When you trying to run an exe, msi, bat, cmd or other executable type of files from a local drive or network folder in Windows, you can see this warning: “Open file — Security Warning”. In order to run the program, user must manually confirm the launch of such a file by clicking the Run button. This Windows security warning usually appears when you run an application file downloaded from the Internet, or executable file that is located on a network shared folder or mapped network drive.
- Windows Security Warning Then Launching Executable or Script
- How to Disable Open File Security Warning for Downloaded Files?
- Security Warning When Opening Files from the Network Share
- Open File Security Warnings When Using AppData Folder Redirection
- Disable Open File Security Warning for Specific File Types via GPO
Windows Security Warning Then Launching Executable or Script
Such Windows behavior is designed to protect your computer from running potentially dangerous executable files that have been downloaded from the Internet or received from other untrusted sources. This security warning appears on all versions of Windows (including Windows 10, 8.1, and 7).
If you install or run programs on a user’s computers in the background (through scheduler tasks, Group Policy logon scripts, SCCM scripts, etc.), this can cause problems. The fact is that in such cases the security warning window doesn’t appear in the user’s session. So, it becomes impossible to install or run such an application in a batch mode.
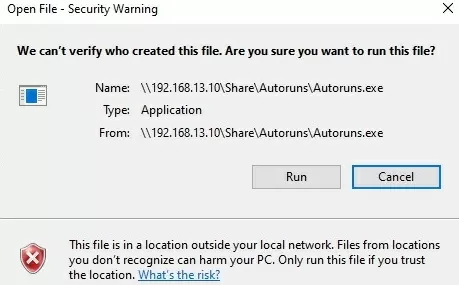
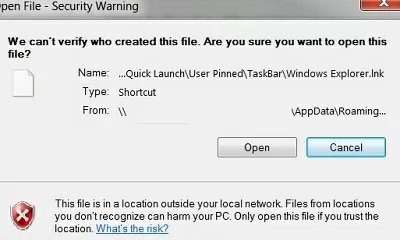
For example, when opening a file from a shared folder, the Windows security alert looks as follows:
Open File — Security Warning The Publisher could not be verified. Are you sure you want to run this software? We can’t verify who created this file. Are you sure you want to run this file? This file is in location outside your local network. Files from locations you don’t recognize can harm your PC. Only run this file if you trust the location.
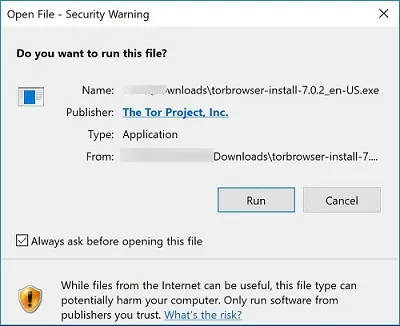
When running a file downloaded from the Internet from the local drive (or a network share mounted via net use), the text of the warning is a bit different:
Open File — Security Warning Do you want to run this file? While files from the Internet can be useful, this file type can potentially harm your computer. Only run software from publishers you trust.
If you uncheck the option “Always ask when opening this file”, then the next time you run this file, the Windows security window will not appear. But in this way, you will have to add programs to exceptions manually.
Let’s try to find out how to remove the security warnings when running executable or installation files on Windows (this guide is applicable for all Windows versions).
We offer several options on how to disable the security warning alert. Choose the suitable one depending on the necessary solution (in some cases you will have to combine the solutions).
How to Disable Open File Security Warning for Downloaded Files?
The executable files downloaded from the Internet are automatically marked as potentially dangerous (downloaded from an unsafe source). This feature is implemented with the help of the alternative NTFS file streams technology (Alternate Data Streams – ADS). To make it simple, let’s consider it to be a special file mark, which is automatically assigned to the downloaded file (see an article How does Windows know if a file was downloaded from the Internet). To remove this marker, you need to unblock this file. To do it:
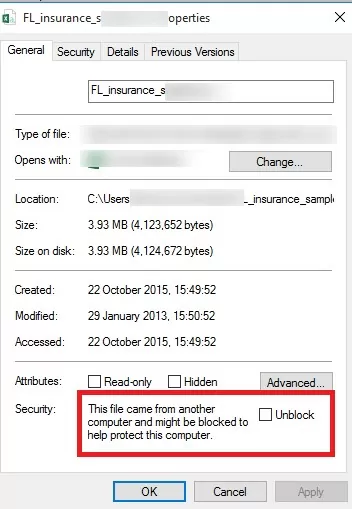
- Open the properties of the executable file;
- On the General tab click the button or tick the Unblock checkbox. If the file has been downloaded from the Internet, the following warning will be displayed next to the button (checkbox):
This file came from another computer and might be blocked to help protect this computer. - Save the changes by clicking OK button. After the file has been unblocked, it is run without the warning window (NTFS alternate data streams is removed).
