After installing the Windows security updates that issued after May 2018, you may face the CredSSP encryption oracle remediation error during RDP connection to the remote Windows server or computer in the following cases:
- You are trying to connect to the remote desktop of a computer with a recently installed old Windows version (for example, Windows 10 RTM, or build 1709 or older, Windows Server 2012 R2, Windows Server 2016), on which the latest Windows security updates are not installed;
- You are trying to connect via RDP to a computer on which Microsoft updates have not been installed for a long time;
- The remote computer blocked RDP connection because the necessary security updates are missing on your computer.
Let’s try to understand what the RDP error CredSSP encryption oracle remediation means and how to fix it.
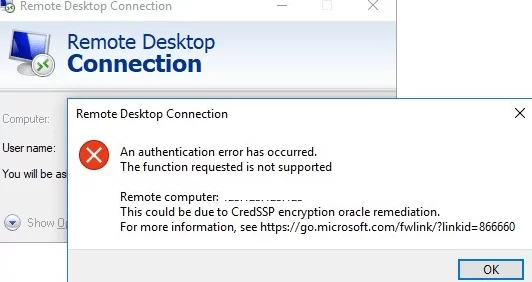
So, when trying to connect to the RemoteApp on RDS servers running Windows Server 2016/2012 R2/2008 R2, or to remote desktops of other users using the RDP protocol (on Windows 10, 8.1 or 7), an error appears:
An authentication error has occurred.
The function is not supported.
Remote Computer: hostname
This could be due to CredSSP encryption oracle remediation.
This error occurs due to the fact that Windows security updates (at least since March 2018) were not installed on remote Windows instance, to which you are trying to connect via RDP.
In March 2018, Microsoft released updates that block remote code execution using a vulnerability in the CredSSP (Credential Security Support Provider) protocol (bulletin CVE-2018-0886). In May 2018, an additional update was published, which by default prevents Windows clients from connecting to remote RDP servers with a vulnerable (unpatched) version of the CredSSP protocol.
Thus, if you have not installed cumulative security updates on your Windows RDS/RDP servers (computers) since March 2018, and May 2018 updates (or newer) were installed on RDP clients, then when you try to connect to RDS servers with an unpatched version of CredSSP an error appears: This could be due to CredSSP encryption oracle remediation.
The RDP error on clients appears after the following security updates are installed:
- Windows 7 / Windows Server 2008 R2 — KB4103718
- Windows 8.1 / Windows Server 2012 R2 — KB4103725
- Windows Server 2016 — KB4103723
- Windows 10 1803 — KB4103721
- Windows 10 1709 — KB4103727
- Windows 10 1703 — KB4103731
- Windows 10 1609 — KB4103723
windows 10 1803 x64 8/*/2019. Download and install the Windows cumulative update (in my example, it is “2019-08 Cumulative Update for Windows 10 Version 1803 for x64-based Systems (KB4512509)”. 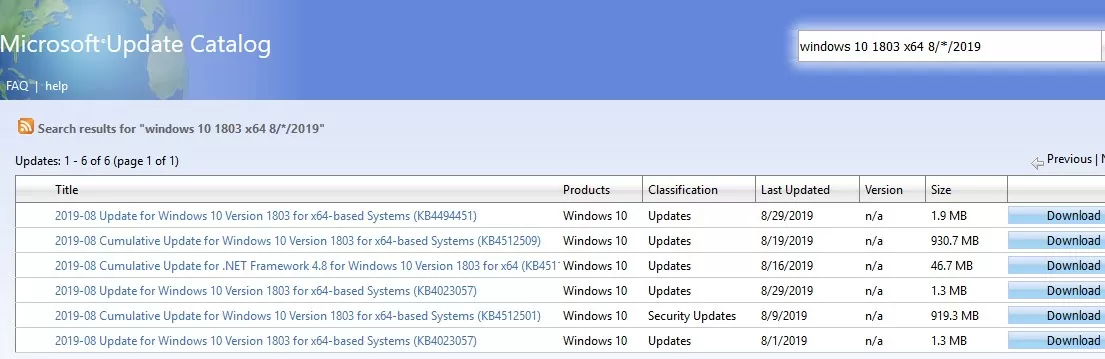
To restore remote desktop connection, you can uninstall the specified security update on the remote computer (but it is not recommended and you should not do this, there is a more secure and correct solution).
