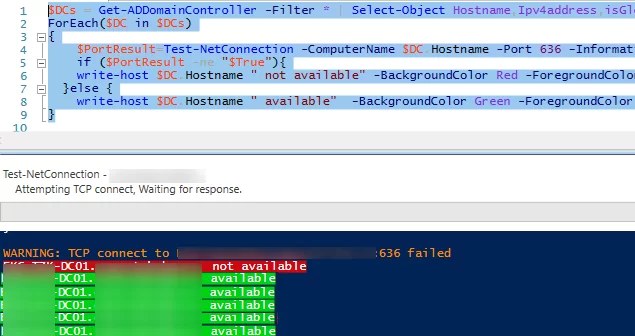
Here is an example of a simple PowerShell script that checks the availability of the LDAPS port (TCP 636) on each DC in your domain using the Test-NetConnection cmdlet. If the LDAPS port is not available, a warning will appear.
$DCs = Get-ADDomainController -Filter * | Select-Object Hostname,Ipv4address,isGlobalCatalog,Site,Forest,OperatingSystem
ForEach($DC in $DCs)
{
$PortResult=Test-NetConnection -ComputerName $DC.Hostname -Port 636 -InformationLevel Quiet
if ($PortResult -ne "$True"){
write-host $DC.Hostname " not available" -BackgroundColor Red -ForegroundColor White
}else {
write-host $DC.Hostname " available" -BackgroundColor Green -ForegroundColor White}
}
We have got a simple script to monitor all DCs availability in your domain.
There are also different scenarios to check all DCs in the domain one-by-one. In previous articles we have shown how to use Get-ADDomainController cmdlet to find the specific event in the logs on all domain controllers. For example, to find a user account lockout events, NTLMv1 authentication events, events of adding a user to an AD security group, etc.
1 comment
Hi Admin,
Thanks a lot for this. Finally, I get the code I needed to check if the status of the Domain Controller is Active or Unavailable. I can only see that thru AD “Change Domain Server” but now with this “Test-NetConnection -ComputerName $DC.Hostname -Port 636” I can check the status via powershell. Thank you so much!