Microsoft Graph API allows you to access any objects in the Azure AD (Microsoft 365) tenant using a single REST API point (https://graph.microsoft.com). You are likely to think that it may be interesting to web developers only, but it is quite the other way round. Some data, objects, or resource properties in Microsoft 365 can only be accessed through Microsoft Graph. To collect analytic data, statistics, or other information, an Azure administrator has to use Microsoft Graph.
In this article, we’ll show you how to register your app in Azure AD, get an authentication token, connect to different Microsoft 365 resources (Azure AD, Office 365, Intune, SharePoint, Teams, OneNote, etc.) using RESTful and PowerShell Invoke-RestMethod cmdlet. You can use Microsoft Graph both to get data and manage objects in Azure.
Registering Microsoft Graph Application on Azure AD
To access resources in your Azure tenant using Microsoft Graph, you need to create a new Azure AD app and allow it to access different Azure objects.
- Sign-in to the Azure portal https://portal.azure.com/
- Go to Azure Active Directory -> App registration;
- Create a new app (New registration);
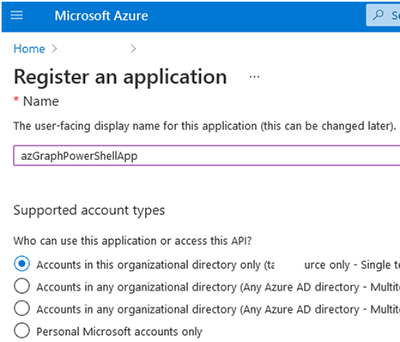
- Enter the name of your app: azGraphPowerShellApp, select who can use the app:
Accounts in this organizational directory only (tenantname only - Single tenant)and click Register;
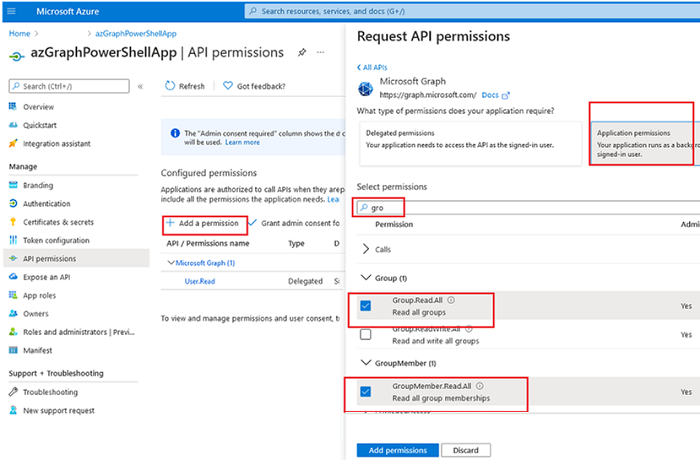
- Then select what Azure resources your application is allowed to access. Go to the API permissions section;
- By default, an app is allowed to read data about a current AzureAD user only (
User.Read). We will grant it read permissions on all properties of Microsoft 365 users and groups; - Click Add a permission, select Microsoft Graph;
- There are two basic permission types in Microsoft Graph (Delegated permission – when something is done on behalf of a user who runs an app and Application Permission – when an app is called by an external script). Select Application Permission;
- In the list that appears, you can select what permissions you will assign to your application to access Azure resources and objects. In my example, I have added Group ->
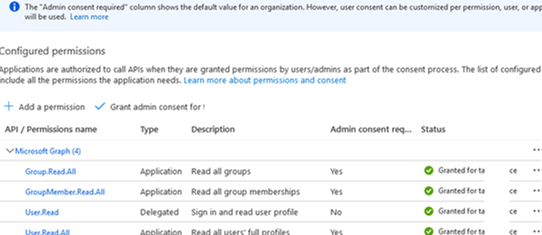
Group.Read.All, GroupMember ->GroupMember.Read.All, User ->User.Read.All(if you want your app to read any data in your tenant, selectDirectory.Read.All);
- Click Grant admin consent to grant access on behalf of the administrator.
