Quite an often task of an Active Directory administrator is to make a list of disabled or inactive user and/or computer accounts. You can use both saved LDAP queries in the ADUC console and PowerShell cmdlets to get a list of inactive objects in an Active Directory domain. In this article, we’ll show you how to use PowerShell to find inactive user and computer accounts.
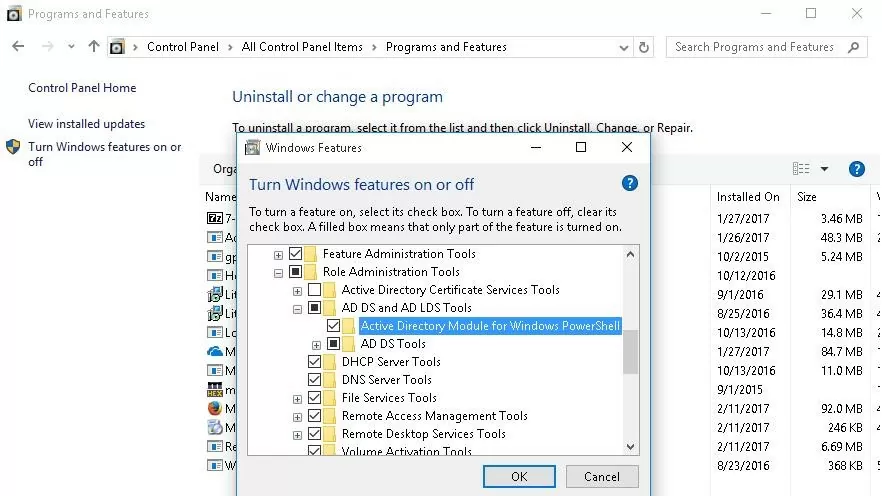
In order to use all the PowerShell cmdlets discussed below, at least PowerShell version 3.0 and the Remote Server Administration Toolkit (RSAT) must be installed on the computer. Enable the Active Directory Module for Windows PowerShell from RSAT (Control Panel -> Programs-> Turn Windows Features on and off-> Remote Server Administration Tools -> Role Administration Tools -> AD DS and AD LDS Tools).
This PowerShell module can also be enabled using this command:
Add-WindowsFeature RSAT-AD-PowerShell
Start the PowerShell console and import Active Directory for PowerShell module:
Import-Module ActiveDirectory
How to Find Inactive (Old) Computers in Active Directory Domain?
You can use the Get-ADComputer cmdlet to find inactive computer objects in a domain. The LastLogonTimeStamp attribute can be used as search criteria. Note that this attribute cannot be used to retrieve real-time information about the last time a computer logged on to the domain. However, due to the fact that this attribute is replicated between DCs every 9-14 days, you can get information about the last computer logon time from any domain controller (unlike the LastLogonDate attribute, which is updated only on the DC through which the computer logged in).
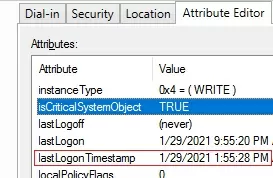
You can check the current value of the LastLogonTimeStamp attribute in the computer properties in the ADUC console on the Attributes Editor tab.
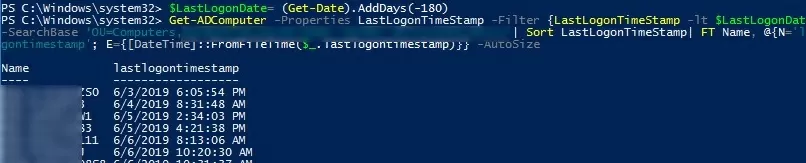
Use the following commands to find all computers in a specific OU that have not been logged on for more than 180 days:
$LastLogonDate= (Get-Date).AddDays(-180)
Get-ADComputer -Properties LastLogonTimeStamp -Filter {LastLogonTimeStamp -lt $LastLogonDate } -SearchBase ‘OU=Computers,OU=Mun,DC=woshub,dc=com’| Sort LastLogonTimeStamp| FT Name, @{N='lastlogontimestamp'; E={[DateTime]::FromFileTime($_.lastlogontimestamp)}} -AutoSize | Export-CSV c:\ps\inactive_computers.csv
This command will generate a CSV file with a list of inactive computers that have not been registered on the domain for more than six months.
