Today we’ll deal with the configuration peculiarities of Java SE centralized security settings on corporate computers using Windows group policies (GPO). These policies should prevent downloading and running untrusted Java applets and ActiveX objects on corporate computers.
The main requirements to the group policies of managing Java security settings:
- A policy should apply only to the machines with Java 6 or Java 7 installed
- Users should still have an opportunity to view current settings in Java Control Panel
- The current Java config files should be stored in the domain controllers and replicated between them
- At least 2 policies should be created: the first should completely block Java in the browsers, and the second — prevent the launch of unsigned applets.
[accordion]
[tab title=”Contents of this article”]
[/tab]
[/accordion]
WMI Filter to Select Computers with Java
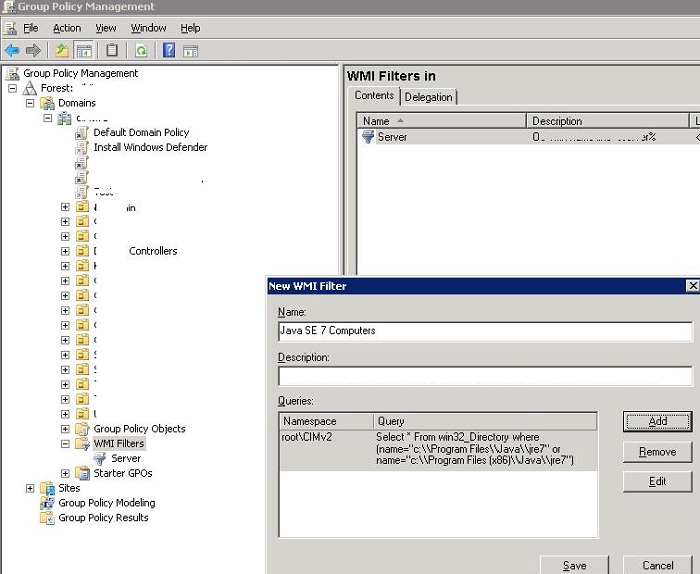
To apply a group policy of Java management only to computers with Java environment installed, create a special WMI filter (More on WMI filtering in group policies).
To do it, open the Group Policy Management Console and create a new WMI filter with the name Java SE 7 Computers in WMI filters section. In the description field, write something like “For Policies that will only apply for hosts running Java SE 7″ and use the following WMI WQL query:
SELECT * FROM win32_Directory WHERE (name="c:\\Program Files\\Java\\jre7" OR name="c:\\Program Files (x86)\\Java\\jre7")This filter will look for Java\jre7 folder in Program Files (x86 and x64) with WMI Query and if found it will apply the policy to these computers.
The same WMI filter should be created for Java 6 (we look for jre6 directory)
Creating Java Configuration Files
Our task is to create two Java security policies. One of them will completely block Java in all browsers, and the other configures some of Java security settings.
To store Java configuration files in the sysvol folder in the domain controller (e.g., \\woshub.com\sysvol\woshub.com\scripts\Java), create two folders:
- Java7Restrict – contains configuration files for special Java security settings
- Java7Block – is a directory for config files that block Java in browsers
To configure Java SE settings, we need deployment.config file. In this config file using deployment.system.config option, specify the path to deployment.properties, which determines Java settings for all users of the system (this file should be located in %windir%\Sun\Java\Deployment\deployment.config directory and is not created during installation by default). The path can point to the URL (HTTP or HTTPS) or a file path UNC to deployment.properties. Not to load individual Java settings for different users, set the option deployment.system.config.mandatory=true.
The file deployment.config for Java7Restrict policy can be as follows:
deployment.system.config=file\://woshub.com/SYSVOL/woshub.com/scripts/Java/Java7Restrict/deployment.properties
deployment.system.config.mandatory=true
The file deployment.properties can also look like that (we assume that Java security level should be set to Very High and the other Java security settings are blocked)
deployment.security.level=VERY_HIGH
deployment.security.level.locked
deployment.security.askgrantdialog.notinca=false
deployment.security.askgrantdialog.notinca.locked
deployment.security.notinca.warning=true
deployment.security.notinca.warning.locked
Create files with the indicated contents in \\woshub.com\sysvol\woshub.com\scripts\Java\Java7Restrict folder.