To authenticate in an app, you can use a certificate or a secret. A secret is an automatically generated password. The username is an app ID. Let’s create a secret for your app.
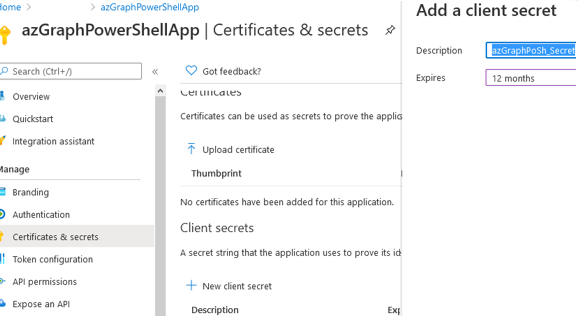
- Open Certificates & secrets -> New client secrets;
- Enter the key name and set its validity time(I have specified 12 months);
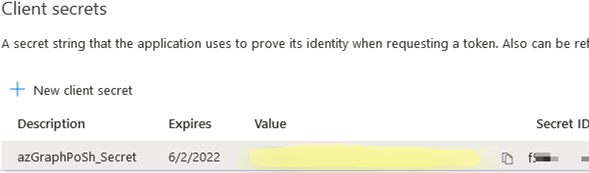
- Copy the value from the Value field (it is the password for the app). Save the password in the Azure Key Vault or in your password manager, since after you exit the app, the password value will be hidden (you will have to create the secret again);
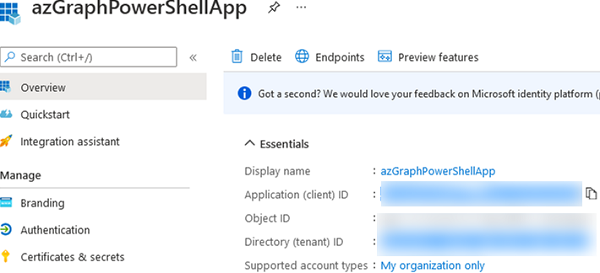
- Then copy your app ID (Application client ID) and Azure tenant ID (Directory tenant ID).
Paste your values to PowerShell variables:
$ApplicationID = "1111111-1111-1111-1111-11111111111"
$TenatDomainName = "2222222-2222-2222-2222-222222222222"
$AccessSecret = "3333333333333333333333333333333333333333333"
Connecting to Azure Microsoft Graph API Using PowerShell
To use Microsoft Graph API from PowerShell, you don’t need to install any separate PowerShell modules (like Azure AD). You can interact with it using a built-in Invoke-RestMethod cmdlet.
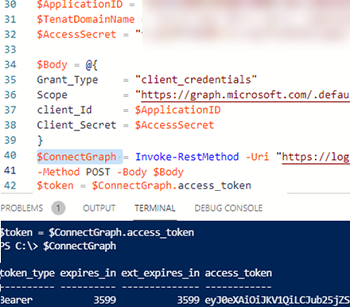
To connect to Graph API, you must get an access token. The following PowerShell script allows you to authenticate in your app and get a Microsoft Graph API access token.
$ApplicationID = "1111111-1111-1111-1111-11111111111"
$TenatDomainName = "2222222-2222-2222-2222-222222222222"
$AccessSecret = "3333333333333333333333333333333333333333333"
$Body = @{
Grant_Type = "client_credentials"
Scope = "https://graph.microsoft.com/.default"
client_Id = $ApplicationID
Client_Secret = $AccessSecret
}
$ConnectGraph = Invoke-RestMethod -Uri https://login.microsoftonline.com/$TenatDomainName/oauth2/v2.0/token -Method POST -Body $Body
$token = $ConnectGraph.access_token
Using the token, you can run different queries against your Azure tenant using GraphAPI.
