In this article, we’ll look at the Active Directory domain administrator password reset scenarios. You may need it in cases where domain administrator privileges have been lost due to forgetfulness or deliberate sabotage by a retiring administrator, a hacker attack, etc. To successfully reset a domain administrator password, you must have physical or remote access to the AD domain controller console (iLO, iDRAC, or VMware vSphere/Hyper-V/Proxmox console when using a virtual DC).
In this example, we are going to reset the administrator password on a domain controller that is running Windows Server 2019. If there is more than one domain controller on the network, you can reset the Domain Admin password on any of them.
How to Reset a Lost Domain Administrator Password If You Don’t Know DSRM Password?
Boot your server from any Windows installation media (this can be a Windows installation USB stick or an ISO image):
- Press
Shift+F10to open the command prompt on the Windows Setup screen; - Now you need to know the letter assigned to the partition where your Windows Server is installed. Run the command:
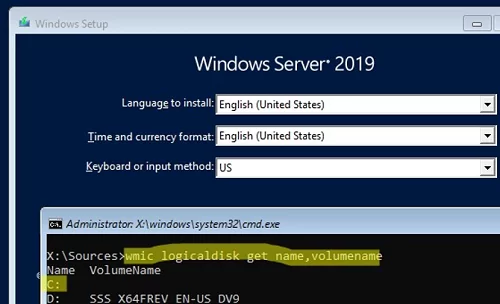
wmic logicaldisk get volumename,name
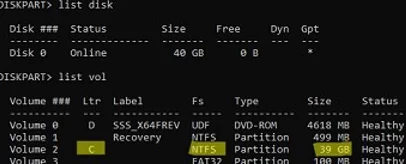
In my example, you can see that my offline Windows Server image is on C:. This is the drive letter we will use in the following commands.You can also identify discs in Windows using diskpart:diskpart->list disk->list vol - Backup the original utilman.exe file:
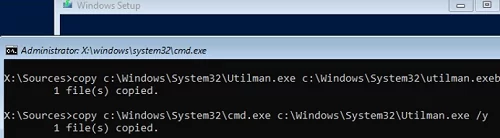
copy C:\windows\system32\utilman.exe C:\windows\system32\utilman.exebak - Then replace the utilman.exe file with the cmd.exe:
copy c:\windows\system32\cmd.exe c:\windows\system32\utilman.exe /y
- Extract the boot image (USB/ISO) and reboot your host:
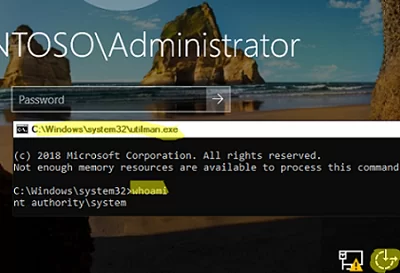
wpeutil reboot - After the domain controller has been booted, click the ‘Easy Access’ button on the login screen. This will open a command prompt;
- Run the
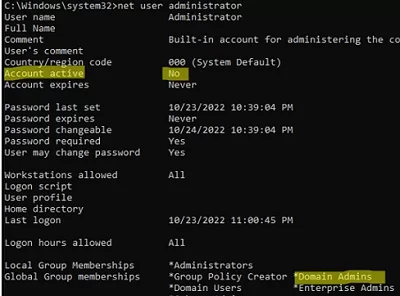
whoamicommand to make sure that the command prompt is running as NT Authority\SYSTEM; - List information about the Administrator account:
net user administrator - In this example, you can see that this user is a member of the Domain admins group and is now disabled:
Account active: No
- Enable the domain administrator account:
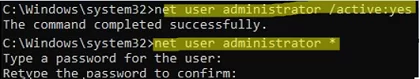
net user administrator /active:yes - You can now reset your domain administrator password:
net user administrator *
Set a new administrator password (the new password must match the domain password policy);. - Boot your server from the installation media again and replace utilman.exe with the original file (to avoid leaving a security hole in the server):
copy c:\windows\system32\utilman.exebak c:\windows\system32\utilman.exe /y - Restart your domain controller in the normal mode and make sure that you can now log on to your DC using the new domain administrator password.