The alternative NTFS data stream attribute Zone.Identifier can be reset using these two commands (a new file will be created):
move oldapp.exe > newapp
type newapp > oldapp.exe
Or with the help of the Sysinternal’s tool:
streams.exe
Also, you can unblock file using PowerShell:
Unblock-File -Path C:\Downloads\somefile.exe
You can disable this warning only for files downloaded using the browser by disabling the setting of the Zone.Identifier attribute:
- For Google Chrome and IE, you need to create such a registry parameter
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments]
“SaveZoneInformation”=dword:00000001 - For Mozilla Firefox: open the settings page
about:config, and change the value ofbrowser.download.saveZoneInformationto false.
In Windows, you can completely disable applying zone information to files downloaded from the Internet using the special GPO parameter Do not preserve zone information in file attachment (User Configuration -> Administrative Templates -> Windows Components -> Attachment Manager).
Security Warning When Opening Files from the Network Share
The warning window may appear when the program is launched from a shared network folder using the UNC path. This problem typically occurs for corporate users when accessing resources in another AD domain or by IP address. In this case, it’s easiest to add the name and/or IP address of the server hosting the executable file to the Local Intranet zone in the Internet Explorer settings. This will indicate that the resource is trusted. To do it:
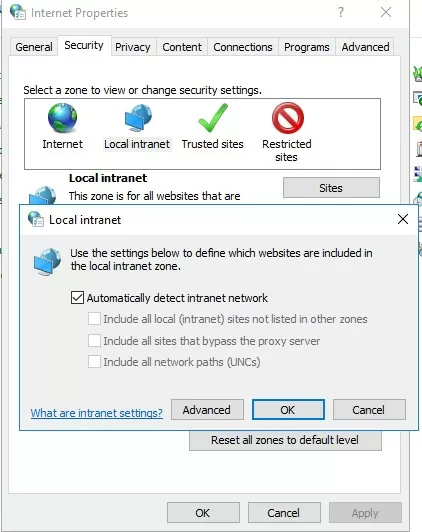
- Go to Control Panel → Internet Option;
- Security tab;
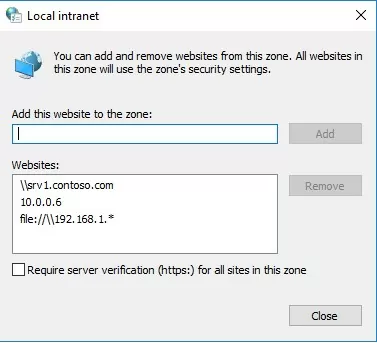
- Open Local Intranet → Sites → Advanced;
- In the next window, add a name and/or an IP address of a server. For example,
\\10.0.0.6,\\srv.contoso.comor\\127.0.0.1\for a local computer. You can use a wildcard character. For example, you can add all IP addresses of your local network to the Local Intranet zone using the following line:file: //192.168.1.*. .
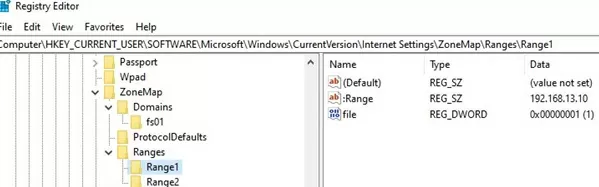
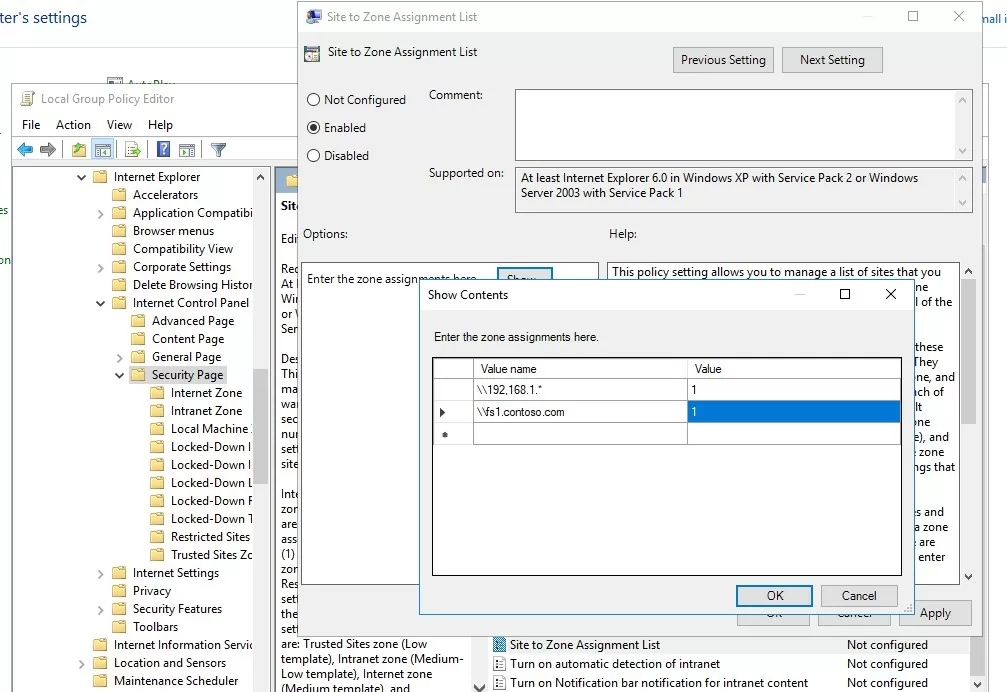
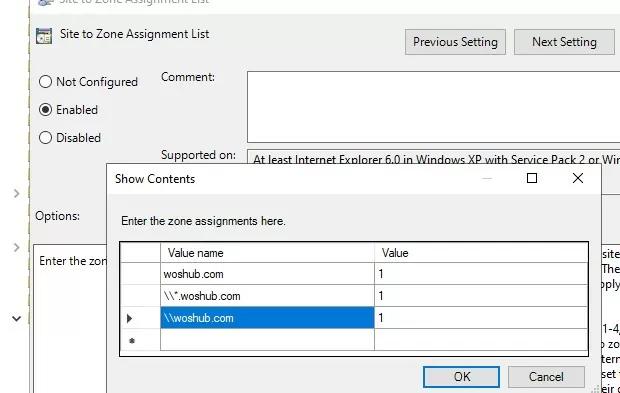