Create configuration files for the policy that blocks Java in all browsers as well. To do it, add the following strings to deployment.properties
deployment.webjava.enabled=false
deployment.webjava.enabled.locked
Creating Group Policies to Manage Java Settings
Let’s go directly to creating group policies that distribute Java security settings to all computers in your company.
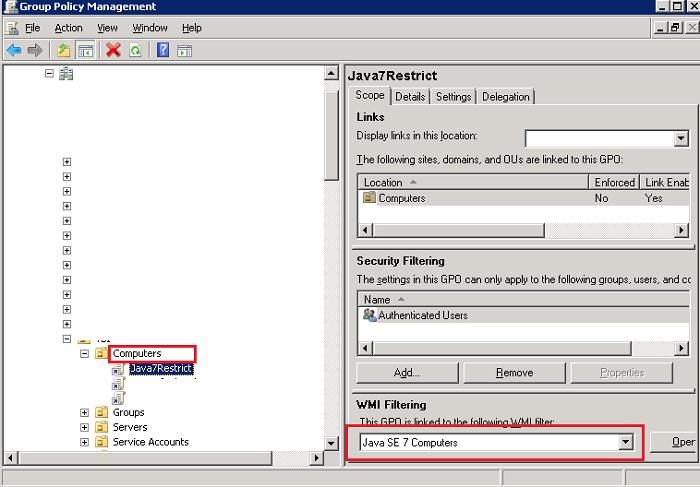
Create a new GPO object (a policy) with the name Java7Restrict.
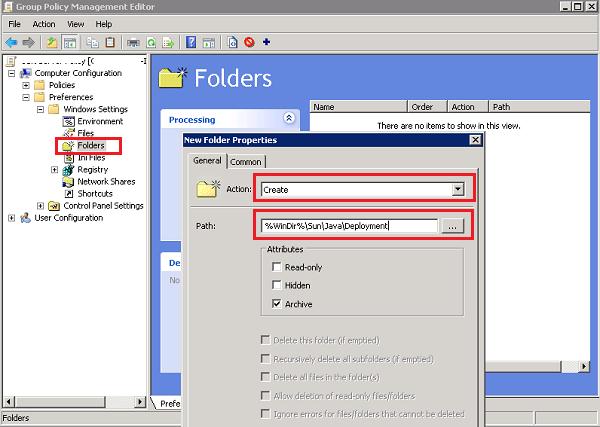
Using GPP (Group Policy Preferences), we have to create a folder to store configuration files with Java settings on user computers. To do it, create a new item in GPO Computer Configuration –> Preferences –> Windows Settings –> Folders with the following settings:
- Action: Create
- Path: %WinDir%\Sun\Java\Deployment
Then you have to copy the deployment.config file to the user computer. To do it, create a new entry in GPO Computer Configuration –> Preferences –> Windows Settings –> Files with the following settings:
- Action: Replace
- Source file: \\woshub.com\sysvol\woshub.com\scripts\Java\Java7Restrict\deployment.config
- Destination file: %windir%\Sun\Java\Deployment\deployment.config.
Now you only have to select Java SE 7 Computers we have created earlier as the WMI filter and link (assign) a policy to the corresponding AD container (OU).
After you applied the policies on the user computers, open Java Control Panel and make sure that Java security level is set to Very High, and other options are inactive so that the users can’t edit them.
If a user tries to load a self-signed applet or one not in your trusted signature file, a window with the following warning appears:
Use the same method to create the second policy Java7Deny to completely block Java in browsers. After the policy is applied, the following notification appears when trying to run Java applet in any browser:
Your security settings have blocked a self-signed application from running.
Today there are a lot of serious security issues of Java applets, many 0day Java vulnerabilities and exploits. So the network administrator and security services should pay much attention to the issues of Java security. In large networks, it is easier to implement it using Windows GPOs.