You can disable the found computer accounts:
Get-ADComputer -Properties LastLogonTimeStamp -Filter {LastLogonTimeStamp -lt $LastLogonDate } -SearchBase ‘OU=Computers,OU=Mun,dc=woshub,dc=com’| Disable-ADAccount
Move these computer objects to a separate OU:
Get-ADComputer ... | Move-ADObject -TargetPath “OU=Disabled Computers,DC=woshub,DC=com”
Or delete inactive computers:
Get-ADComputer ... | Remove-ADComputer
Find Inactive User Accounts in Active Directory
You can also use the lastLogonTimeStamp attribute to find inactive user accounts. To build a list of inactive users, you need to use this attribute, and not lastLogon (the lastLogon attribute is not replicated between domain controllers).
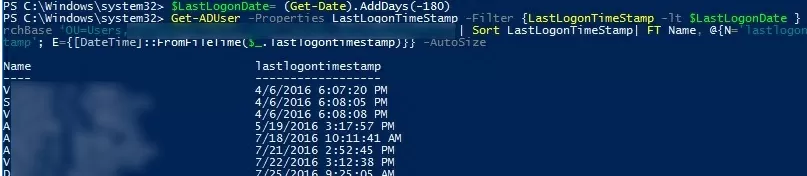
The following script allow to select enabled user accounts that have not logged into the domain for more than six months (180 days) using the Get-ADUser cmdlet:
$LastLogonDate= (Get-Date).AddDays(-180)
Get-ADUser -Properties LastLogonTimeStamp -Filter {LastLogonTimeStamp -lt $LastLogonDate } -SearchBase ‘OU=Users,OU=Mun,dc=woshub,dc=com’| ?{$_.Enabled –eq $True} | Sort LastLogonTimeStamp| FT Name, @{N='lastlogontimestamp'; E={[DateTime]::FromFileTime($_.lastlogontimestamp)}} -AutoSize | Export-CSV c:\ps\inactive_users.csv
You can disable inactive users :
Get-ADUser -Properties LastLogonTimeStamp -Filter {LastLogonTimeStamp -lt $LastLogonDate } -SearchBase ‘OU=Users,OU=Mun,dc=woshub,dc=com’| Disable-ADAccount
If you need to remove inactive user accounts from AD, use the pipeline with Remove-ADUser.
Using Search-ADAccount to Find Inactive AD Objects
You can use the Get-ADUser, Get-ADComputer, or Get-ADObject cmdlets to find inactive objects in AD. However, creating the correct filter for these commands can be tricky. The ActiveDirectory PowerShell module has a more convenient cmdlet for performing these tasks – Search-ADAccount. This cmdlet is used to find objects of any type (both users and computers). Let’s look at examples of using the Search-ADAccount cmdlet for typical tasks of searching for disabled, inactive, and locked objects in AD.
Here is the list of the most important keys of Search-ADAccount cmdlet:
| Search-ADAccount Key | Description |
-AccountDisabled | Search of disabled accounts |
-AccountExpired | Search of expired accounts |
-AccountExpiring [-DateTime DateTime] [-TimeSpan TimeSpan] | Search of the accounts to be expired in a certain period of time (-TimeSpan) or on a specific date (-DateTime) |
