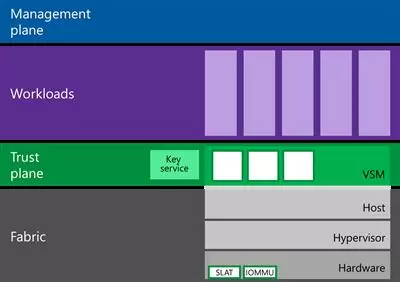
In Windows 10 Enterprise (only in this edition), a new Hyper-V component has appeared – Virtual Secure Mode (VSM). VSM is a protected container (virtual machine) run on a hypervisor and separated from host Windows 10 host and its kernel. Crucial from the security point of view system components run inside this protected virtual container. No third-party code can be executed in the VSM, and code integrity is constantly checked for modification. This architecture allows to protect data in the VSM, even if the kernel of the host Widows 10 is compromised, because even the kernel cannot access the VSM directly.
VSM container cannot be connected to the network and nobody can get administrative privileges in it. Encryption keys, user authentication data and other crucial information from the compromise point of view can be stored in Virtual Secure Mode container. Thus, a hacker won’t be able to penetrate the corporate structure using locally cached data of the domain user accounts.
The following system components can work inside the VSM:
- LSASS (Local Security Subsystem Service) is a component responsible for authentication and isolation of local users. (Thus, the system is protected from the attacks of “pass the hash” type and such tools, like mimikatz link.) It means that the passwords (and/or hashes) of user registered in the system cannot become available even for a user with local administrator privileges.
- Virtual TPM (vTPM) is a synthetic TPM device for guest machines necessary for encryption of disk contents
- The system for monitoring the OS code integrity protects the code against modification
To use VSM, the environment has to meet the following hardware requirements:
- UEFI, Secure Boot and Trusted Platform Module (TPM) support for secure key storage
- Hardware virtualization support (VT-x, AMD-V or later)
How to Enable Virtual Secure Mode (VSM) in Windows 10
Let’s see how to enable Virtual Secure Mode Windows 10.
- UEFI Secure Boot must be enabled.
- Windows 10 has to be included in the domain. (VSM protects only domain user accounts, not local ones.)
- Hyper-V role has to be installed in Windows 10. (In our case, we had to install Hyper-V Platform first, and then we installed Hyper-V Management Tools)
- Virtual Secure Mode (VSM) has to be enabled in a special policy in the Group Policy Editor (gpedit.msc): Computer Configuration -> Administrative templates -> System -> Device Guard -> Turn on Virtualization Based Security. Enable this policy and select Secure Boot option in Select Platform security level. Also check Enable Credential Guard (LSA isolation) here.
- And the last thing to do is to configure BCD to start Windows 10 in the VSM:
bcdedit /set vsmlaunchtype auto
- Restart your computer
How to Make Sure That the VSM Is On
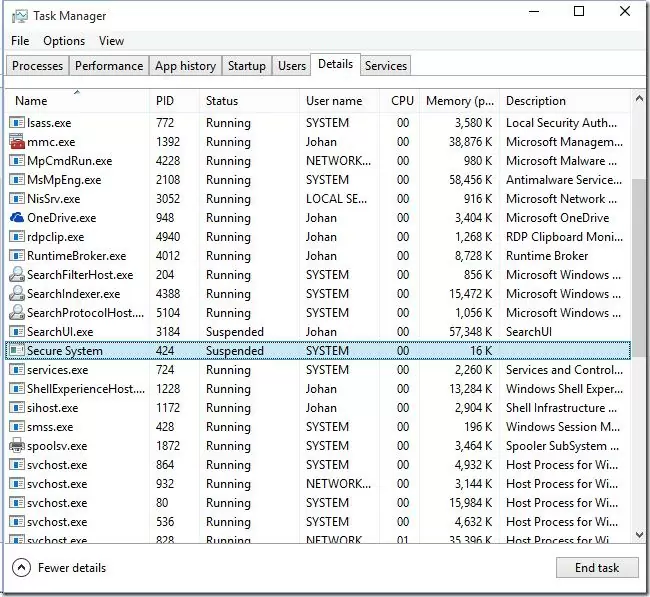
You can make sure that the VSM is active if Secure System process is present in the Task Manager.