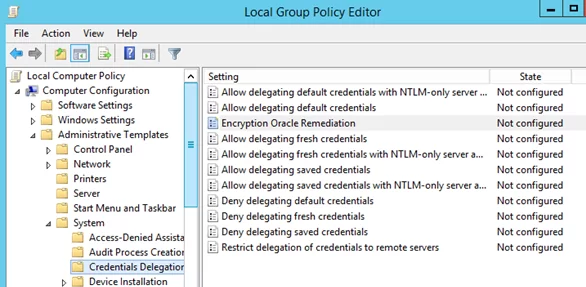
To fix the connection problem, you need to temporarily disable the CredSSP version check on the computer from which you are connecting via RDP. This can be done using the local Group Policy editor.
- Run the local GPO editor: gpedit.msc;
- Go to the GPO section Computer Configuration -> Administrative Templates -> System -> Credentials Delegation;
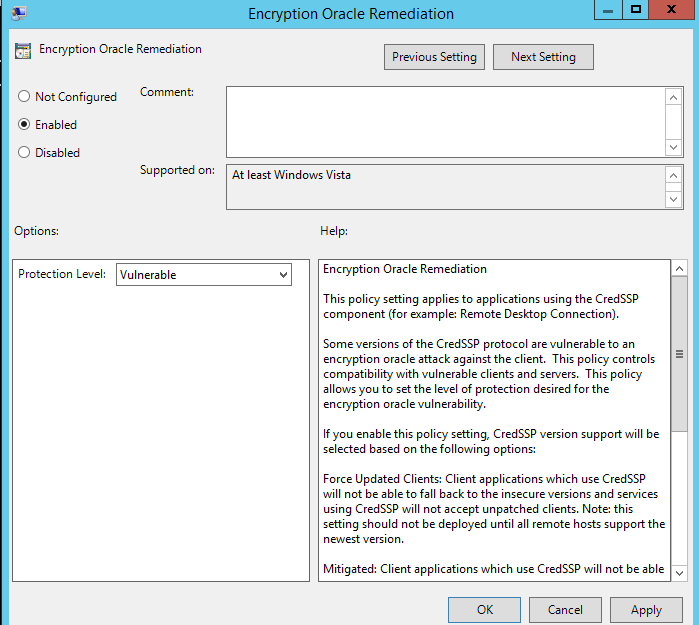
- Locate the policy with the name Encryption Oracle Remediation, enable the policy and set the Protection level to Vulnerable;
- Update the policy setting on the computer (run
gpupdate /forcecommand) and try to connect to the remote server via RDP. With the Oracle Remediation Encryption policy set to Vulnerable, client applications with CredSSP support will be able to connect even to unpatched RDS/RDP endpoints.
- Force Updated Clients — the highest protection level when the RDP server blocks the connection from non-patched clients. Usually, this policy should be enabled after you have completely updated the entire infrastructure and added the latest security updates to the Windows install images for servers and workstations;
- Mitigated — in this mode, an outgoing remote RDP connection to RDP servers with a vulnerable version of CredSSP is blocked. However, other services using CredSSP work fine;
- Vulnerable — the lowest level of protection when connecting to an RDP server with a vulnerable version of CredSSP is allowed.