-AccountInactive [-DateTime DateTime] [-TimeSpan TimeSpan] | Search of the accounts not logged in since a certain date (-DateTime) or during a certain period of time (-TimeSpan) |
-LockedOut | Search of the accounts locked by the domain password policy |
-PasswordExpired | Search of the accounts with the expired passwords |
-PasswordNeverExpires | Accounts with the PasswordNeverExpires attribute set (UserAccountControl attribute) |
For example, let’s display the list of disabled user accounts in domain:
Search-ADAccount -UsersOnly –AccountDisabled
You can limit the search scope to a specific Active Directory container (OU):
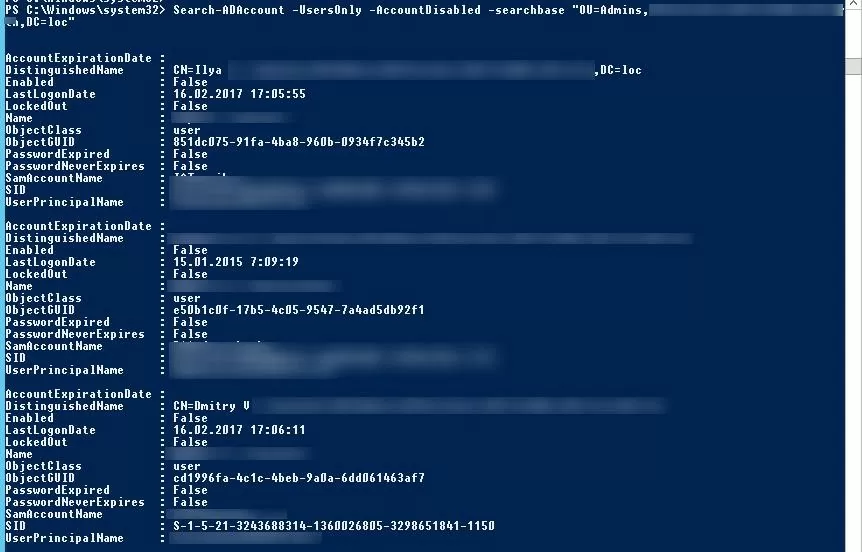
Search-ADAccount -UsersOnly –AccountDisabled –searchbase "OU=Admins,OU=Accounts,DC=woshub,DC=com"
The same data can be presented in a more convenient table form using this command:
Search-ADAccount -UsersOnly -AccountDisabled -searchbase "OU=Admins,OU=Accounts,DC=woshub,DC=com"|ft -AutoSize
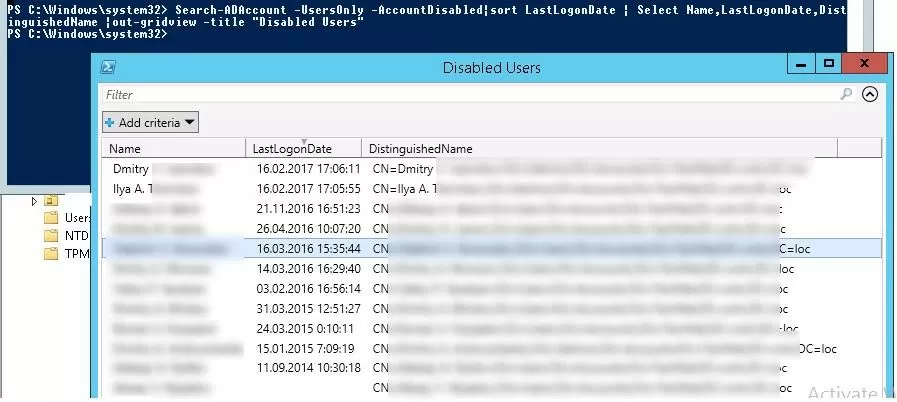
If you need to get the list of the disabled users containing certain user attributes and present it as a graphic table to be sorted, run the following:
Search-ADAccount -UsersOnly AccountDisabled |sort LastLogonDate | Select Name,LastLogonDate,DistinguishedName |out-gridview -title "Disabled Users"
The list of locked user accounts:
Search-ADAccount -UsersOnly –LockedOut
The list of user accounts that have been inactive in the last 60 days:
$timespan = New-Timespan –Days 60
Search-ADAccount –UsersOnly –AccountInactive –TimeSpan $timespan | ?{$_.Enabled –eq $True}
To count these user accounts:
Search-ADAccount –UsersOnly –AccountInactive –TimeSpan $timespan | ?{$_.Enabled –eq $True} | Measure
The list of computers not registered in the domain network for the last 90 days:
Search-ADAccount -AccountInactive –ComputersOnly -TimeSpan 90
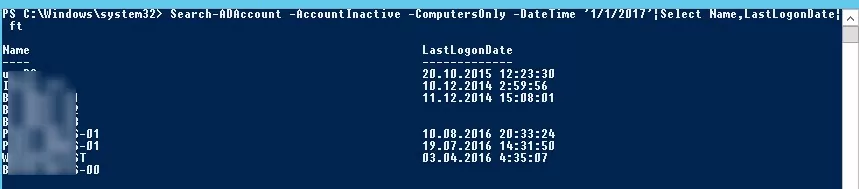
Or since a certain date:
Search-ADAccount -AccountInactive -ComputersOnly -DateTime ‘1/1/2021’|Select Name,LastLogonDate| ft
To export the object list to a CSV, use this command:
Search-ADAccount -AccountDisabled -UsersOnly| Export-Csv "c:\ps\disabled_users.csv"
1 comment
This is very useful PowerShell cmdlet, you can get a lot of information from it.
But if you are not so advanced PowerShell user then I can recommend my free Active Directory reporting tool
There you can much easier generate inactive, disabled, password expired, password will expire in X days and much more reports.