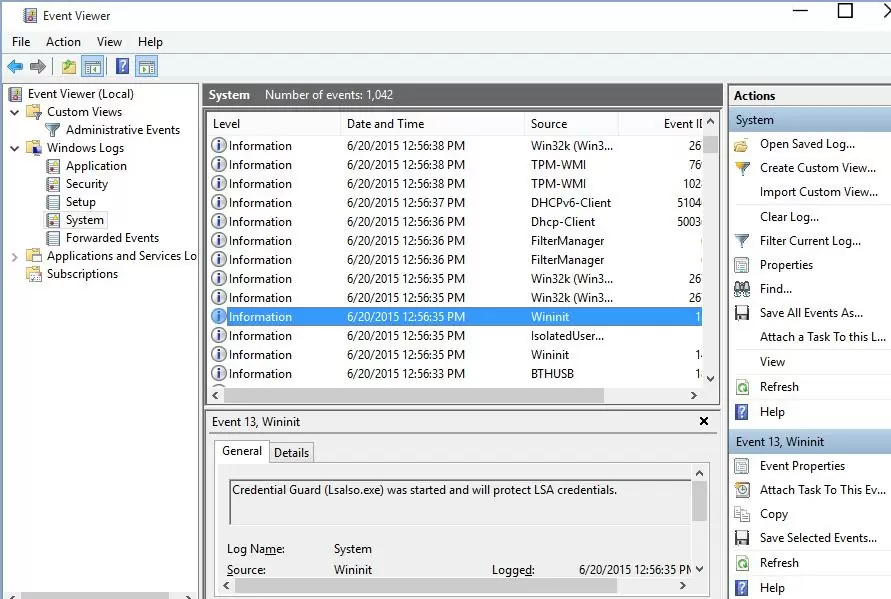
Or if there is the event “Credential Guard (Lsalso.exe) was started and will protect LSA credential” in the system log.
How to Test VSM Security
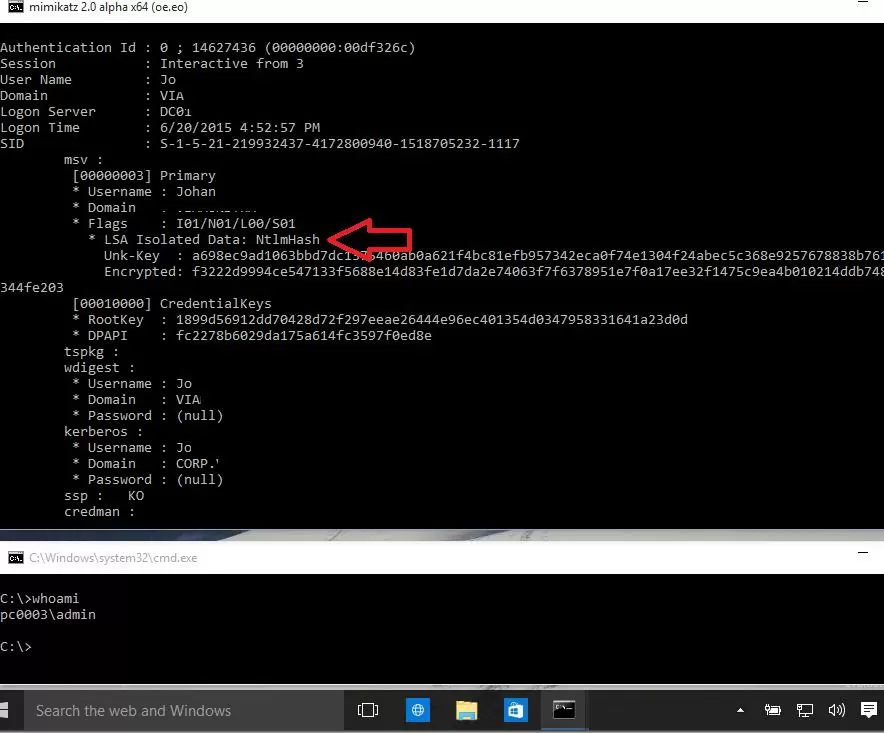
Log in with a domain account to the machines with the VSM enabled and run the following mimikatz command with the local administrator privileges:
mimikatz.exe privilege::debug sekurlsa::logonpasswords exitWe can see that LSA is running in an isolated environment and user password hashes cannot be obtained.
If you do the same on a machine with the VSM disabled, we can get NTLM hash of a user password, which can be used in pass-the-hash attacks.
Ref: Enabling Virtual Secure Mode (VSM) in Windows 10 Enterprise Build 10130



2 comments
Nice article,
But I did notice you “borrowed” some screenshots from me without asking…
/ Johan Arwidmark
Hi, John.
I added a link on your post