Also you can add the IP addresses and DNS names of trusted domains and hosts to the Local Intranet zone using GPO. Open the Local (gpedit.msc) or the Domain Group Policy Editor (gpmc.msc). Enable the policy Compute Configuration -> Administrative Templates ->Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page -> Site to Zone Assignment List. In the policy settings, you must specify a list of trusted hosts and/or domains in the following format:
- Server (host) name (e.g.,
file://server_name,\\server_name,server_nameorIP) - Zone number (1 for the Local Intranet Zone)
If the security warning window appears when launching programs from a mapped network drive, add a drive letter (for example, U:\) or UNC path to the local Intranet zone.
Save the policy changes and refresh the GPO settings on the client (gpupdate /force). The warning should stop appearing when opening executable files from the specified shared network folders.
In addition, you can enable the following settings under the GPO section User Configuration -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page. This is the best option for domain users:
- Intranet Sites: Include all local (intranet) sites not listed in other zones
- Intranet Sites: Include all network paths (UNCs)
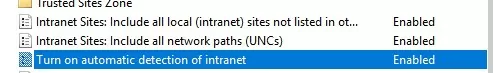
- Turn on automatic detection of intranet
Open File Security Warnings When Using AppData Folder Redirection
If you are using AppData folder redirection (in the profile roaming scenarios), users may encounter the “Open File – Security Warning” window when launching application shortcuts from the profile folders.
In this case, you need to add your server (or the entire domain) where roaming profiles are stored to the IE trusted zone.
Use the GPO option User Configuration -> Policies -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page -> Site to Zone Assignment List. Add server (domain) name with value 1.
Disable Open File Security Warning for Specific File Types via GPO
In some cases, it is advisable to completely disable the appearance of the security warnings for certain file types (extensions) through Group Policies. Although, of course, this is not very secure, because the user can accidentally run something malicious.
To do it, in the GPO Editor go to: User Configuration -> Administrative Templates -> Windows Components -> Attachment Manager.
- Enable the policy Do not preserve zone information in file attachments. All the downloaded files will be run without the warning on all computers.