Resetting the Domain Admin Password on a Virtualized Domain Controller
If you have a virtualized domain controller running on any hypervisor (ESXi, Hyper-V, Proxmox), you can use the DSInternals PowerShell module to reset the administrator password.
To do it:
- Shut down the VM running the AD DS role (domain controller) and connect its virtual drive (vhdx, vmdk, etc.) to any other VM running Windows. Assign it a drive letter, for example,
E:; - Install the DSInternals module from the PowerShell Gallery:
Install-Module DSInternals –ForcePowerShell modules can be installed offline when an Internet connection is not available. - Get a boot key used to encrypt password hashes in your AD database (ntds.dit):
$bootkey= Get-BootKey -SystemHiveFilePath "E:\Windows\System32\config\SYSTEM" - You can now obtain information about any user account in the AD database:
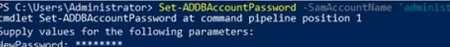
Get-ADDBAccount -SamAccountName 'Administrator' -DBPath "E:\Windows\NTDS\ntds.dit" -BootKey $bootkey - If the domain administrator account is disabled, enable it and set a new password:
Enable-ADDBAccount -SamAccountName 'Administrator' -DBPath "E:\Windows\NTDS\ntds.dit"
Set-ADDBAccountPassword -SamAccountName 'administrator' -DBPath "E:\Windows\NTDS\ntds.dit" -BootKey $bootkey
- Disconnect the virtual drive, re-connect it to the source VM, and power on the domain controller;
- After that, the new domain administrator password will be replicated to all DCs.
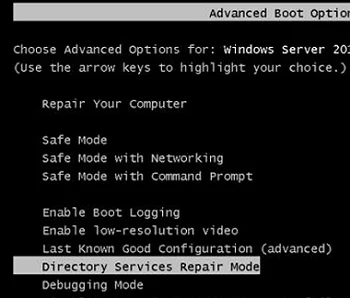
Reset Domain Administrator Password from DSRM
If you know the DSRM administrator password, you can boot your DC into DSRM by selecting the appropriate option from the Advanced Boot Options menu.
Enter the local user name (administrator) and the password (DSRM password) on the logon screen.
In this example, the domain controller name is DC01.
Let’s check which user is logged into the system by running the command:
whoami /user
USER INFORMATION ---------------- User Name SID ================== ============================================ dc01\administrator S-1-5-21-3244332244-312345677-2454632109-500
As you can see, we are logged in as the local admin user.
The next step is to change the Active Directory administrator password (by default, the account is also called Administrator). To reset the password of the domain administrator, we are going to create a service that will reset the password of the administrator account under SYSTEM:
sc create ResetADPass binPath= "%ComSpec% /k net user administrator P1SSsw0rd21!" start= auto
Ensure that the service has been created:
sc qc ResetADPass
[SC] QueryServiceConfig SUCCESS SERVICE_NAME: ResetADPass TYPE : 10 WIN32_OWN_PROCESS START_TYPE : 2 AUTO_START ERROR_CONTROL : 1 NORMAL BINARY_PATH_NAME : C:\Windows\system32\cmd.exe /k net user administrator P@ssw0rd1 LOAD_ORDER_GROUP : TAG : 0 DISPLAY_NAME : ResetADPass DEPENDENCIES : SERVICE_START_NAME : LocalSystem
Restart the domain controller in the normal mode:
shutdown -r -t 0
On startup, the service we’ve created changes the Domain Admin password to P1SSsw0rd21!. Use this account and password to log in to the DC.
whoami /user
USER INFORMATION ---------------- User Name SID ===================== ============================================ corp\administrator S-1-5-21-1737425439-23123122-1234318981-500
Then delete the Windows service that we have just created:
sc delete ResetADPass
[SC] DeleteService SUCCESS
In this article, we have a look at how you can reset the password of an AD domain administrator. We would like to reiterate the importance of ensuring the physical security of your IT infrastructure. If someone other than authorized personnel has local access to your physical host running your domain controllers, they can easily reset any user or administrator password. If you need to deploy DC in less trusted locations, it is recommended that you use a read-only domain controller (RODC) feature.