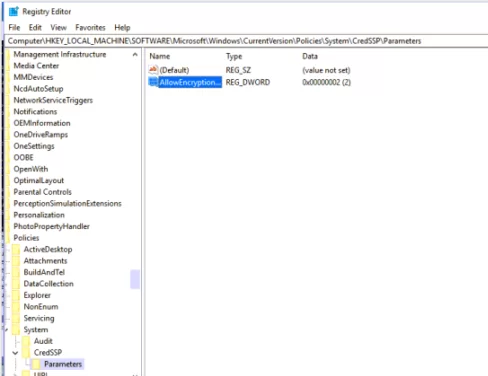
If you do not have a local GPO editor (for example, in Windows Home editions), you can make a directly registry change that allows RDP connection to servers with unpatched version of CredSSP:
REG ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /v AllowEncryptionOracle /t REG_DWORD /d 2
You can change AllowEncryptionOracle registry parameter on multiple computers in AD using a domain GPO or with such a PowerShell script (you can get a list of computers in the domain using the Get-ADComputer cmdlet from the RSAT-AD-PowerShell module):
$computers = (Get-ADComputer -Filter *).DNSHostName
Foreach ($computer in $computers) {
Invoke-Command -ComputerName $computer -ScriptBlock {
REG ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /v AllowEncryptionOracle /t REG_DWORD /d 2
}
}
After successfully connecting to a remote RDP server (computer), you need to install the latest security updates through the Windows Update (verify that the wuauserv service is enabled) or manually. Download and install the latest cumulative Windows updates from the Microsoft Update Catalog website as shown above. If the error “The update is not applicable to your computer” appears when installing the MSU update, read the article using the link above.
After installing the updates and rebooting the server, don’t forget to disable the policy on the clients (either switch it to the Force Updated Clients), or return the value of the AllowEncryptionOracle registry parameter to 0. In this case, your computer will not be at risk of connecting to CredSSP unprotected hosts and exploitation of the vulnerability.
REG ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /v AllowEncryptionOracle /t REG_DWORD /d 0
There is another scenario in which updates are not installed on your computer. For example, the RDP server is updated, but it has a policy that blocks RDP connections from computers with the vulnerable version of CredSSP (Force Updated Clients policy setting). In this case, you will also see the RDP connection error “This could be due to CredSSP encryption oracle remediation”.
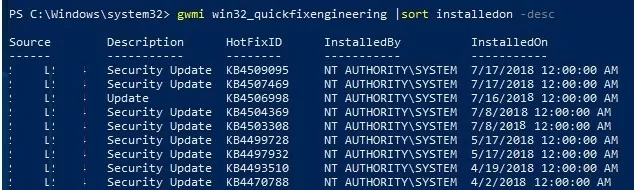
Check the Windows updates last install date on your computer using the PSWindowsUpdate module or through the WMI command in the PowerShell console:
gwmi win32_quickfixengineering |sort installedon -desc
This example shows that the latest Windows security updates were installed on June 17, 2018. Download and install the newer MSU cumulative update file for your Windows edition (see above).
8 comments
Hi,
I have seen that problem yesterday on a server that I can’t update.
What I did to fix for the client to be able to connect to the server was to deselect the box “Allow connections only from computers running Remote Desktop with Network Level Authetication (recommended)”.
Hi,
Thanks for the info! Please clarify:
Have you disabled NLA on the server side?
Do you use Windows Server 2003 / Win XP or something similar as an RDP server?
What is the Windows version on the client? Did you enable the policy Oracle Remediation Encryption = Vulnerable on the client computer?
RADJ,
Sorry… I’ve just seen your reply…
Q: Have you disabled NLA on the server side? A: Yes
Q: Do you use Windows Server 2003 / Win XP or something similar as an RDP server? A: No
Q: What is the Windows version on the client? A: Windows 7
Q: Did you enable the policy Oracle Remediation Encryption = Vulnerable on the client computer? A: No
As the server can’t be updated, it doesn’t has that group policy to configure…
So the quick fix was to deselect that box.
In this other site I saw a regedit solution:
http://jermsmit.com/credssp-encryption-oracle-remediation/
Is there a solution how to connect to the RDS farm from a computer running Windows XP Sp3?
Most likely the AllowEncryptionOracle = 2 registry parameter on computers with Windows XP will not work. Most likely, to connect to RDS from clients on XP, you need to switch the Encryption Oracle Remediation policy to the Mitigated/ Vulnerable level on terminal servers. However, the RDS server will be vulnerable to the exploitation of the CredSSP vulnerability (CVE-2018-0886). You will also have to disable the Network Level Authentication on RDS server (however, there is also a workaround for enabling NLA in Windows XP SP3). Those, it should be used only as a temporary solution, until you update the OS on clients to Windows 10 / 8.1 / 7.
You can also connect via windows 10 ‘remote desktop’ app .. just to get you in and run updates
thanks it work in my win 10 home
Please sync your time and location first