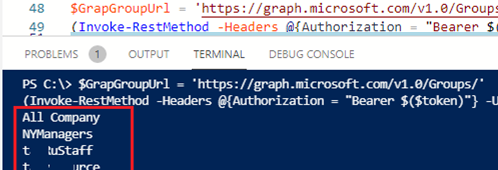
For example, the script below displays a list of groups in your Azure AD:
$GrapGroupUrl = 'https://graph.microsoft.com/v1.0/Groups/'
(Invoke-RestMethod -Headers @{Authorization = "Bearer $($token)"} -Uri $GrapGroupUrl -Method Get).value.displayName
You can display the date when an Azure AD group was created:
$GrapGroupUrl = 'https://graph.microsoft.com/v1.0/Groups/'
$Groups=(Invoke-RestMethod -Headers @{Authorization = "Bearer $($token)"} -Uri $GrapGroupUrl -Method Get).value
$Groups | select displayName,createdDateTime
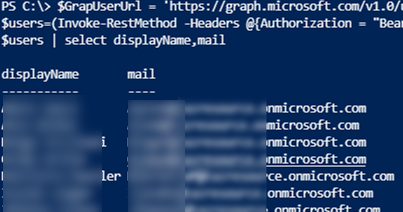
To show a user name, UPN, and email address:
$GrapUserUrl = 'https://graph.microsoft.com/v1.0/users'
$users=(Invoke-RestMethod -Headers @{Authorization = "Bearer $($token)"} -Uri $GrapUserUrl -Method Get).value
$users | select displayName,userprincipalname,mail
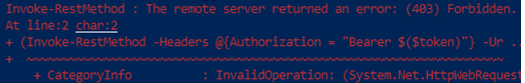
The remote server returned an error: (403) Forbidden.
In the examples above, we only read data from Azure AD using the GET method. But you can also use POST, PUT, PATCH, or DELETE methods to make changes. For instance, you can create a user in Azure AD, reset a password, change a description, etc.
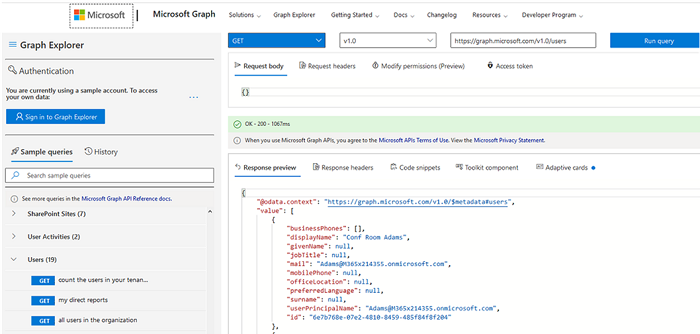
To view available Microsoft Graph API properties or methods in your browser, you can use Graph Explorer (https://developer.microsoft.com/en-us/graph/graph-explorer).
Install-Module Microsoft.Graph). But we showed that you can access Microsoft Graph directly from PowerShell.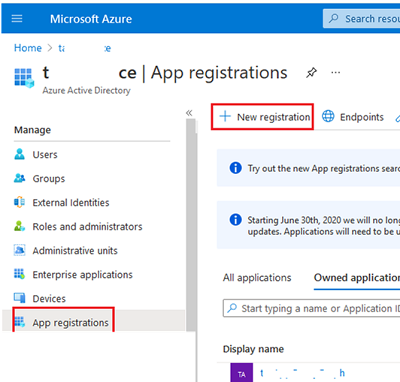
1 comment
Hello! Thank you for this article, it made it easy to set up the API in Azure. You referenced this guide in a previous article about checking read/unread email status in Exchange here: https://woshub.com/check-read-unread-email-status-exchange/
I did some tinkering around in MS Graph after authenticating and was able to find the isRead information in one of the GET queries, but was only able to run it for the messages in my own inbox. I also wasn’t able to figure out how to specify which email ID I wanted to run the query on. Is this a limitation of the API or is there something I’m missing? I’d much appreciate a follow up to that article if its possible to use Graph for the same purpose as you outlined with the Get-MessageTrackingLog command in PowerShell.
Thank you!