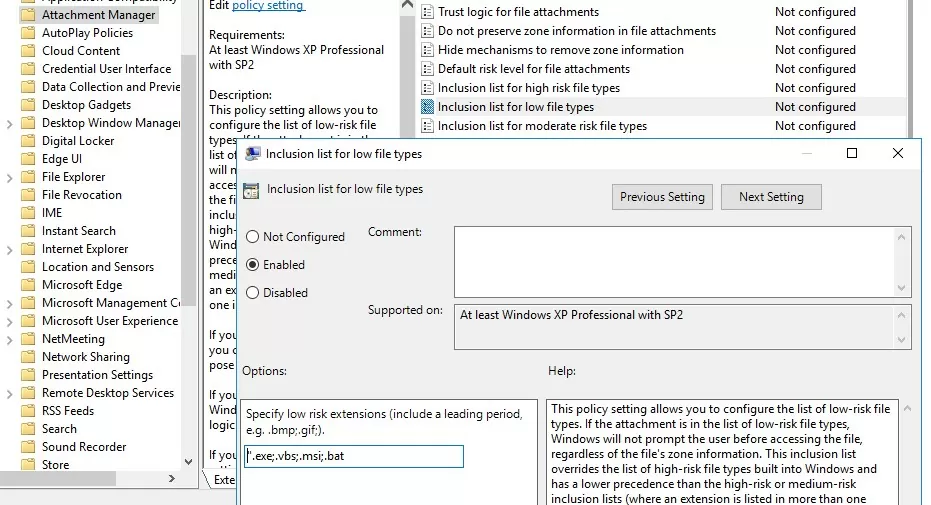
- Enable the policy Inclusion list for low file types, and in its settings specify the list of file extensions that you would allow to run, e.g.,
.exe; .vbs; .msi. Windows will ignore the alternate data steam markers on the files with these extensions and run them without the warning.Note. This policy adds file extensions to the LowRiskFileTypes registry parameter:[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations]"LowRiskFileTypes"=".exe;.vbs;.msi;.bat;"
gpedit.msc) is missing on Windows 10 Home edition. But there is a workaround to install it.Save the policy, assign it to the target OU and apply it to clients by running on them the gpupdate /force command.
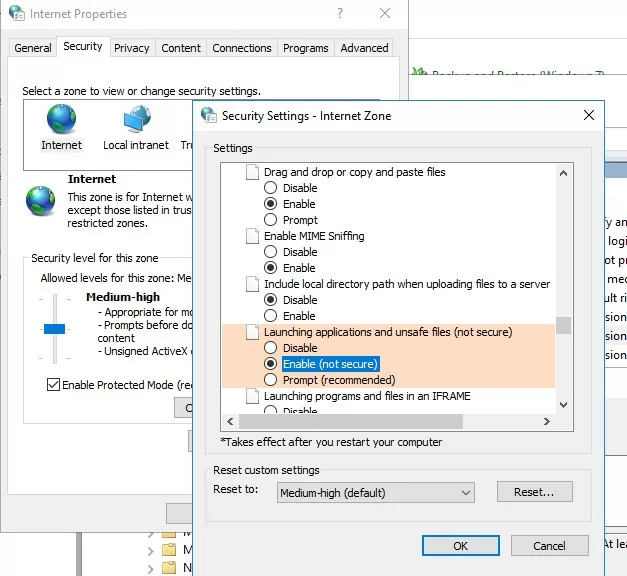
Now, the warning should stop appearing when opening executable files with the specified extensions with any information in the Zone.Identifier stream. You can also allow Internet Explorer to run any files in the Internet Explorer properties (Security -> Internet -> Custom level -> Miscellaneous -> Launching applications and unsafe files (not secure), but it is very risky.
You can completely disable the “Open File – Security Warning” window for unsafe files using the GPO option Turn off the Security Settings Check feature (located in the section Computer Configuration -> Administrative Templates -> Windows Components -> Internet Explorer).
Or you can allow any file to run without displaying the “Open File Security Warning” using the following commands:
REG ADD "HKLM\SOFTWARE\Policies\Microsoft\Internet Explorer\Security" /V "DisableSecuritySettingsCheck" /T "REG_DWORD" /D "00000001" /F
REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3" /V "1806" /T "REG_DWORD" /D "00000000" /F
REG ADD "HKLM\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3" /V "1806" /T "REG_DWORD" /D "00000000" /F
5 comments
There is no unblock option 🙁
Thank you for explaining the “fix” for this…worked fine for me using Windows 7 Pro. It just started after the last Windows update a couple of days ago.
Not an issue any more…”UNBLOCKED”…!!!
Thanks again and have a great day…!
Works very well, thanks!
Thank you.
Best regards. Aleksej
As usual, incredibly useful information. Just enabling the policy “Turn on automatic detection of intranet” as suggested removed the pop up warnings from my domain environment.
What made this problem additionally frustrating, is that when attempting to install applications stored on a file server using the Start-Process cmdlet via Powershell remoting to a target workstation, the command just hangs infinitely because of this security warning!
Thanks again!